IDS system for monitoring and analysis based on real-time network flow and detection method
A real-time network and detection method technology, applied in the field of network security, can solve problems such as high maintenance costs, insufficient attention to network security, and inability to solve the target, and achieve the effect of improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
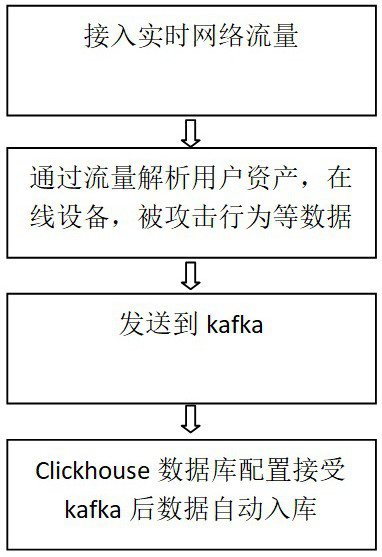
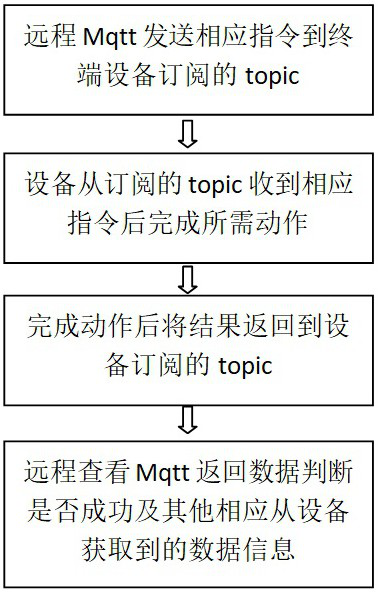
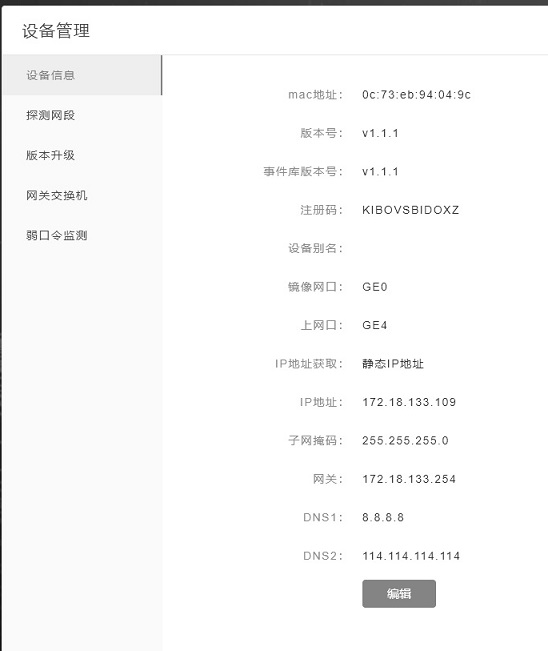
[0059] Threat-aware device endpoints:
[0060] A switch equipped with a linux system is used for installing and using related functions and programs of the present invention. The main procedures for realizing the functions are as follows:
[0061] (1) Monitoring terminal running program:
[0062] Watchdog, that is, "watchdog", can automatically restart the device when the terminal device is abnormal (such as system crash, etc.), so as to protect the normal operation of the intrusion detection program.
[0063] Linux kernel specific modules communicate with userspace via character devices. Once the user space program opens the character device, it will cause a 1-minute timer to be started in the kernel. After that, the user space program needs to ensure that data is written to the device within 1 minute, and each write operation will cause the timer to be reset. device.
[0064] If the user space program has no write operation within 1 minute, the expiration of the timer wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com