End-side cloud architecture-based distributed federated learning security defense method and application
A technology of security defense and cloud architecture, which is applied in the field of information security and can solve problems such as low overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
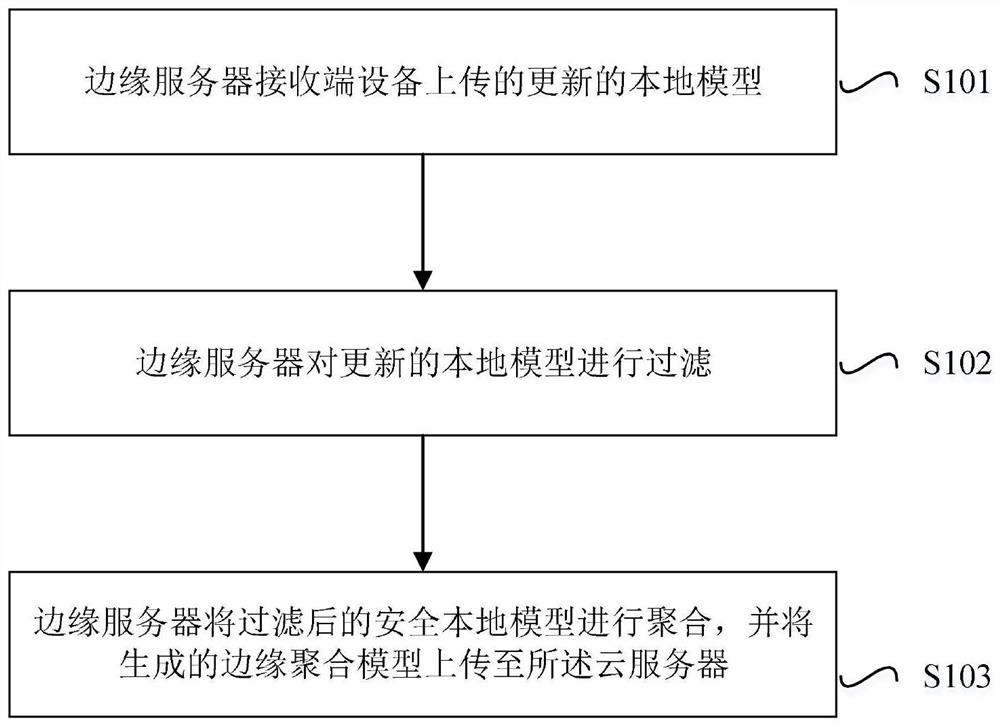
[0041] Such as Figure 1 to Figure 3 As shown, the security defense method of distributed federated learning based on the device-edge-cloud architecture in an embodiment of the present invention is introduced, and the method includes the following steps.
[0042] In step S101, the edge server receives the updated local model uploaded by the end device.
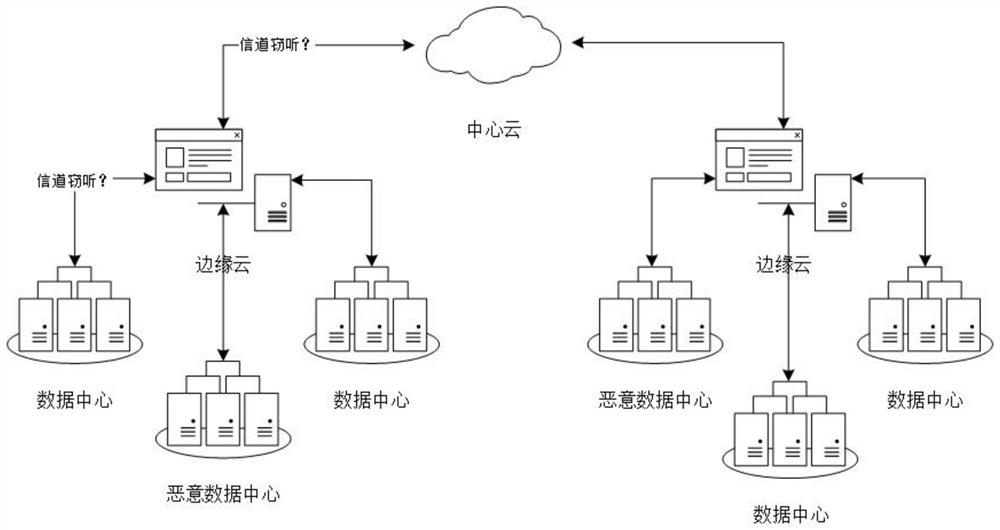
[0043] Such as figure 2 As shown in the figure, determine the end devices (data centers) under the jurisdiction of each edge server (edge cloud), partition the end devices with similar geographical distribution, and deploy edge servers for jurisdiction to provide computing and cache resources. The cloud server (central cloud) initializes the global model and sends it to each edge server, and then the edge server sends it to the corresponding bottom-end device. The end device uses private data to train the global model, calculates the updated local model through the stochastic gradient descent method, and uploads the updat...
Embodiment 2
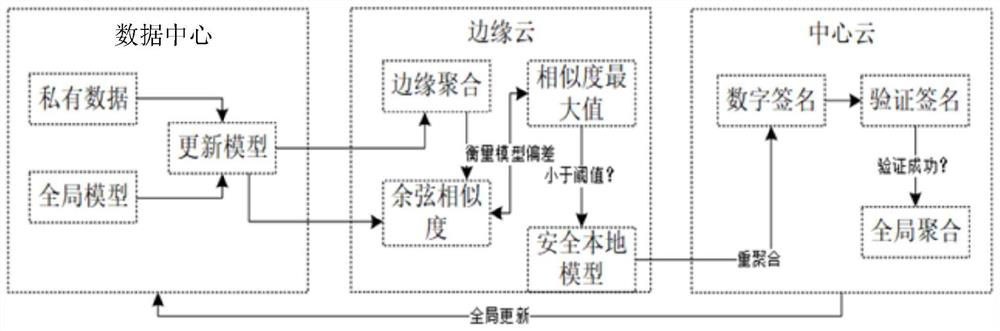
[0055] Such as Figure 4 As shown, the security defense method of distributed federated learning based on the device-edge-cloud architecture in an embodiment of the present invention is introduced, and the method includes the following steps.
[0056] In step S201, the cloud server initializes the global model and sends the global model to the edge server.
[0057] In step S202, the cloud server verifies the digital signature of the edge aggregation model uploaded by the edge server, and performs global aggregation on the edge aggregation model to obtain an updated global model.
[0058] After the cloud server verifies the signature, the malicious model that fails the verification is excluded, and the edge aggregation model that is successfully verified and safe is aggregated globally to update the global model.
[0059] Through the signature verification algorithm, verify whether the signature corresponds to the message, because the hash encryption algorithm has two basic ch...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com