Method and apparatus for preventing fraudulent access in conditional access system
A conditional access and fraudulent technology, applied in the direction of collaborative devices, TV system components, error prevention, etc., to achieve the effect of preventing fraudulent access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
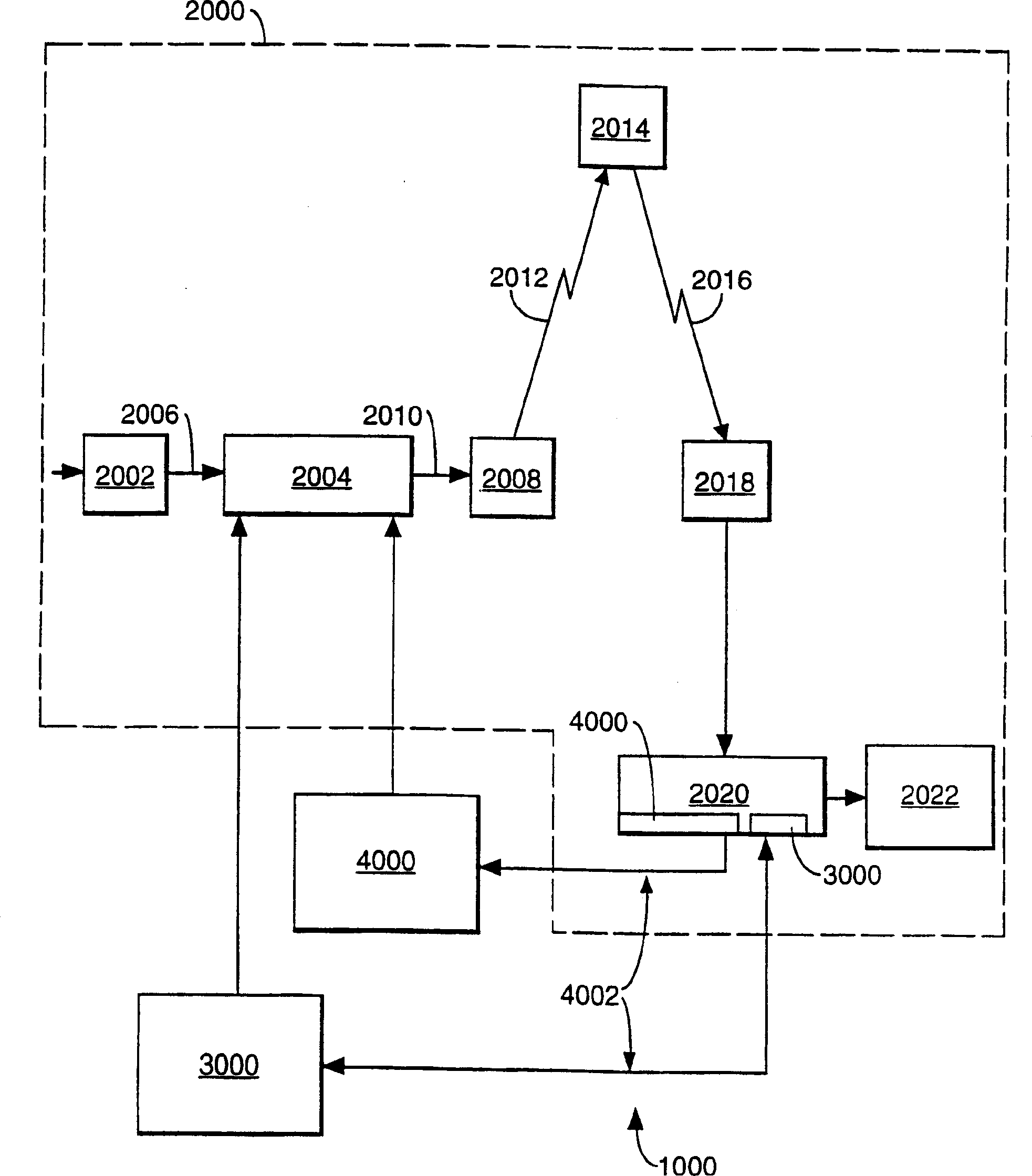
[0043] figure 1 A digital broadcasting and receiving system 1000 is shown which includes a conventional digital television system 2000 which uses the known MPEG-2 compression system to transmit compressed digital signals. An MPEG-2 compressor 2002 located in a broadcast center receives a digital signal stream (usually a video signal stream). Compressor 2002 is connected to multiplexer and encryptor 2004 by line 2006 . Multiplexer 2004 receives a number of additional input signals, assembles one or more transport streams, and transmits the compressed digital signal to broadcast center transmitter 2008 via link 2010, which may of course take many forms, including telecommunications link. Transmitter 2008 transmits electromagnetic signals via uplink 2012 to satellite transponder 2014 where they are electronically processed and broadcast via abstracted downlink 2016 to ground receiver / decoder 2018, typically owned or leased by the end user dish antenna. Signals received by rec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com