Data tampering monitoring method based on iNotify real-time response
A data tampering and real-time response technology, applied in the field of information security, can solve the problems of the failure of the file signature, the inability to guarantee the authenticity of the data, and the inability to detect the arrival of new files in time. Effects of Sex and Reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
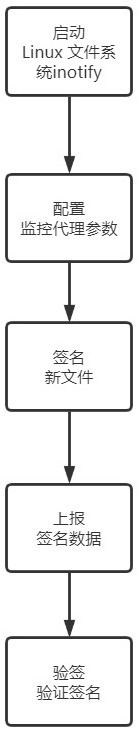
[0027] Such as figure 1 As shown, in the present embodiment, the data tampering monitoring method based on iNotify real-time response of the present invention, the specific steps are as follows:
[0028] Step 1: Install the iNotify module on the CentOS 7.8 Linux system, and then enable the iNotify function.
[0029] Enter the "ls -lsart / proc / sys / fs / inotify" command in the Linux system console, if you see the output in the monitor:
[0030] total 0
[0031] -rw-r--r-- 1 root root 0 Oct 9 09:36 max_queued_events
[0032] -rw-r--r-- 1 root root 0 Oct 9 09:36 max_user_instances
[0033] -rw-r--r-- 1 root root 0 Oct 9 09:36 max_user_watches
[0034] It means that the iNotify mechanism has been successfully started.
[0035] Step 2: Write the monitoring proxy module of the Linux system, so that the monitoring proxy module can monitor iNotify notification events.
[0036] Among them, use the "ssh-keygen" tool to generate a dedicated key pair for account user1, such as the priv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com