Agile image encryption method based on deep learning
A technology of deep learning and encryption method, which is applied in the field of image information security, can solve problems such as system inconvenience, and achieve the effect of enhancing security and being convenient and quick to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
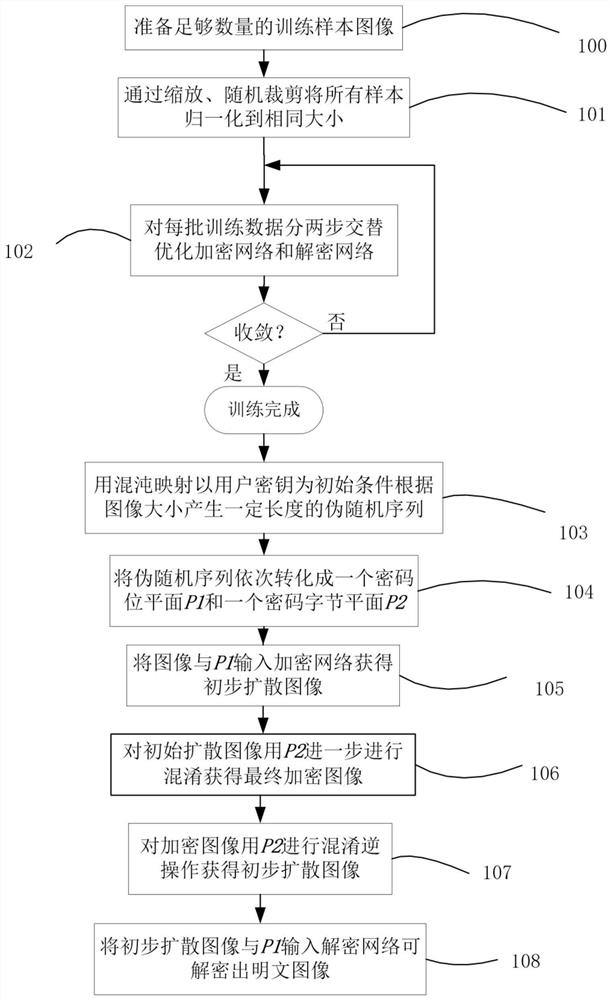
[0074] (1) Prepare training data.
[0075] Prepare a sufficient number of training samples (the training set data can be collected and created by yourself or downloaded from the Internet to some public image data sets, such as ImageNet, etc.), and all images are converted into grayscale images, and all images are normalized to a size of 256×256 , the normalization method is as follows: For images whose short side is greater than 256, directly perform random cropping; for images whose short side is less than 256, first enlarge the image proportionally until the short side is 256, and then perform random cropping.
[0076] (2) Joint training encryption network and decryption network
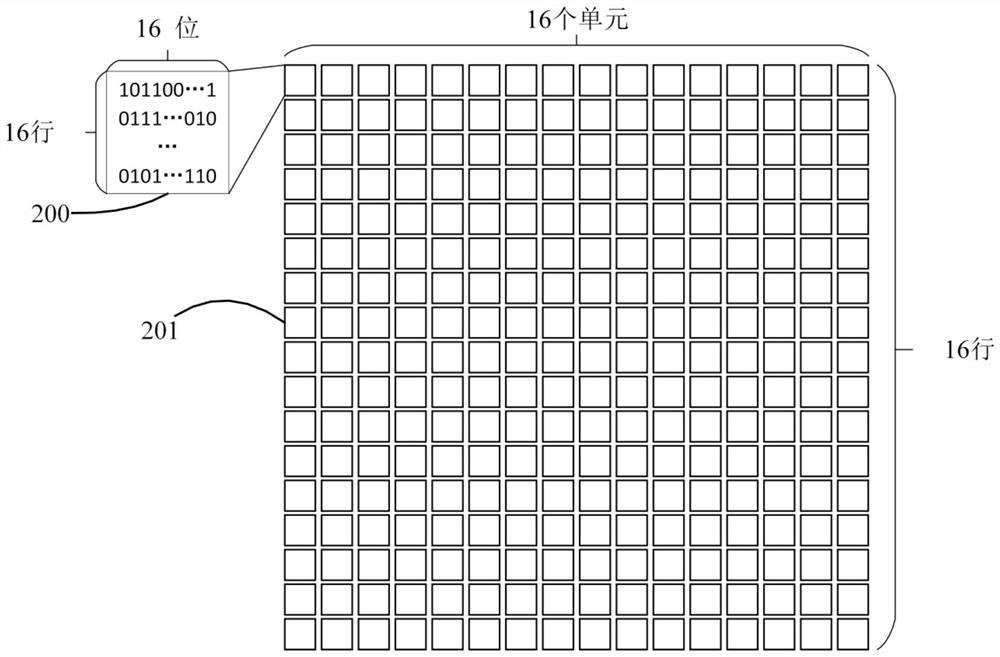
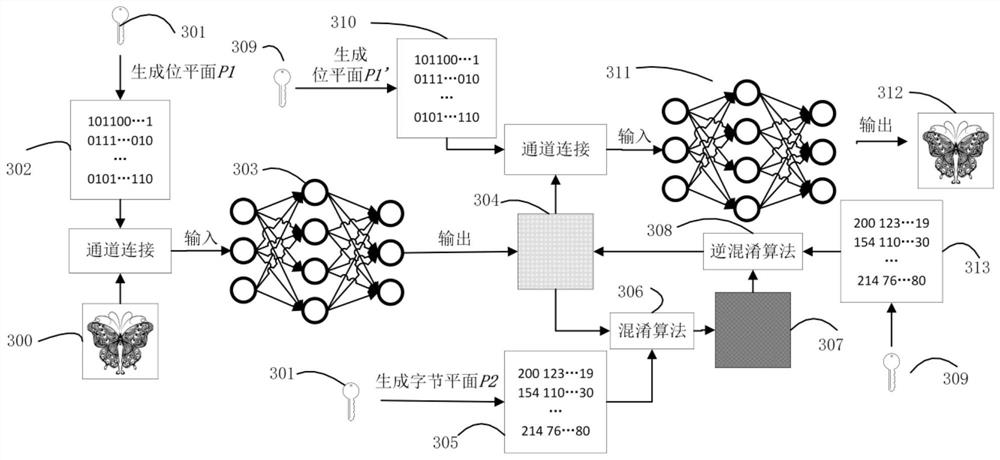
[0077] Input the prepared training data into the encryption network and the decryption network in batches for training. For each batch of data, first randomly generate two different keys k≠k', and use the key as a seed to generate a pseudo key containing 32 integers. Random sequence, each integer ...
Embodiment 2
[0083] (1) Prepare training data.
[0084] Prepare a sufficient number of training samples (the training set data can be collected and created by yourself or downloaded from the Internet to some public image data sets, such as ImageNet, etc.), and all images are converted into grayscale images, and all images are normalized to a size of 256×256 , the normalization method is as follows: For images whose short side is greater than 256, directly perform random cropping; for images whose short side is less than 256, first enlarge the image proportionally until the short side is 256, and then perform random cropping.
[0085] (2) Joint training encryption network and decryption network
[0086] Input the prepared training data into the encryption network and the decryption network in batches for training. For each batch of data, first randomly generate two different keys k≠k', and use the key as a seed to generate a pseudo key containing 32 integers. Random sequence, each integer ...
Embodiment 3
[0092] (1) Prepare training data.
[0093] Prepare a sufficient number of training samples (the training set data can be collected and created by yourself or downloaded from the Internet to some public image data sets, such as ImageNet, etc.), and all images are converted into grayscale images, and all images are normalized to a size of 512×512 , the normalization method is as follows: for images whose short side is larger than 512, directly perform random cropping; for images whose short side is smaller than 512, first enlarge the image proportionally until the short side is 512, and then perform random cropping.
[0094] (2) Joint training encryption network and decryption network
[0095] Input the prepared training data into the encryption network and the decryption network in batches for training. For each batch of data, first randomly generate two different keys k≠k', and use the key as a seed to generate a pseudo key containing 32 integers. Random sequence, each intege...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com