Access rate limiting method based on token pail algorithm
A token bucket algorithm and access rate technology, applied in the field of network communication, can solve the problems of the normal operation of the network access equipment, the large performance degradation of the network access equipment, and the consumption of large microcode resources.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
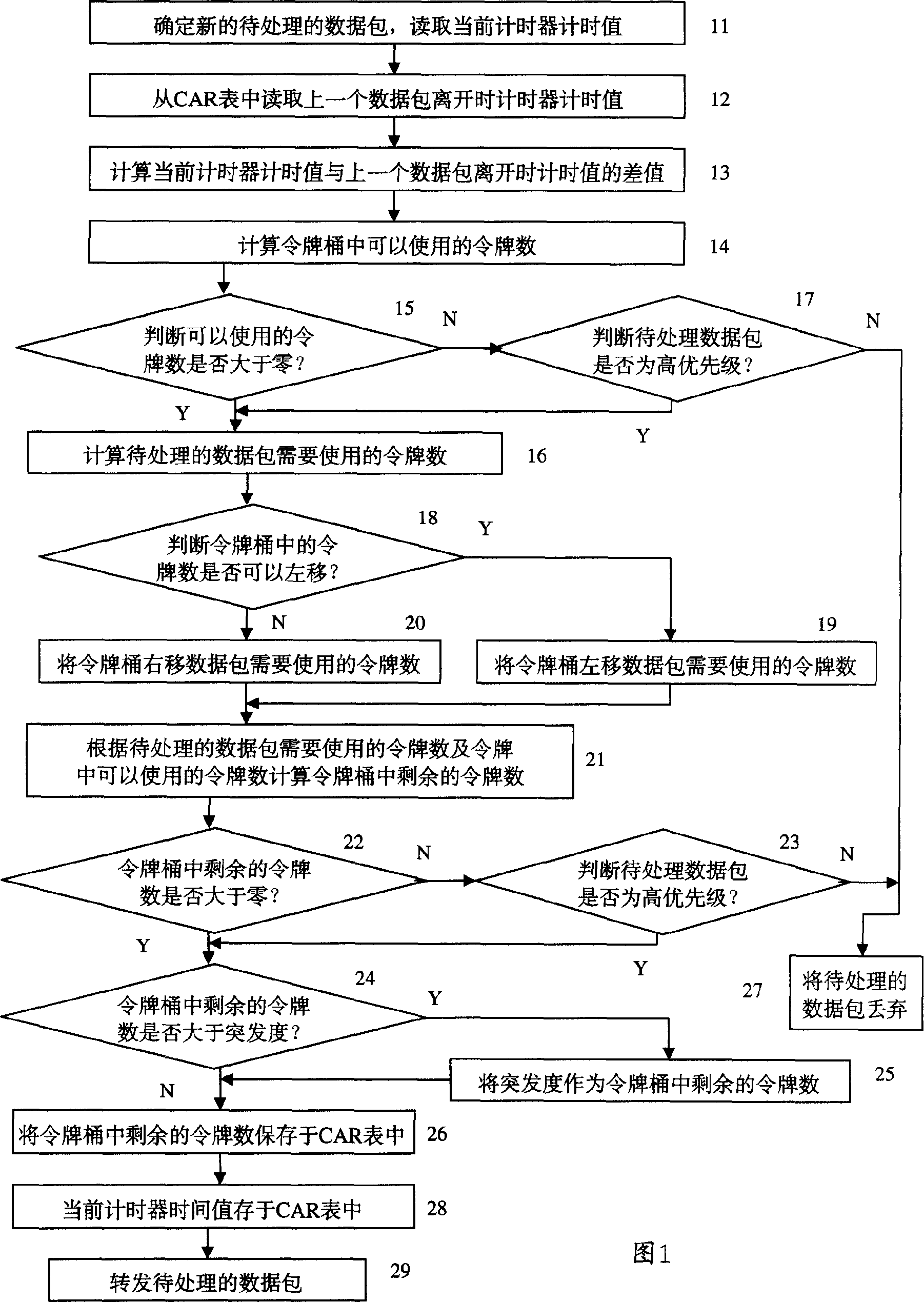
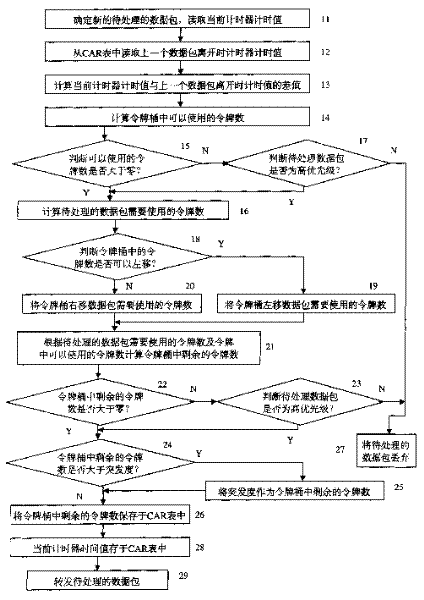
[0038] Because the realization of double leaky bucket increases the number of times of reading and writing memory according to the network processor, it has a great impact on the performance of the whole machine. Therefore, the present invention adopts the basic algorithm of double leaky bucket, but only uses one token bucket, allowing the token Negative tokens in the bucket are represented by one's complement.
[0039] The specific embodiment of the method of the present invention is shown in Fig. 1, comprises the following steps:
[0040] Step 11: Read the current time of the timer.
[0041] Step 12: Read the time value of the timer when the last packet left from the CAR table.
[0042] Step 13: Calculate the difference between the current time of the timer and the time value of the timer when the last data packet leaves.
[0043] Step 14: Add the difference obtained in step 13 to the number of tokens remaining in the token bucket when a data packet leaves, as the number o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com