Safety ability consultation method
A technology of security capabilities and protocols, applied in secure communication devices, synchronous send/receive encryption equipment, digital transmission systems, etc., can solve the problems of many protocol interaction processes, poor scalability, and impact on interoperability, and achieve a simple interaction process. , The effect of strong scalability and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055] In the NGN network, network security is an important problem encountered in the actual operation of the NGN network. If the security problem of the NGN network cannot be solved well, the NGN network will not be able to be applied on a large scale.
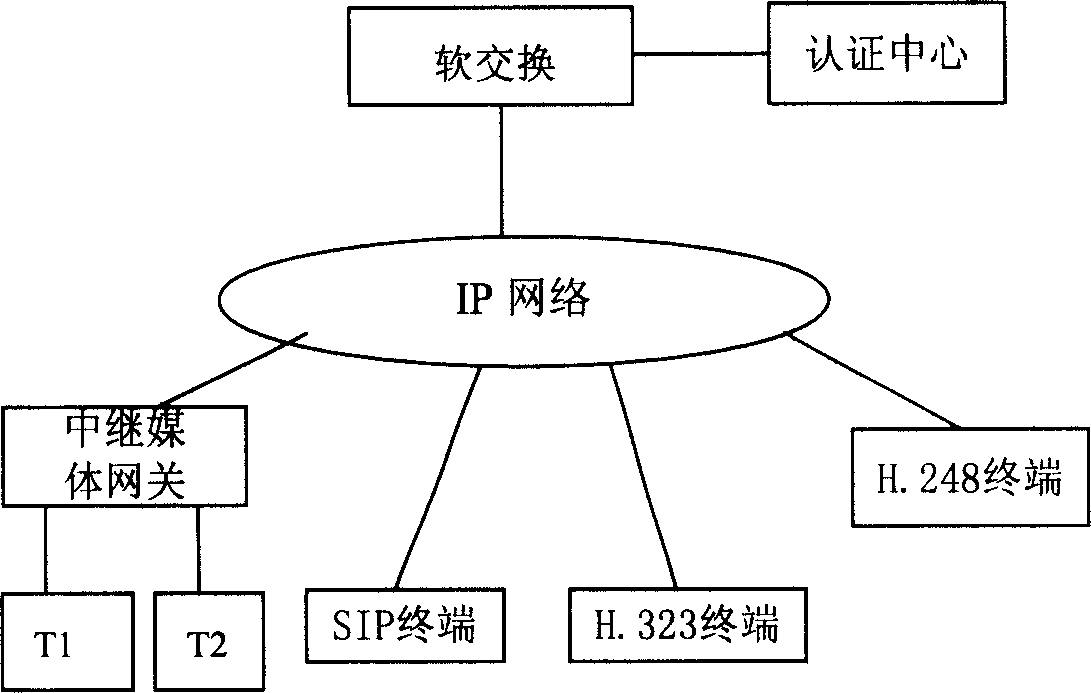
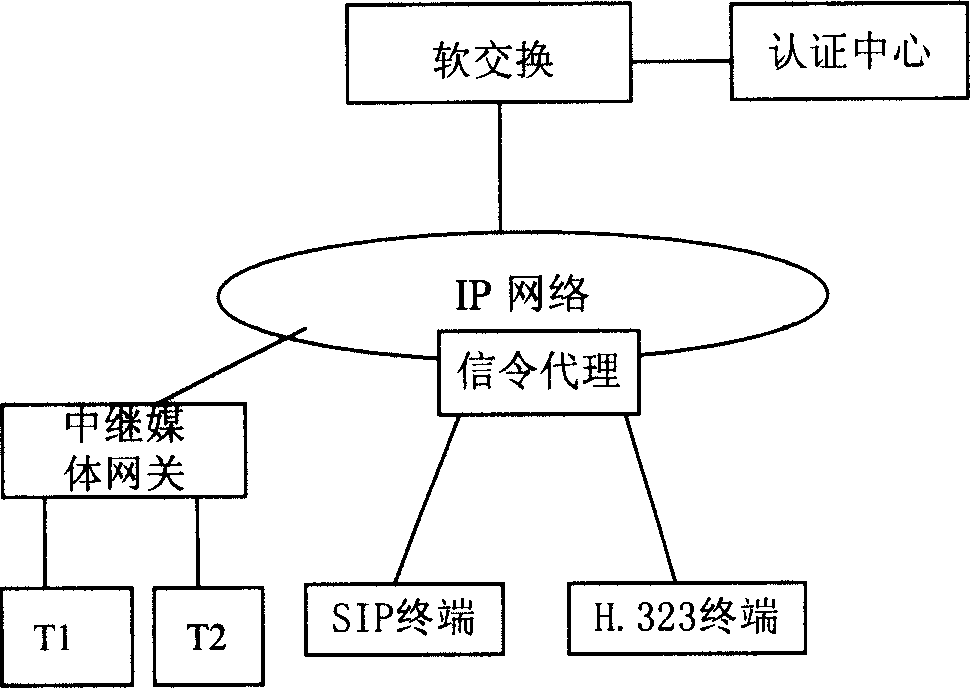
[0056] In an NGN network, network equipment mainly includes terminals, gateways and soft switches, etc. figure 1 It is a simple single-domain network diagram of NGN, that is, there is only one softswitch (also called media gateway controller) device, and the actual network may have multiple softswitch devices. Such as figure 1 In the NGN network environment shown, the softswitch is connected to the trunk media gateway, SIP (Session Initiation Protocol) terminal, H.323 terminal and H.248 terminal through the IP network, and the trunk media gateway is connected to the analog telephone T1 and T2 , In addition, the soft switch is also connected with the authentication center AuC.
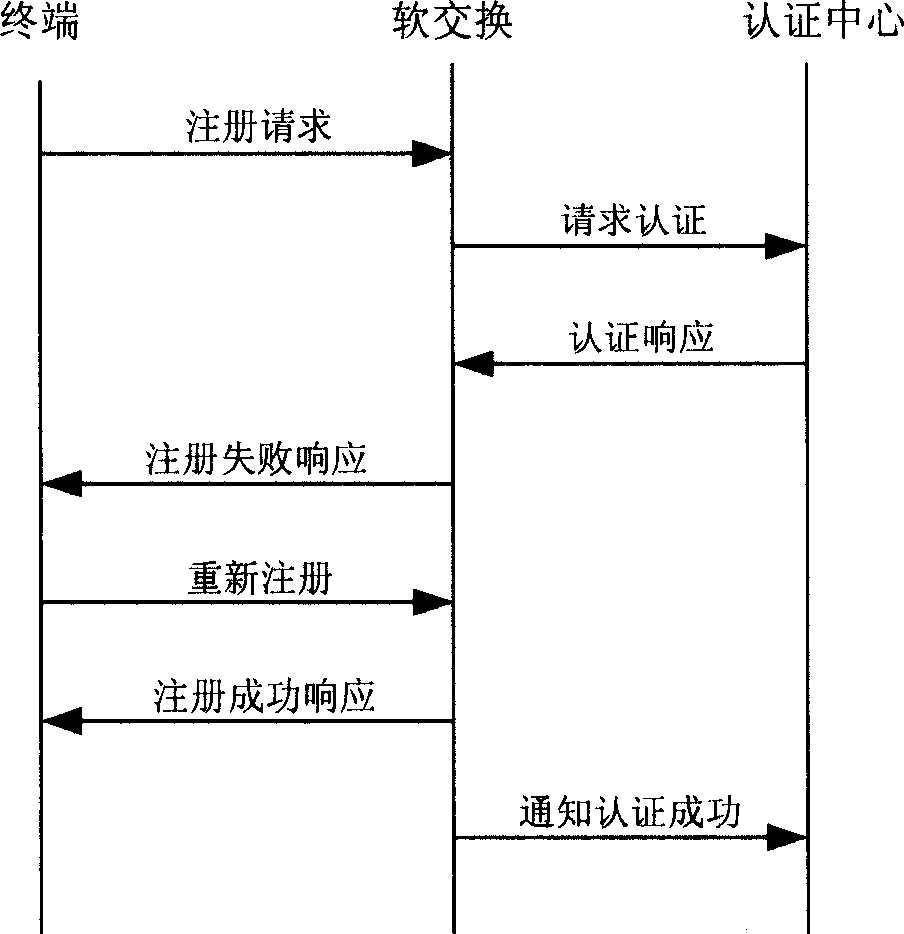
[0057] The present invention combines the cha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com