Positioning vulnerable water print generating and recognizing method capable of distigushing image and watermark distortion
A technology of fragile watermarking and authentication method, applied in image communication, image data processing, image data processing and other directions, can solve the problems of harsh requirements, hinder the timely dissemination of news, hinder the promotion and application of digital images, etc., to ensure reliability and authenticity. It is beneficial to application and promotion, and the effect of news activities is efficient.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
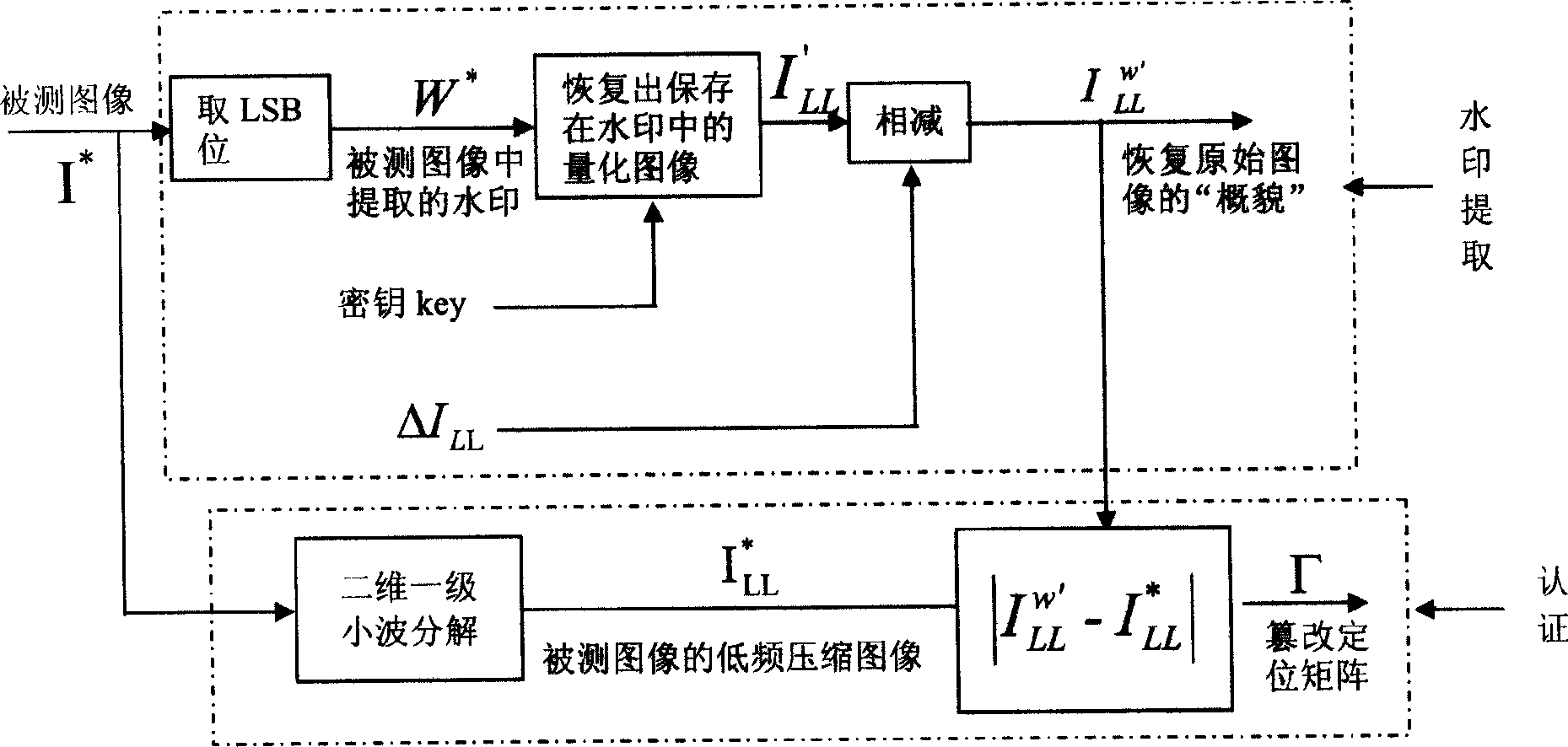
[0028] A positioning type fragile watermark generation and authentication method capable of distinguishing image and watermark tampering, comprising the following steps:
[0029] 1. Watermark generation:
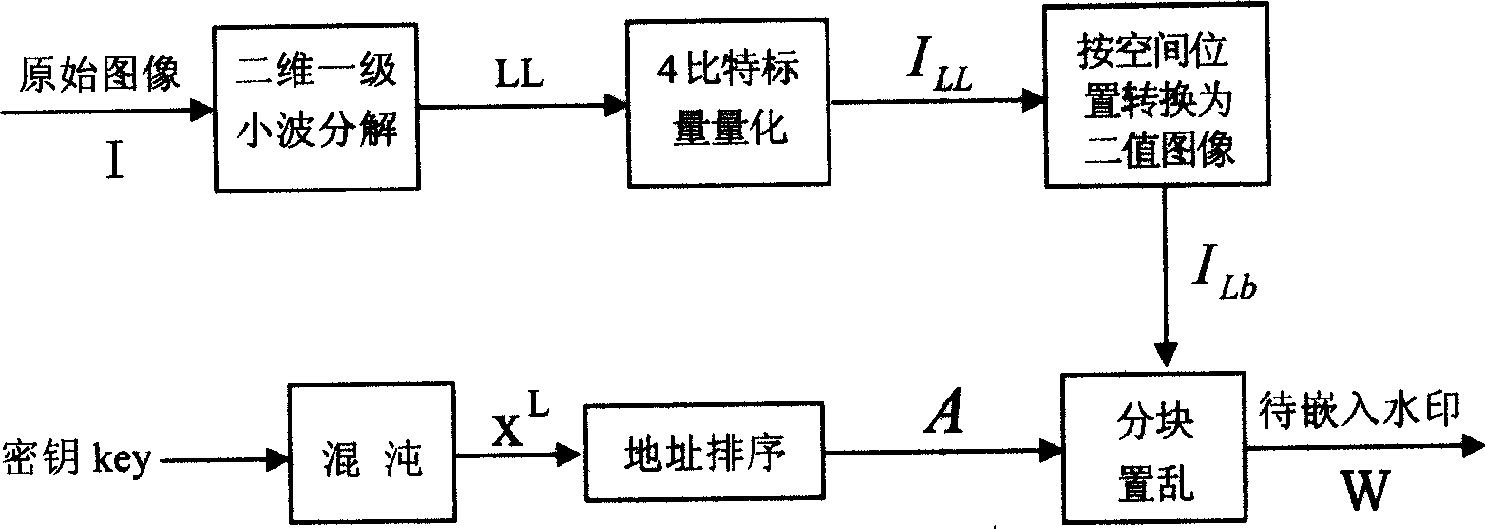
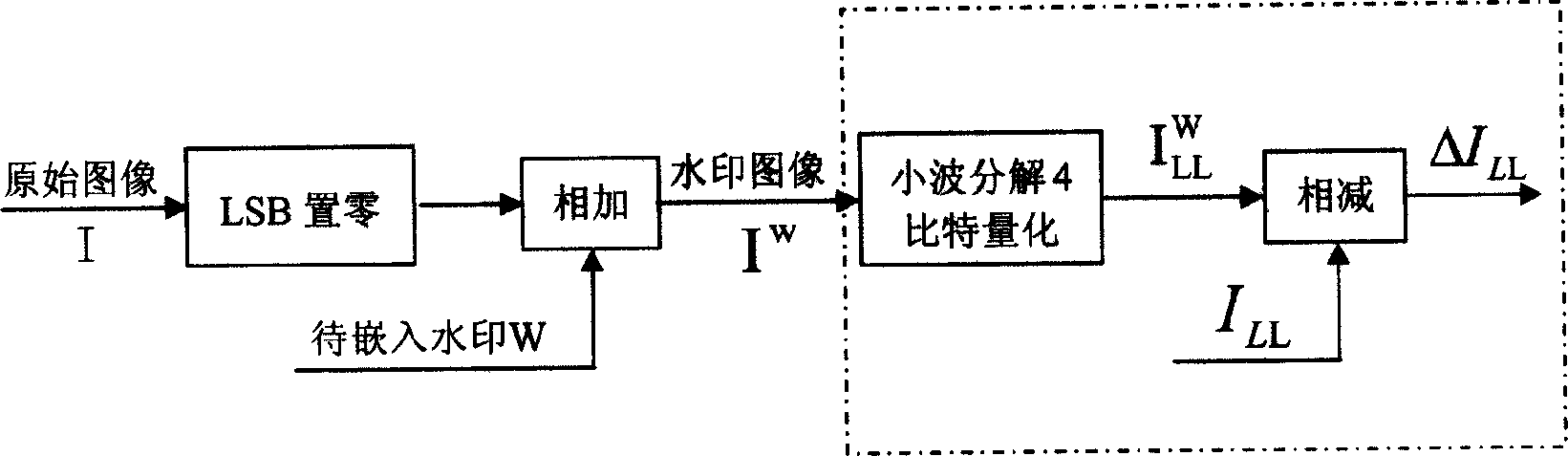
[0030] 1, figure 1 It shows that the early stage process of watermark generation is: perform two-dimensional one-level wavelet decomposition on the original image I to obtain: {LL, LH, HL, HH}, and quantize the low-frequency wavelet coefficient LL in it with 4-bit scalar to generate a low-frequency compressed image I LL , whose corresponding binaries are arranged in spatial order, generating a binary image I Lb .
[0031] In this embodiment, the DB1 wavelet base is selected to perform two-dimensional first-level wavelet decomposition on an image whose size is m*n, and perform 4-bit mean value scalar quantization on the low-frequency coefficient LL therein to generate a low-frequency compressed image I LL . The quantization process is described by the formula as:
[003...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com