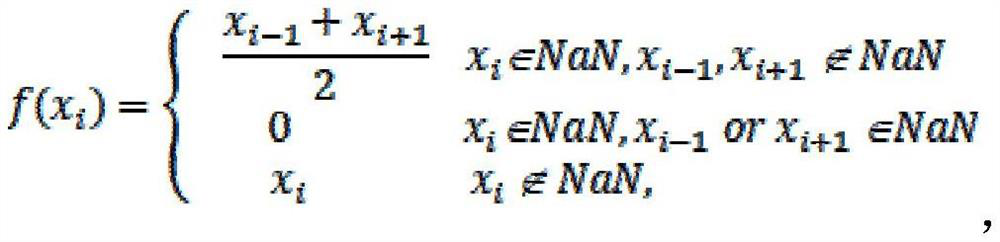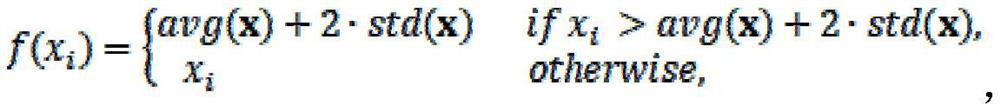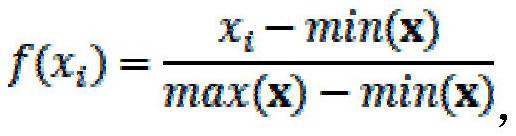Smart power grid privacy protection and electricity stealing detection method based on block chain
A smart grid and privacy protection technology, applied in digital data protection, neural learning methods, biological neural network models, etc., can solve problems such as damage, smart meters are vulnerable to attacks, and economic losses of power companies and legitimate users, so as to ensure data security The effect of completeness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0103] The present invention will be described in further detail below through examples, and the following examples are explanations of the present invention and the present invention is not limited to the following examples.
[0104] Embodiments of the invention include:
[0105] (1) The lightweight data aggregation method based on the consortium blockchain satisfies resource-constrained smart meters in practical applications, and realizes privacy protection and integrity protection in smart grid communications.
[0106] (2) The electricity theft detection method based on the convolutional neural network, using the safe, efficient, and traceable user group data provided in (1), establishes a model to analyze the electricity consumption data and detect the user's electricity consumption behavior, and realizes the detection of theft. Discovery of electrical behavior and secure transfer of results.
[0107] (3) Based on the blockchain-based electricity theft behavior processing...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com