Secure transmission device for calculating checksum according to classification
A secure transmission and Ethernet technology, applied in the field of secure transmission devices, can solve the problems of lack of theoretical training and experience in dealing with system attacks, forged identity attacks, illegal access attacks, and tampering of important enterprise data. Security, the effect of solving remote disaster recovery and real-time hot backup
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] A kind of secure transmission device for calculating the checksum according to the classification of the present embodiment comprises the following steps:
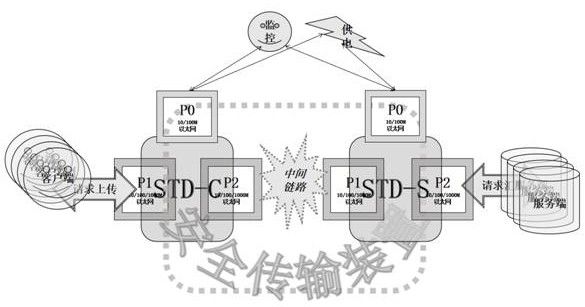
[0040] S1: Before use, directly connect the Ethernet port P0 of the safety transmission device STD-C and the safety transmission device STD-S to the management platform. The Ethernet port P0 uses a predefined management IP address and port, and the administrator sends Management command, when the Ethernet network port P0 receives a configuration message in the agreed format from the administrator, it will be configured;
[0041] S2: Define the network where the client cluster resides as network C, which connects to the Ethernet port P1 of the secure transmission device STD-C, defines the network where the server cluster resides as network S, and connects network S to the secure transmission device STD-S Ethernet network port P2;
[0042] S3: The messages sent by any client are grouped according to the source IP add...
Embodiment 2
[0050] The hardware of the secure transmission device STD in this embodiment can be any one of FPGA, ASIC, CPLD, DSP, single-chip microcomputer, ARM chip, RISC-V chip, custom chip, PC system and mobile phone system.
[0051] In this embodiment, the Ethernet network port P1 and the Ethernet network port P2 adopt any one of 10 Gigabit, Gigabit and 100M network ports, and the Ethernet network port P0 adopts a 100M network port.
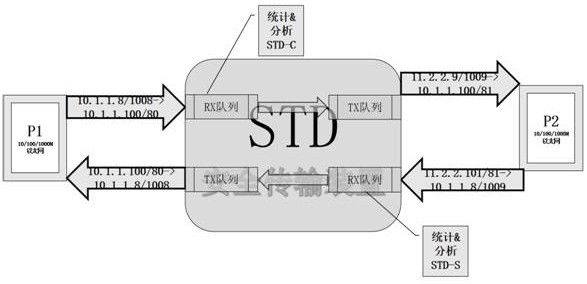
[0052] The secure transmission device STD-C of this embodiment is at the client node, and receives the requests gathered by each client at a high speed, and counts and generates a specific log CMSG, and the secure transmission device STD-S is at the server node, and receives and sends to Collect requests from each server, and count and generate specific log SMSG, and submit CMSG and SMSG to the monitoring platform to check whether the real-time reported CMSG and SMSG are consistent.
[0053] The secure transmission device STD-C of this embodiment is conn...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com