Image waterprint method for copyright protection
An image watermarking and copyright protection technology, applied in the fields of information hiding and information security, can solve the problems of abstract embedding, inability to clearly state copyright ownership, large amount of calculation, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example
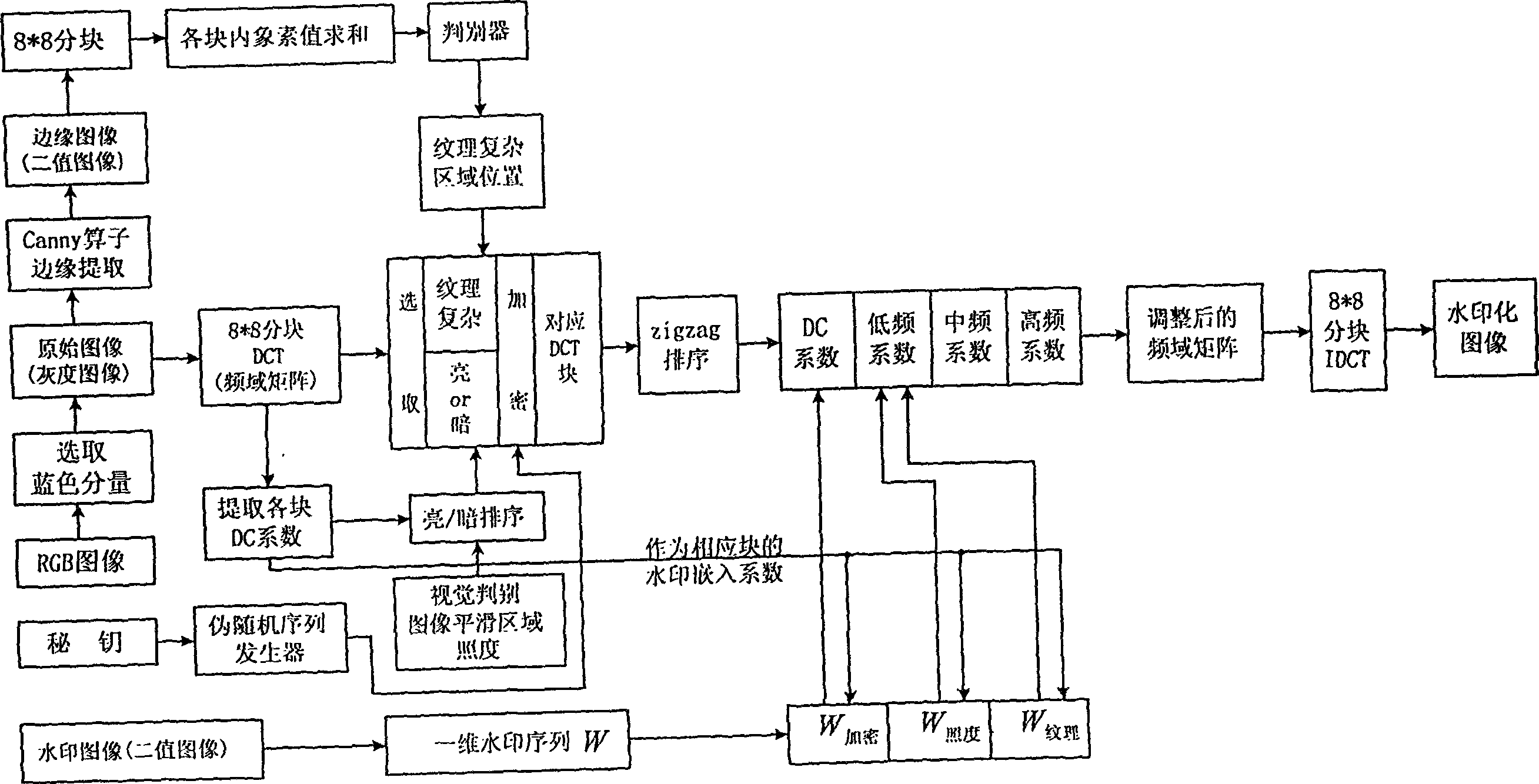
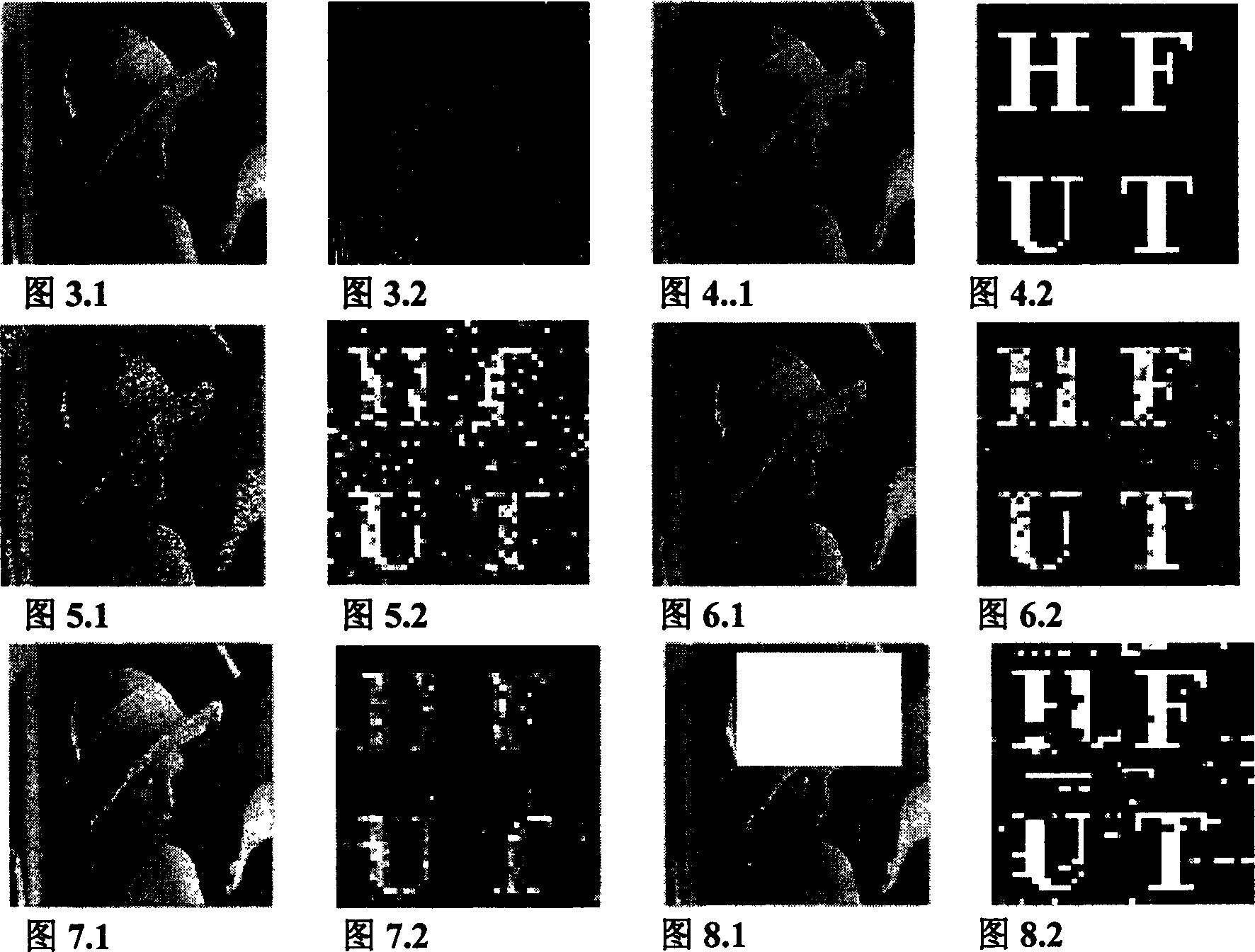
[0082]According to the above algorithm programming, the watermark is embedded in the original image. The original image is a 256×256 256-level grayscale image (Figure 3.1), and the watermark is a 40×40 binary image (Figure 4.2). Figure 3.2 is the edge image obtained by the canny operator. Observing the original image, it is found that most of the smooth areas are bright spots, so the dark spot areas are selected for embedding. Figure 4.1 is a watermarked image, the intensity α of the embedded low-frequency coefficient is 0.1, and the intensity α of the embedded DC coefficient is 0.006. It can be seen that the watermarked image generated by this method (Figure 4.1) has no obvious visual difference from the original work (Figure 3.1).
[0083] Because usually the images on the network are processed by printing, copying, scanning, etc., some noise will be generated. Gaussian noise is used here instead. Figure 5.1 is the watermarked image after adding noise, with a variance of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com