User behavior anomaly detection method and system of embedded tense
An anomaly detection and behavior technology, applied in transmission systems, file systems, file system functions, etc., can solve the problem of high false positive rate and false negative rate of abnormal user behavior detection, and achieve a high false positive rate and high false negative rate. , the effect of improving accuracy, improving accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
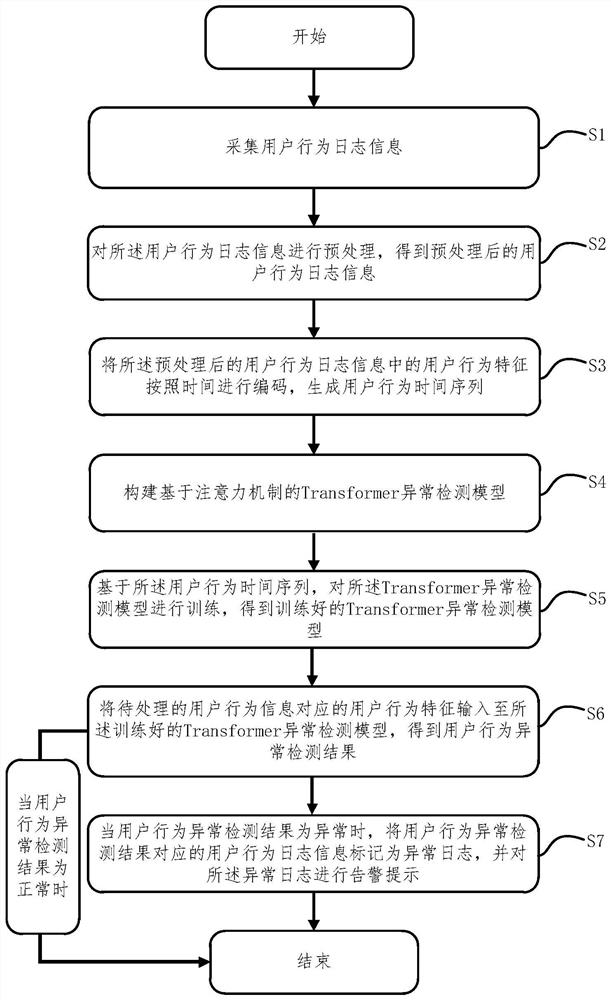
[0057] Such as figure 2 and Figure 4 As shown, the present embodiment provides a temporal-embedded user behavior anomaly detection method, which embeds temporal information into user behavior, and applies the Transformer anomaly detection model based on the attention mechanism for anomaly detection, specifically including the following steps :
[0058] Step S1, collecting user behavior log information.
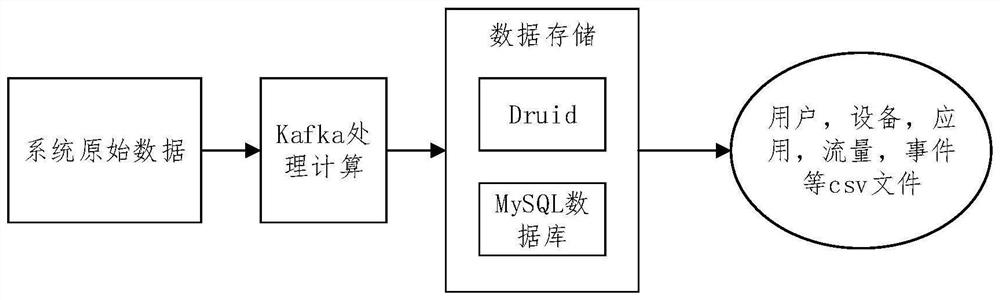
[0059] Such as image 3 As shown, collecting user behavior log information specifically includes the following steps:
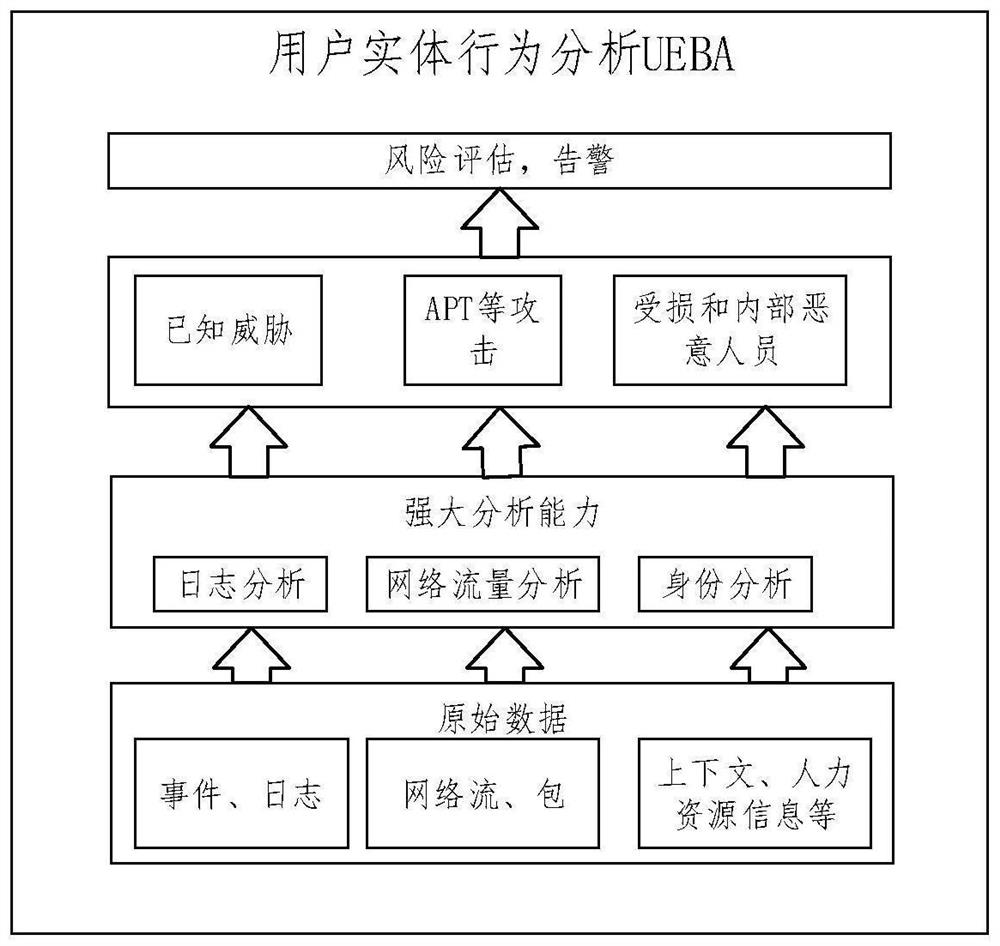
[0060] Step S1.1, use Kafka software to process and calculate the system raw data, and generate user behavior log information. Such as figure 1 As shown, the raw data of the system includes terminals and applications accessed by users, based on data such as events, logs, network flows, context information, and human resource information.
[0061] Step S1.2, using the Druid database to pre-aggregate the user behavior log information, build a query inde...
Embodiment 2
[0084] Such as Figure 5 As shown, this embodiment provides a temporally embedded user behavior abnormality detection system, the functions of each module and unit of the system are the same as the steps of the method in Embodiment 1 and correspond one-to-one, and the system specifically includes:
[0085] The user behavior log information collection module M1 is used to collect user behavior log information.
[0086] The user behavior log information collection module M1 specifically includes:
[0087] The user behavior log information generation unit M1-1 is used to use Kafka software to process and calculate the original data of the system to generate user behavior log information;
[0088] The user behavior log information storage unit M1-2 is used to pre-aggregate the user behavior log information using the Druid database, build a query index, and store it in the MySQL database.
[0089] The user behavior log information preprocessing module M2 is configured to preproce...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com