Method for identifying Internet users
An Internet and user technology, applied in the direction of data exchange network, data exchange details, computer security devices, etc., can solve the problems of huge cost, unsuitable for the huge market of new Internet services, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
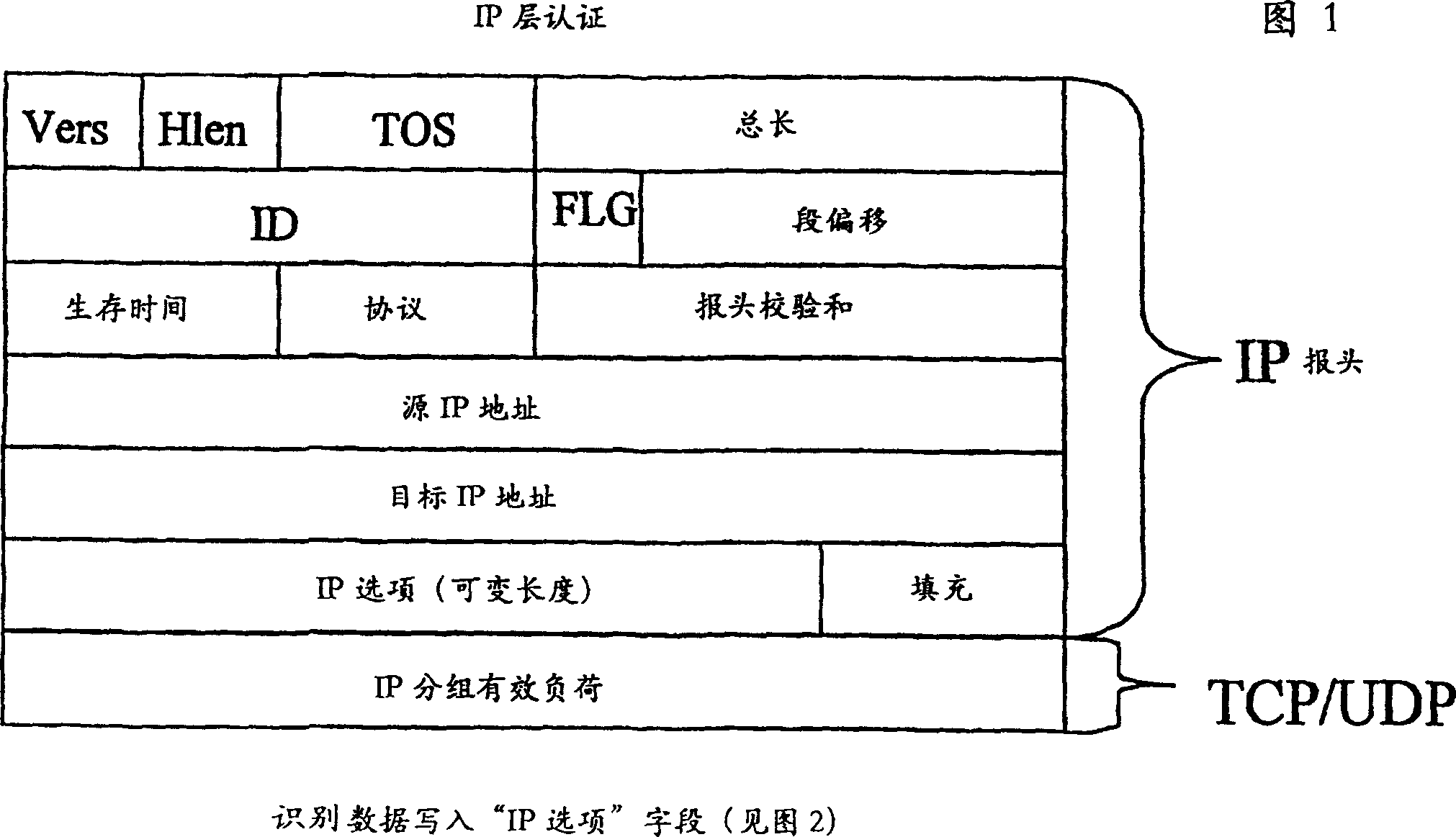
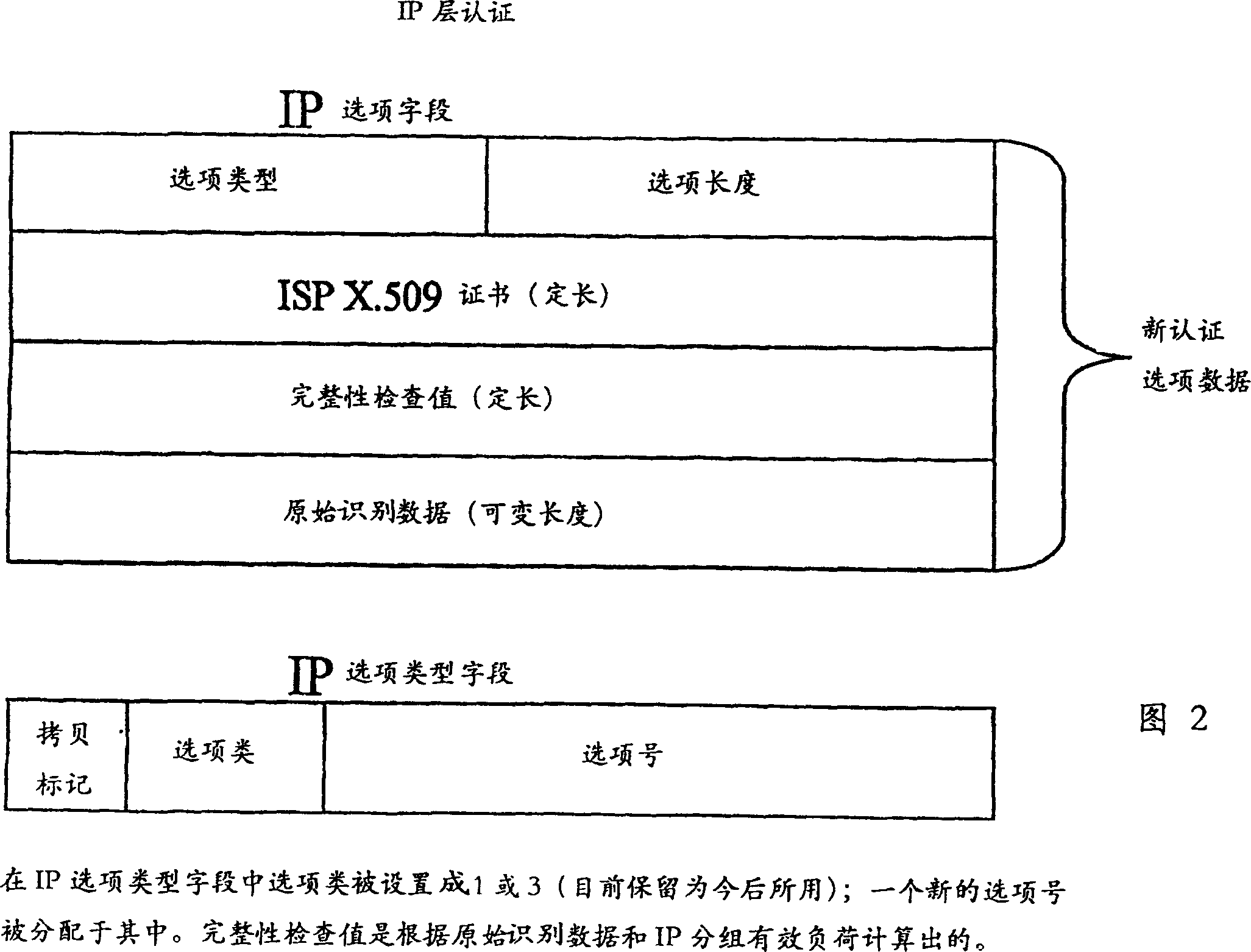
[0028] For a solution with the best possible general performance (independent of the transport or application protocol used), it is recommended to implement it at the IP layer (see Figures 1 and 2).
[0029] In the POP (Point-of-Presence, access node) of the Internet access provider,
[0030] · IP packets are checked for a certain (to be defined) flag set, a so-called authentication request flag, whereby Internet users can request that identification data be added to each IP packet, and / or
[0031] • Search in a database (with similar functionality to the security policy database under IPSEC) to see if "set IP packets with identifying data" has been requested by Internet users of the service. Here selector can be target IP address, transport protocol or TCP / UDP port.
[0032] If so, the Internet access provider will add data identifying the Internet user to the header of the IP packet. This could be, for example, the Internet user's telephone number, or his username, known t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com