Method of carrying out hard disk protection by utilizing encryption of main zoning
A hard disk protection and main partition technology, applied in the direction of preventing unauthorized use of memory, instruments, electronic digital data processing, etc., can solve the problem that the main partition table cannot correctly guide the PC to load the operating system, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] In the following detailed description, specific details are described in order to provide a thorough understanding of the present invention. Those skilled in the art will recognize, however, that the invention may be practiced with other similar details.
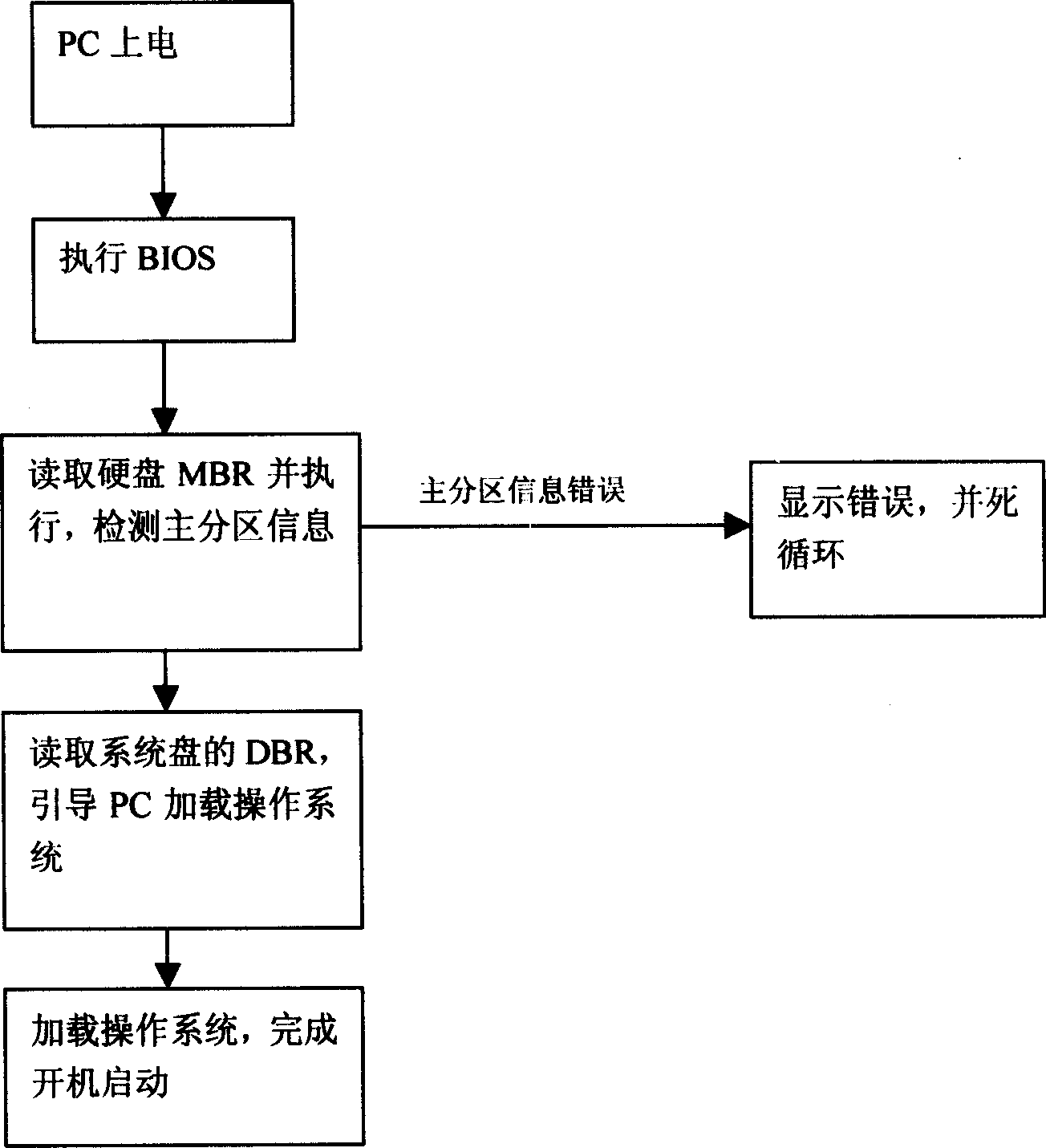
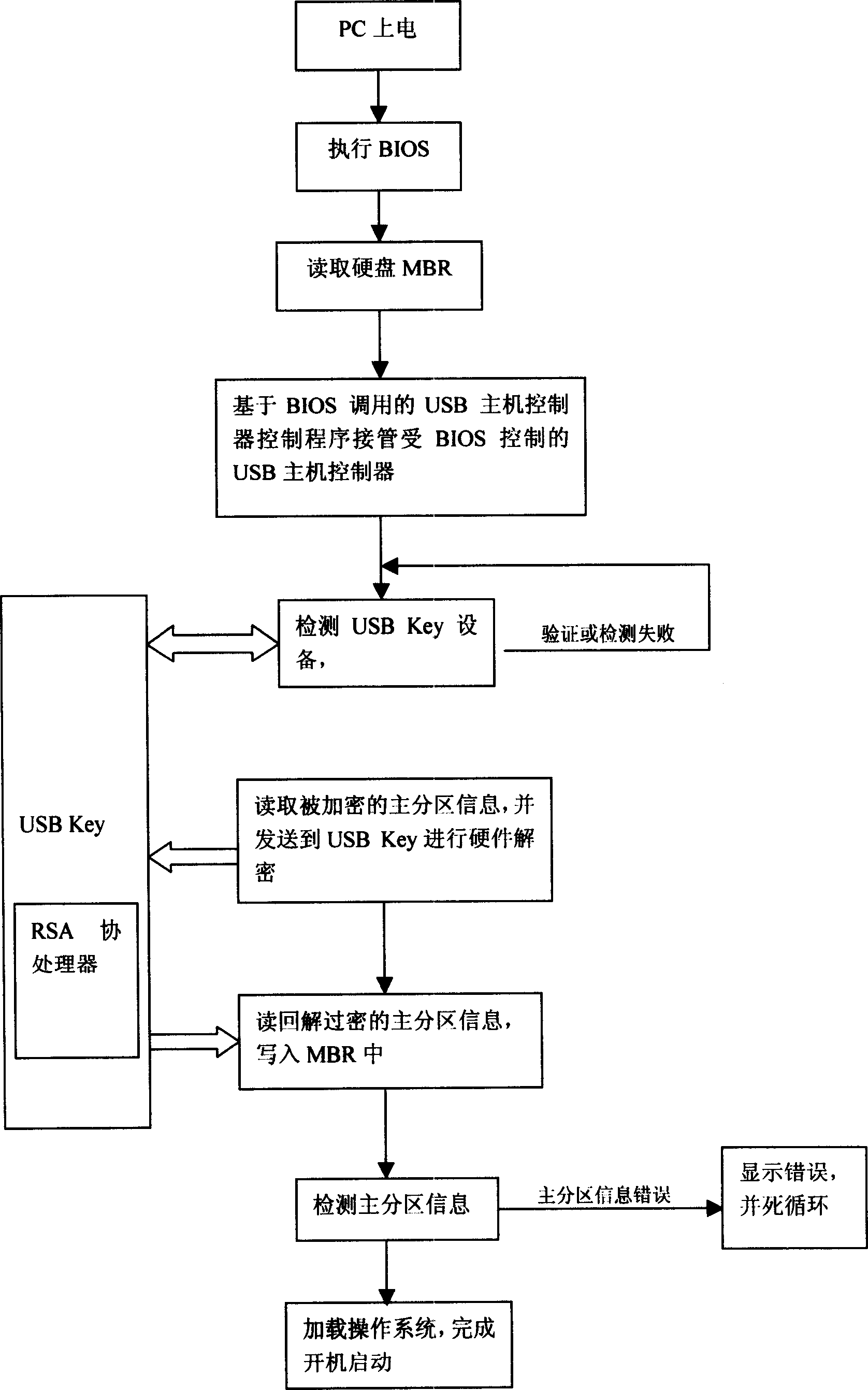
[0019] When the hard disk protection function is installed, store the MBR code with the function of controlling the program of the USB host controller based on the BIOS environment into the space starting from the 0th, 0th, 0th, and 1st sectors of the disk;
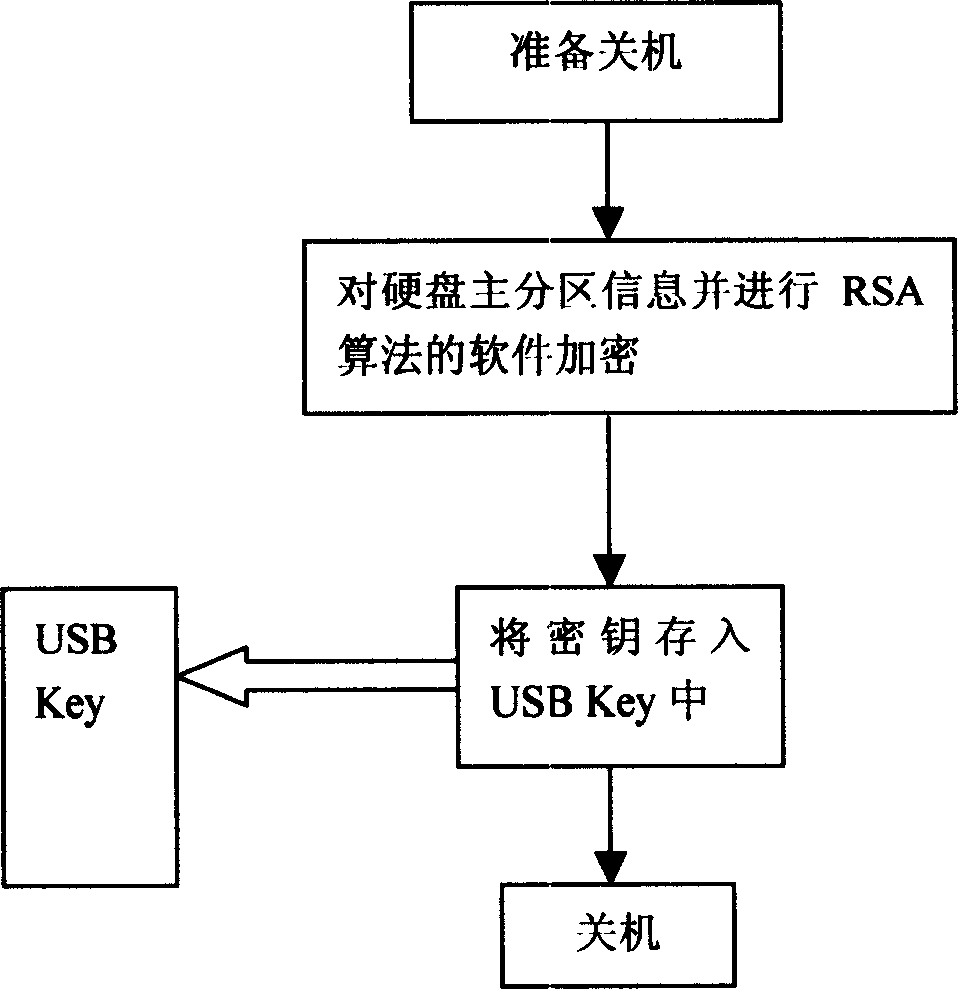
[0020] During the shutdown process of the PC, software encryption of the RSA algorithm is performed on the primary partition table of the hard disk, and the key is stored in the USB Key;
[0021] After the PC is started, it enters the MBR stage, and the USB host controller control program takes over the USB host controller based on the BIOS environment;
[0022] Detect the USB Key through the USB host controller control program;
[0023] Perform hardware decryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com