Anti-intrusion method for low-voltage power line carrier communication system
A low-voltage power line and carrier communication technology, which is applied in transmission systems, digital transmission systems, and security communication devices, can solve problems such as limiting the accuracy of intrusion detection and calculation efficiency, the inability to guarantee the security of low-voltage power line communication networks, and large data dimensions. Achieve the effects of improving accuracy and computing efficiency, improving the probability of anti-intrusion and the accuracy of intrusion detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
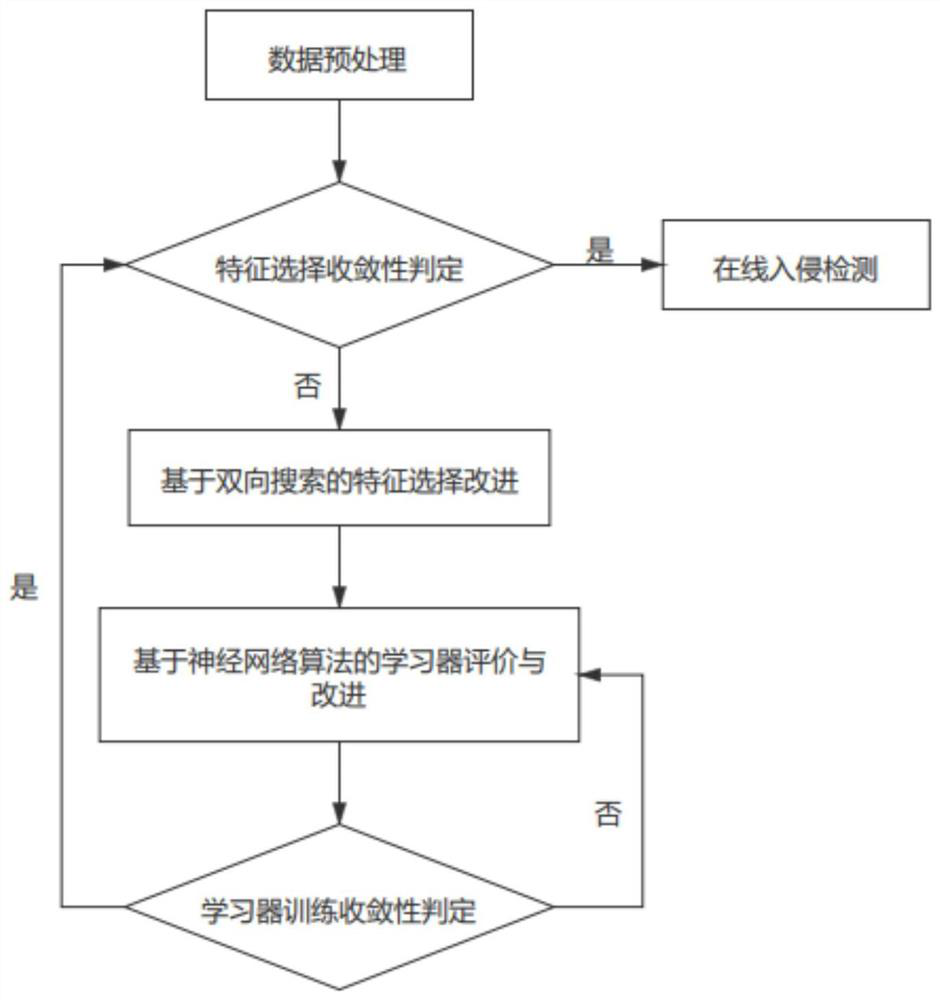
[0042] refer to figure 1 , the present invention provides a low-voltage power line carrier communication system anti-intrusion method, comprising:
[0043] data preprocessing;
[0044] Judging the convergence of feature selection, if it is judged to be convergent, it will enter the online intrusion detection, otherwise, it will enter the next step;
[0045] Improved feature selection based on bidirectional search;
[0046]Improvement of learner based on neural network algorithm;
[0047] The learner trains the convergence judgment. If it is judged to be convergent, it will enter the feature selection convergence judgment. Otherwise, repeat the previous step.
[0048] Data preprocessing includes: data standardization processing on unknown data, one hot preprocessing, and conversion of a single piece of unknown data from 1×41 to 1×122.
[0049] Improvements to learners based on neural network algorithms include:
[0050] Train the CNN-Focal classification model through supe...
Embodiment 2
[0071] refer to figure 1 , the present invention provides a low-voltage power line carrier communication system anti-intrusion method, comprising:
[0072] Data preprocessing, data standardization processing and one hot preprocessing for unknown data, converting single unknown data from 1×41 to 1×122;
[0073] Judging the convergence of feature selection, if it is judged to be convergent, it will enter the online intrusion detection, otherwise, it will enter the next step;
[0074] Improved feature selection based on bidirectional search;
[0075] Improvements to learners based on neural network algorithms:
[0076] (1) Train the CNN-Focal classification model through supervised learning
[0077] The CNN-Focal classification model obtained through training includes an input layer, a convolutional layer, a Dropout layer, a Max-pooling layer, a fully connected layer, and a Softmax layer. Among them, the first layer of the CNN-Focal classification model is the input layer, and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com