A method for implementing security communication between mobile self-organized network nodes
A mobile ad hoc network and mobile communication technology, which is applied in the field of realizing secure communication between mobile ad hoc network nodes, and can solve the problems of mobile node counterfeiting, network security threats, security attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
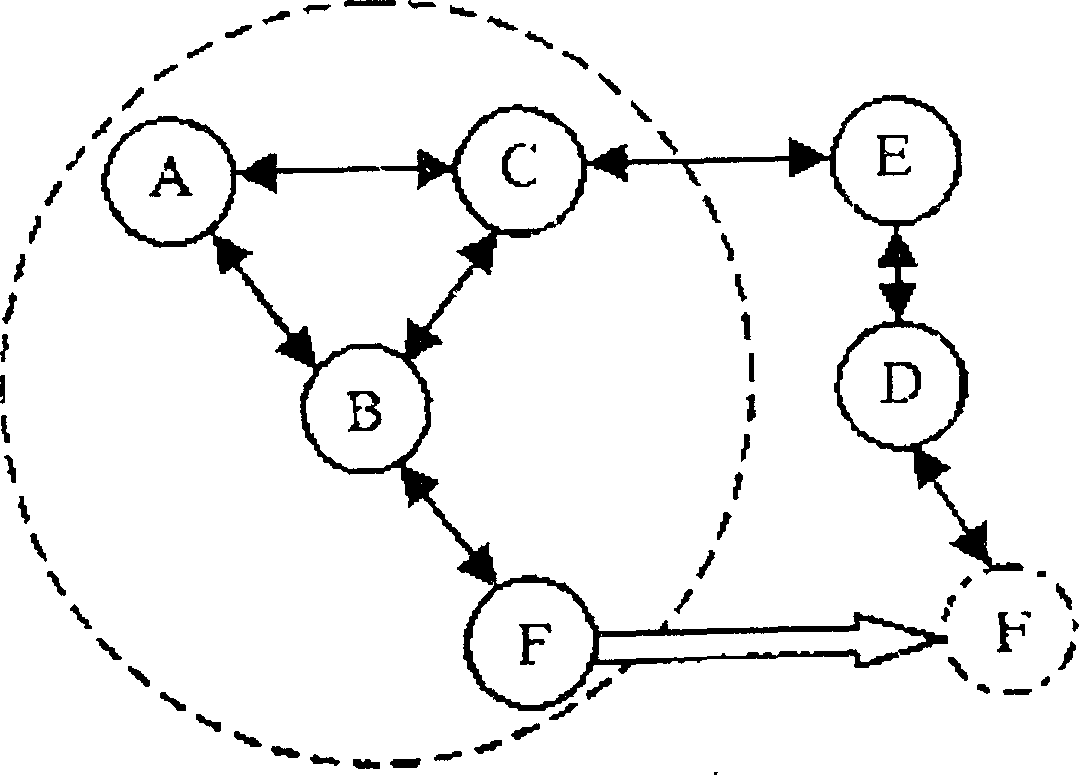
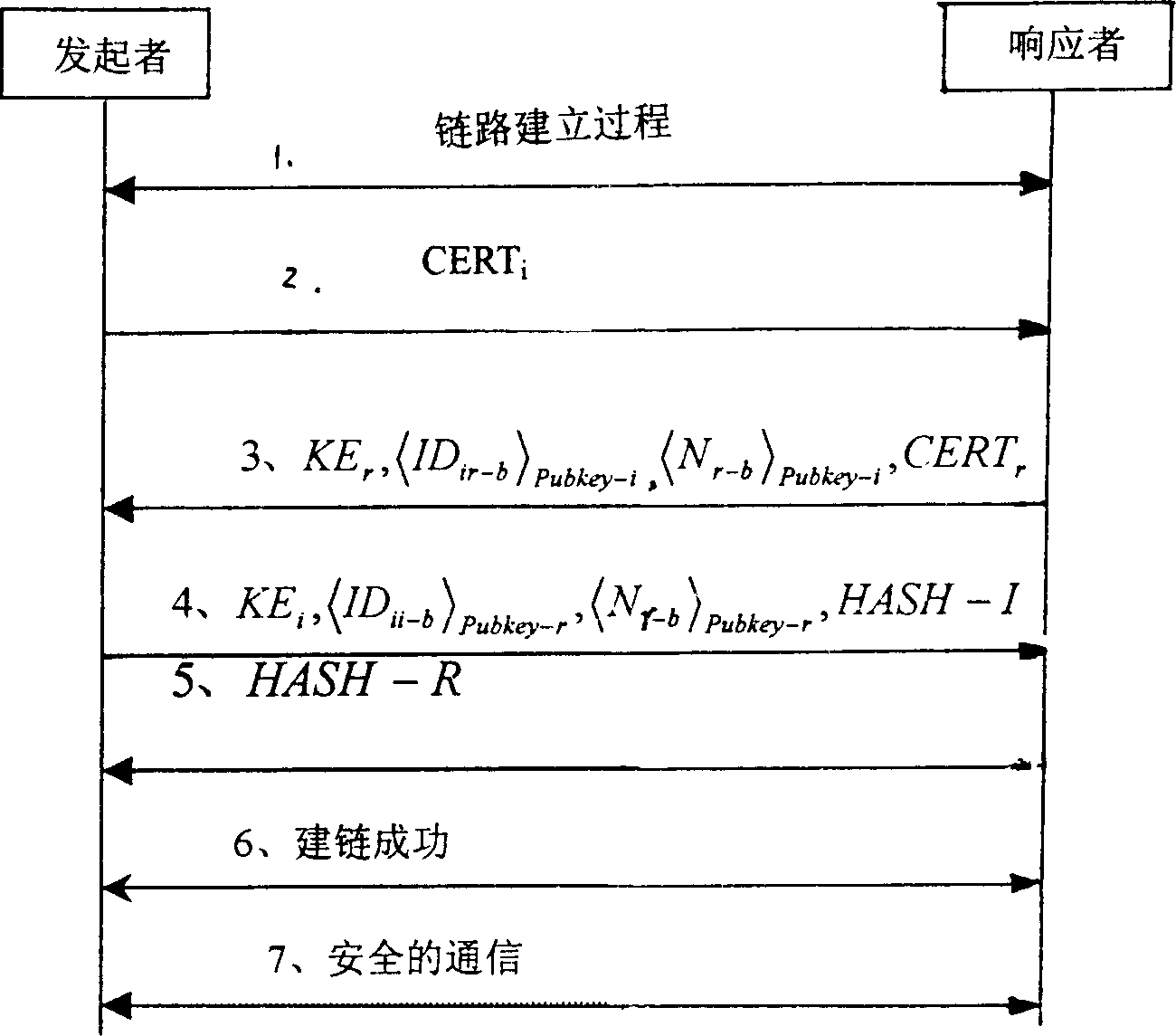
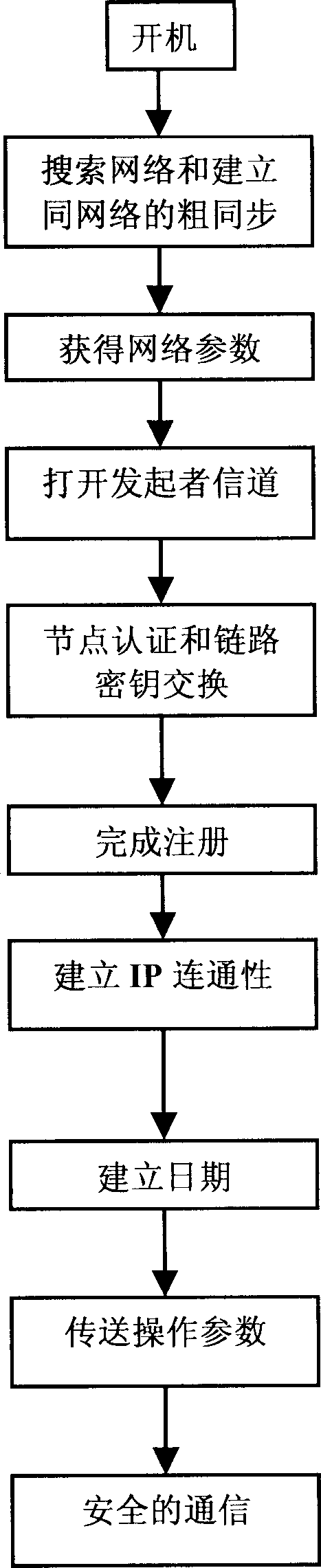
[0037] Modern IP network, its protocol reference model consists of physical layer, data link layer, network layer, transport layer and application layer from bottom to top, and the method of the present invention is implemented in the second layer of data link layer. This layer is mainly composed of control plane, data plane and framing plane. The data plane transmits the data sent from the network layer to the framing plane, so as to pass it to the communication partner; at the same time, the data plane transmits the data sent from the framing plane to the network layer for processing; the framing plane transmits the upper layer data sent from the data plane After adding the frame header of the data link layer to the control message sent by the control plane, it is transmitted to the communication peer through the physical layer; at the same time, the framing plane sends the data received from the physical layer to the data plane and the control plane respectively. The contro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com