Safety device for identifying cipher and safety identifying method
A password security and password technology, applied in the field of identifying password security devices, can solve the problems of expansion of password card space, increase of memory cost, unfavorable portability, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
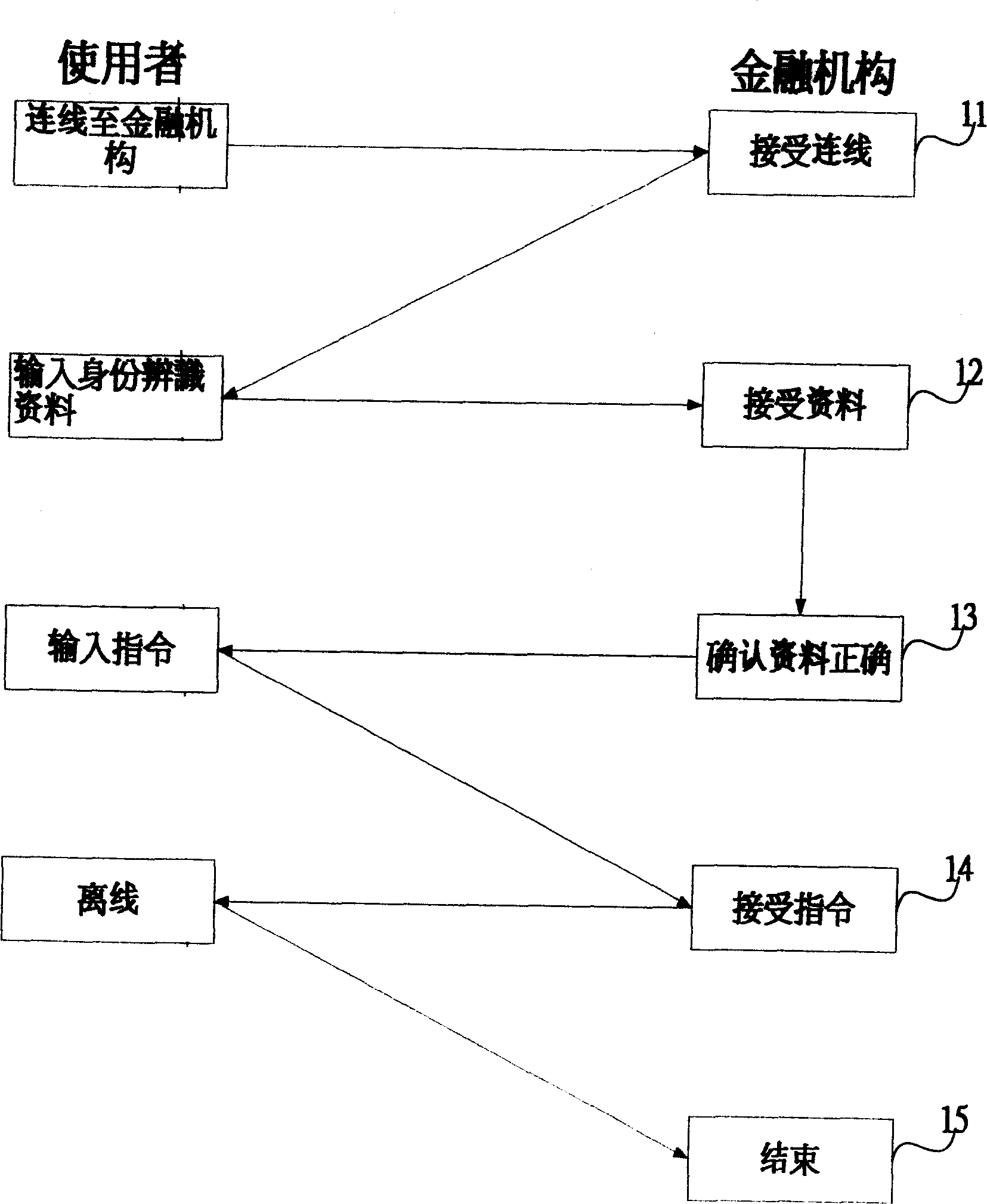
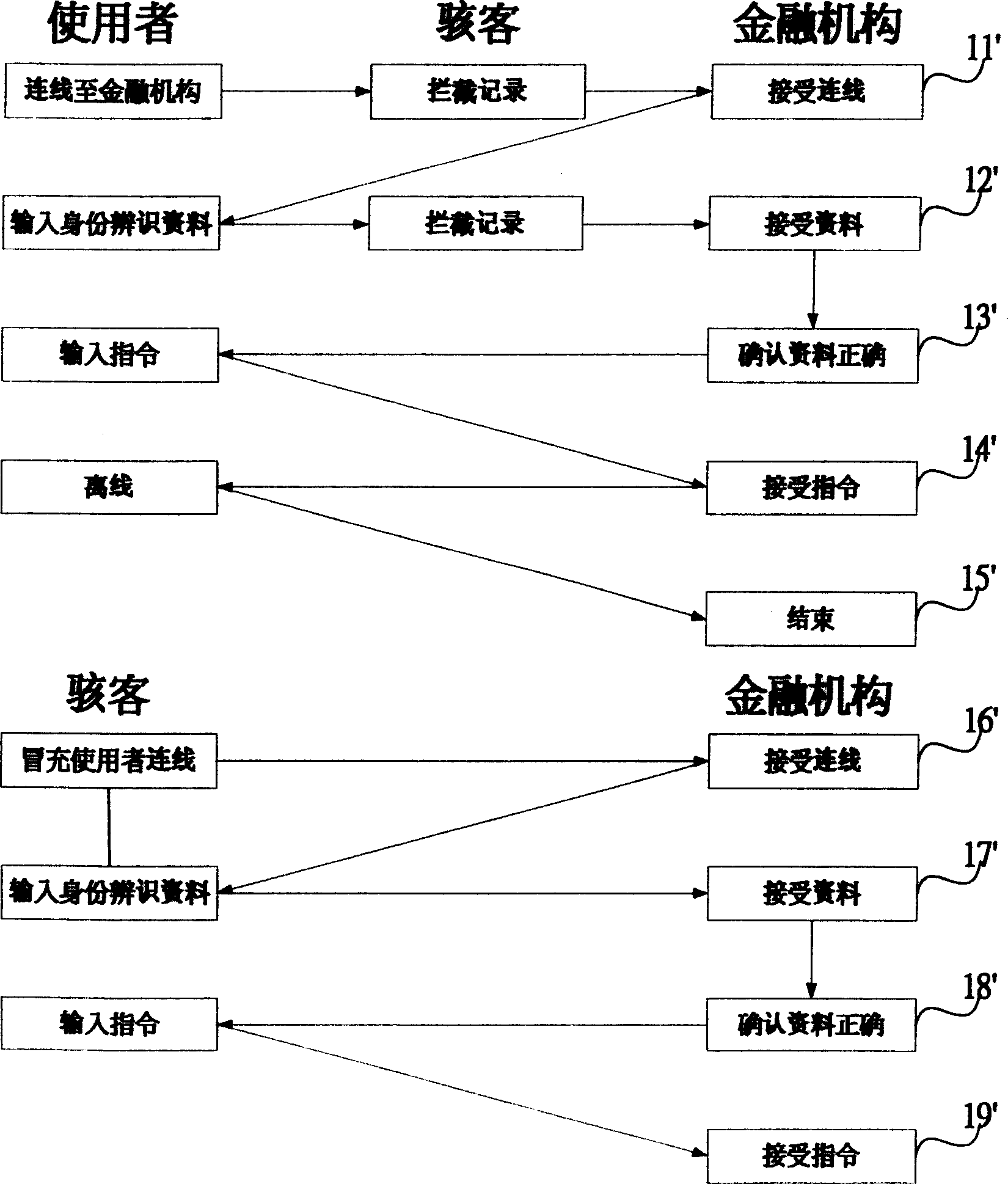
[0041] The structural features of the present invention are described in detail as follows with reference to the drawings and embodiments:
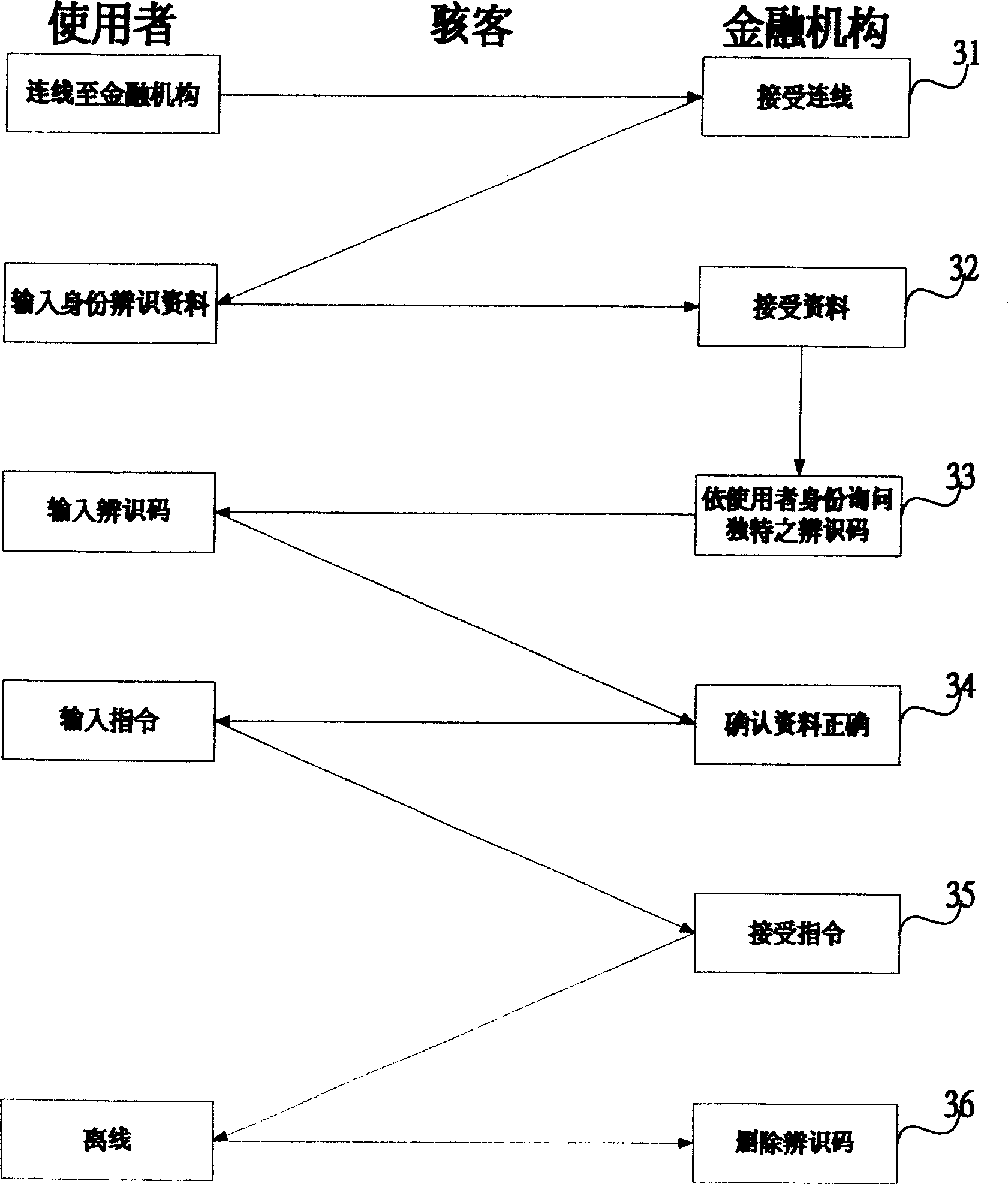
[0042] Such as image 3 Shown below is the flow of the Taiwanese Patent Application No. 93111819 applied to the present invention. When a financial institution accepts the user's connection in step 31, it immediately asks the user to input such as name, ID number, and Identification data such as identity authentication passwords; and in step 33, after the server confirms that the data is correct, then directly select any password address in the identification password group corresponding to the user to ask the question, and ask the user to operate the password machine Or read the password card to find out the identification password output corresponding to the address; in step 34, accept and confirm that the user identification password is correct, and in step 35, accept the user instruction.
[0043] The difference from the previous case is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com