Web application program vulnerability attack detection method, server, electronic equipment and storage medium
A technology for attack detection and application programs, applied in the field of network security, can solve problems such as difficult identification and detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
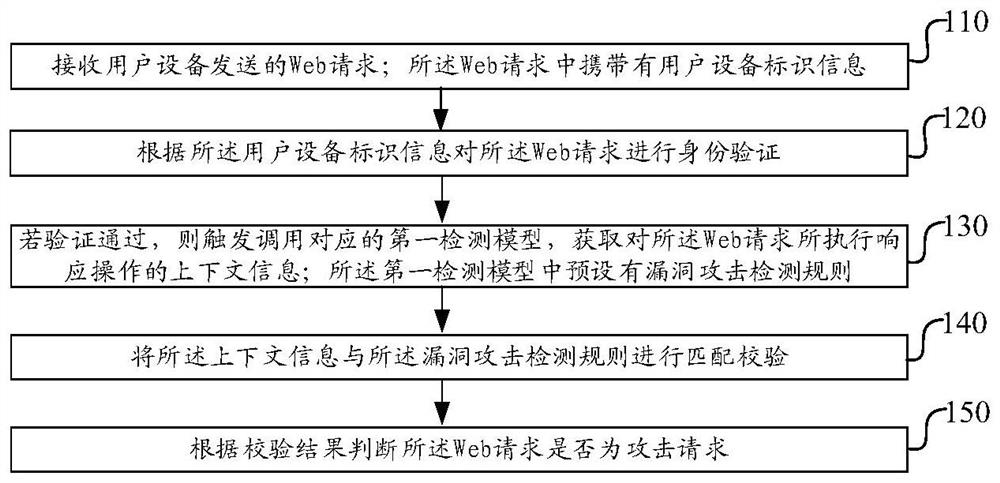
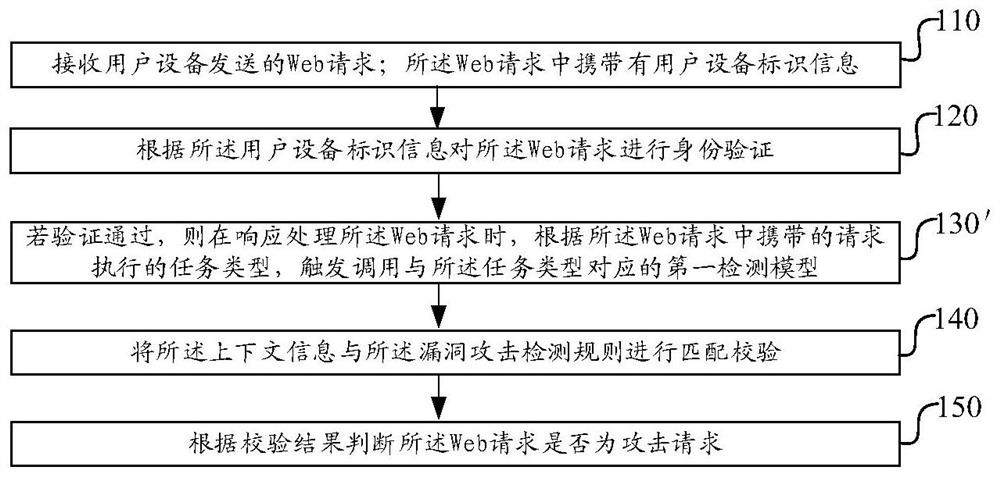
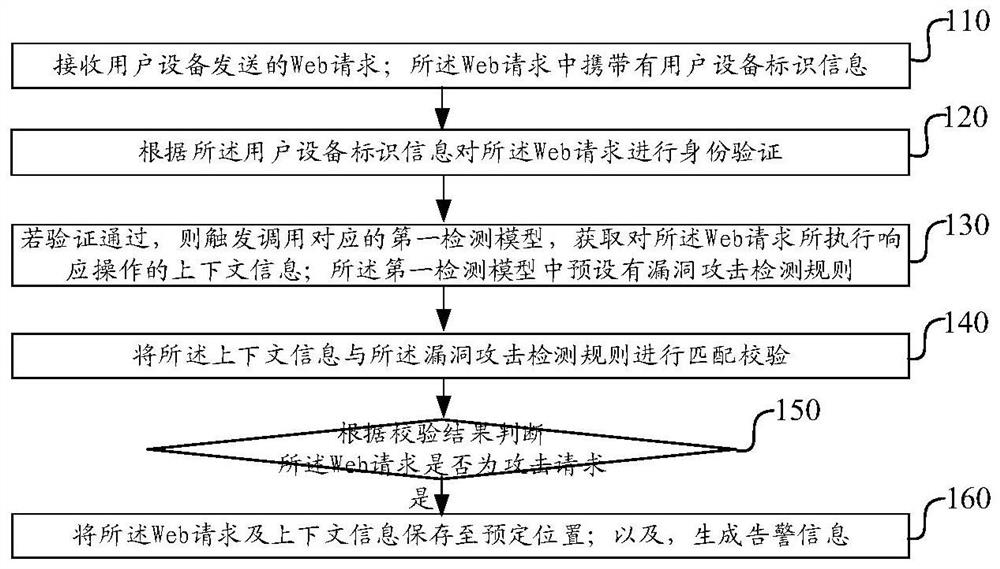
[0084] Figure 5 It is a schematic block diagram of the architecture of an embodiment of the Web application server of the present invention, see Figure 5 As shown, the server includes a host, and the web application described in any one of Embodiment 1 is installed on the host, and the first detection model is embedded in the web application, when a user sends a web message to the server When requested, the web application program is used to execute the vulnerability attack detection method described in any one of the first embodiment.
[0085] The server of this embodiment can be used to execute figure 1 The implementation principle and technical effect of the technical solution of the shown method embodiment and the server of this embodiment are similar to those of Embodiment 1, and will not be repeated here, and can be referred to each other.
Embodiment 3
[0087] Image 6 It is a schematic block diagram of the structure of an embodiment of the honeypot server of the present invention. The present invention also provides a server for capturing network attackers, including a host, deploying the application program provided in this embodiment as a honeypot application and deploying it on the host The predetermined location, the application program can be triggered to collect user (including attacker) information to understand the attacker's attack method. After the attacker triggers the successful attack event, the attacker's personal fingerprint (here refers to the identification information used to identify the attacker's identity and / or behavior, not the biological fingerprint) is collected through the honeypot collection program to achieve the purpose of countermeasures and Do not accidentally injure normal users.
[0088] Specifically, a honeypot application program is deployed on the host, and a honeypot collection program i...
Embodiment 4
[0091] An embodiment of the present invention also provides an electronic device, including one or more processors; a memory; one or more executable programs are stored in the memory, and the one or more processors read the stored program in the memory The executable program code is used to run the program corresponding to the executable program code, so as to execute the method described in any one of the first embodiment.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com