Risk assessment method, device and equipment and storage medium
A technology of risk assessment and equipment, applied in the field of network security, can solve the problem that the zero trust model does not give dynamic judgment, and achieve the effect of risk assessment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
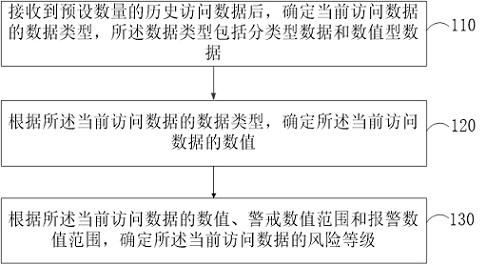
[0045] figure 1 It is a flow chart of a risk assessment method provided by Embodiment 1 of the present invention. This embodiment of the present invention is applicable to the situation where the risk level of the currently accessed data needs to be determined. The method can be executed by a computer device, and specifically includes the following steps:
[0046] Step 110, after receiving a preset amount of historical access data, determine the data type of the current access data, where the data type includes categorical data and numerical data.
[0047] In the existing technology, the risk level of the access data can be determined based on the topological relationship, but the existing technology cannot determine the risk level of all the access data, which may easily cause the omission of the access data, so a zero-trust model is proposed to dynamically determine the risk level The method replaces the risk level determination method in the prior art, and realizes the dete...
Embodiment 2
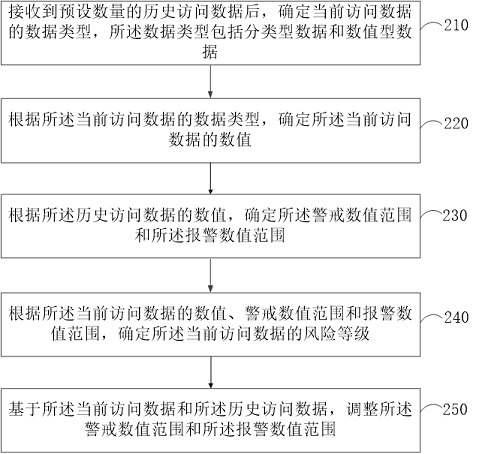
[0066] figure 2 It is a flow chart of a risk assessment method provided by Embodiment 2 of the present invention, which is embodied on the basis of the above-mentioned embodiments. In an embodiment of the present invention, the method may also include:
[0067] Step 210, after receiving a preset amount of historical access data, determine the data type of the current access data, where the data type includes categorical data and numerical data.
[0068] After the zero trust model receives a preset amount of historical access data, the method and specific steps of determining the data type of the current access data have been described in detail in Embodiment 1, and will not be repeated here.
[0069] Step 220. Determine the value of the currently accessed data according to the data type of the currently accessed data.
[0070] The method and specific steps for determining the value of the currently accessed data have been described in detail in Embodiment 1, and will not be...
Embodiment 3
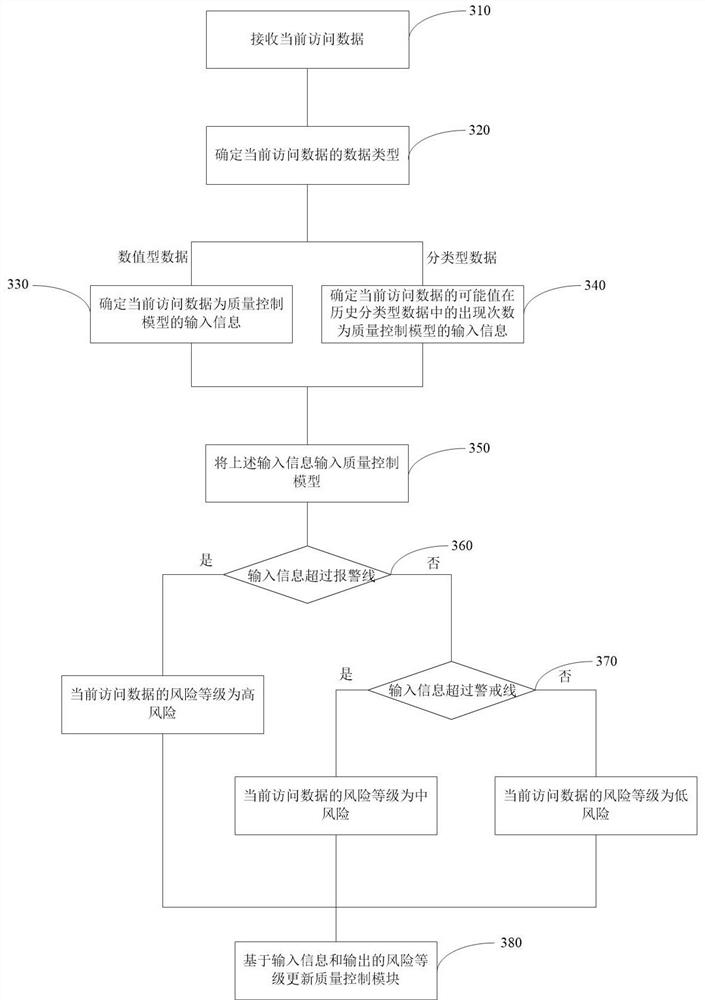
[0113] Figure 4 The structure diagram of a risk assessment device provided by Embodiment 3 of the present invention is suitable for realizing risk assessment of currently accessed data when the risk level of currently accessed data needs to be determined. The device can be realized by software and / or hardware, and is generally integrated in computer equipment.
[0114] Such as Figure 4 As shown, the device includes:
[0115] The first determination module 410 is configured to determine the data type of the current access data after receiving a preset amount of historical access data, and the data type includes categorical data and numerical data.
[0116] The second determining module 420 is configured to determine the value of the currently accessed data according to the data type of the currently accessed data.
[0117] The third determination module 430 is configured to determine the risk level of the currently accessed data according to the value of the currently acce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com