Single-time multi-vulnerability code detection method and system
A technology of vulnerability detection and code detection, applied in the field of information security, to achieve wide applicability, improve security level, and high feasibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
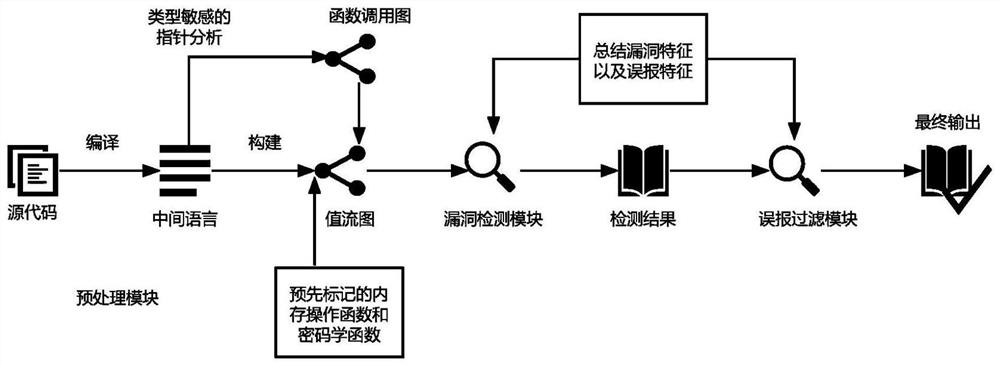
[0025] Such as figure 1 As shown, it is an automatic code vulnerability detection system involved in this embodiment, which is implemented on the framework of LLVM version 12.0. The system includes: a preprocessing module, a vulnerability detection module, and a false positive filtering module, wherein: the preprocessing module utilizes LLVM to compile The tool converts the C language source code of the code to be tested into the LLVM intermediate language, performs type-sensitive pointer analysis on it, and constructs a function call graph of the entire project; using the function call graph and pre-marked memory operation functions and cryptographic functions, from the to-be-tested The value flow graph of memory objects and global constants is built in the LLVM intermediate language of the detection code; the vulnerability detection module constructs a code vulnerability detection mode by summarizing the characteristics of different types of code vulnerabilities, and then sel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com