Image self-authentication method based on hash function and information hiding
A technology of information hiding and hash function, which is applied in the direction of image data processing, image data processing, encryption device with shift register/memory, etc. It can solve the problems of being easily obtained by illegal users and the security of watermark information cannot be obtained well Guarantee and other issues, achieve good applicability and portability, facilitate implementation, and reduce resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] In order to make the objectives, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below with reference to the accompanying drawings and embodiments. It should be understood that the specific embodiments described herein are only used to explain the present invention, but not to limit the present invention.
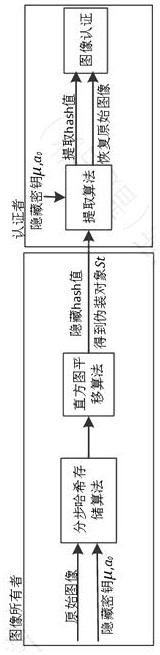
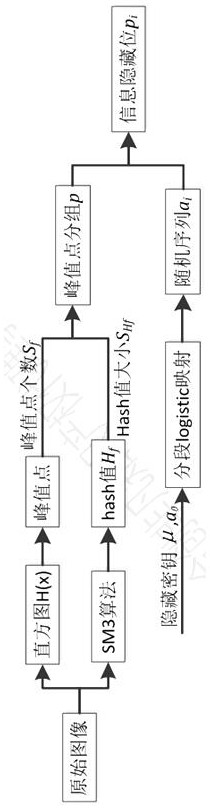
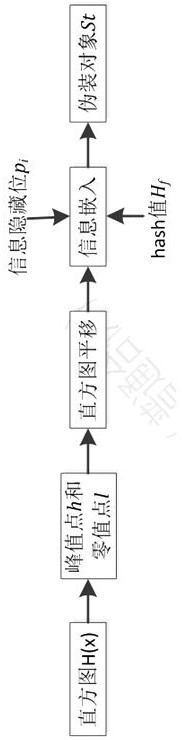
[0063] The invention uses the SM3 algorithm and the symmetric information hiding algorithm to perform integrity authentication on the images in the digital image library. First, the image owner uses the SM3 algorithm to generate a hash value H for the images to be transmitted. f , and use piecewise logistic map to generate random sequence a i , so as to get the hidden bit p of the hash value i . Then, the hash value is embedded at the peak point of the image histogram through the histogram translation algorithm, so as to obtain the camouflage object S t . The authenticator gets the mas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com