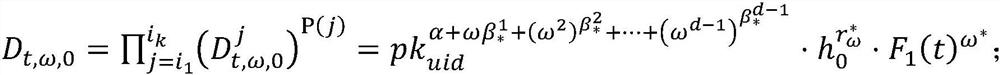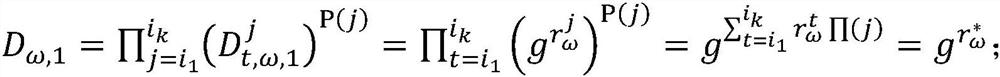Internet of Things client privacy protection authentication method based on edge computing
An edge computing and authentication method technology, applied in the field of information security, can solve problems affecting system security, unaffordable, and no longer able to obtain specific identity information of signers, so as to ensure key application and management, and improve efficiency.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
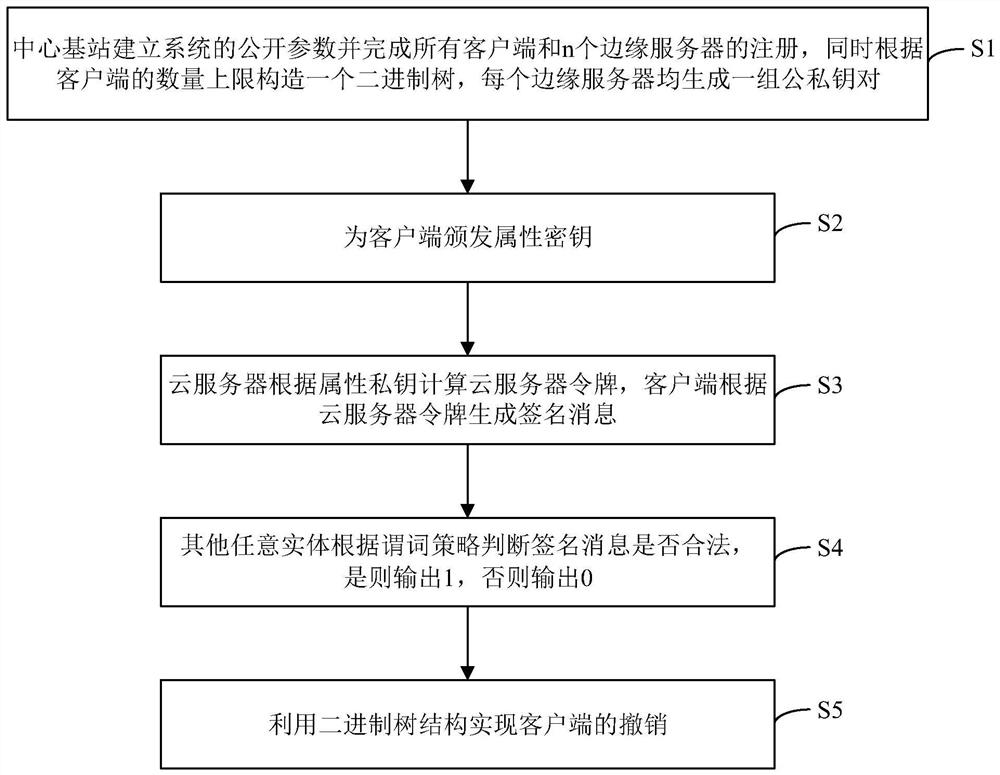
[0064] Below in conjunction with the drawings, preferred embodiments of the present invention are given and described in detail.
[0065] The entities involved in the embodiments of the present invention include:
[0066] Central base station (BS): as the global trusted certificate center of the system, it initializes the system and accepts the registration of legal clients and edge servers;
[0067] Edge Server (ES): Multiple Edge Servers manage the same set of system attributes and issue attribute key components for each IoT client;
[0068] Internet of Things client: only a client with a legal attribute key can construct a signature that satisfies the corresponding predicate policy, and signature verification does not require any additional information, and any client entity can complete signature verification.
[0069] Such asfigure 1 As shown, the embodiment of the present invention provides a privacy protection authentication method for the Internet of Things client bas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com