Public key code hopping safety system and method
A security system and code-hopping technology, which is applied in the field of encrypted code-hopping security systems, can solve problems such as block cipher code-hopping systems that cannot ensure system security, and achieve the effects of reducing costs and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
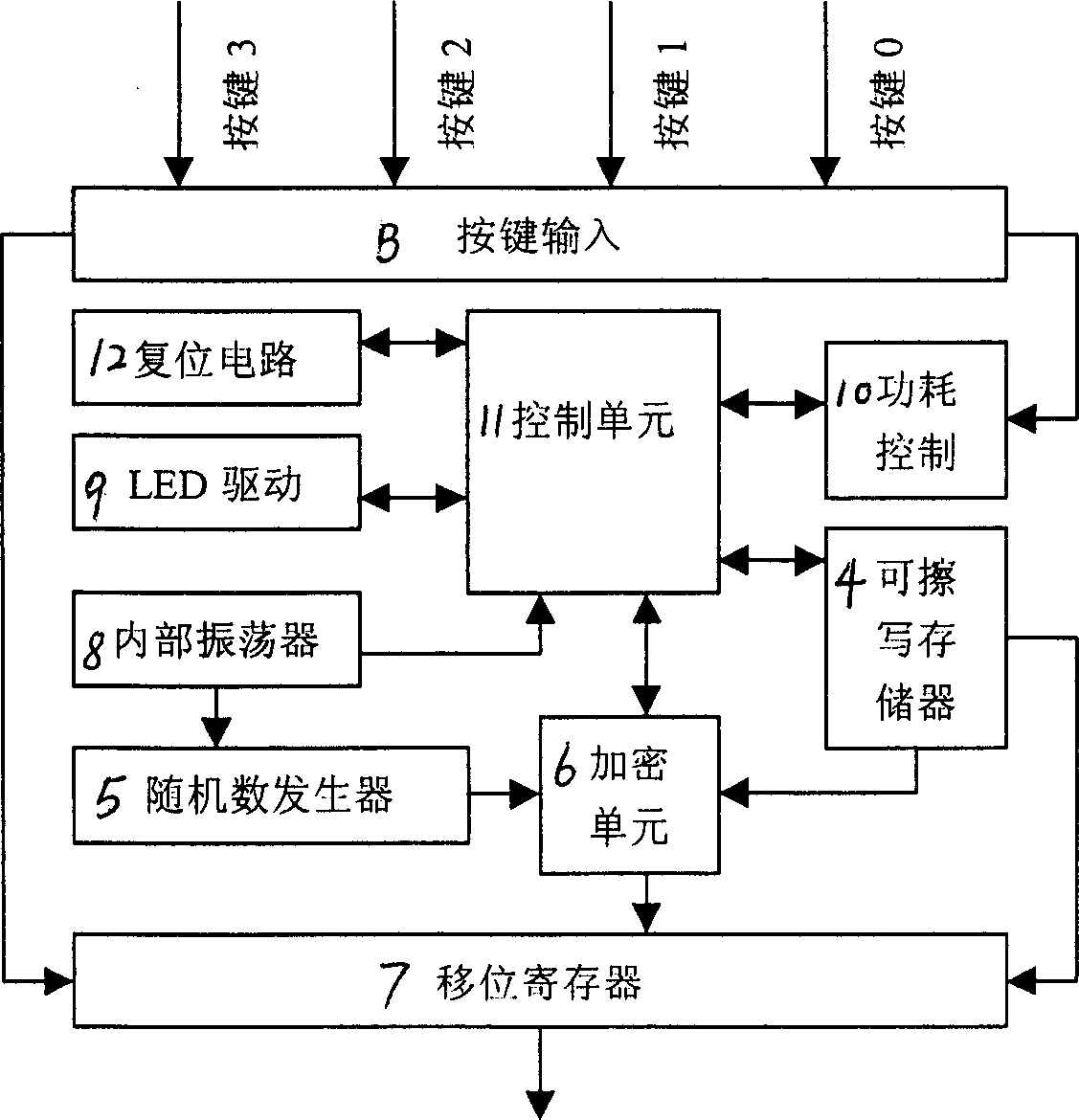
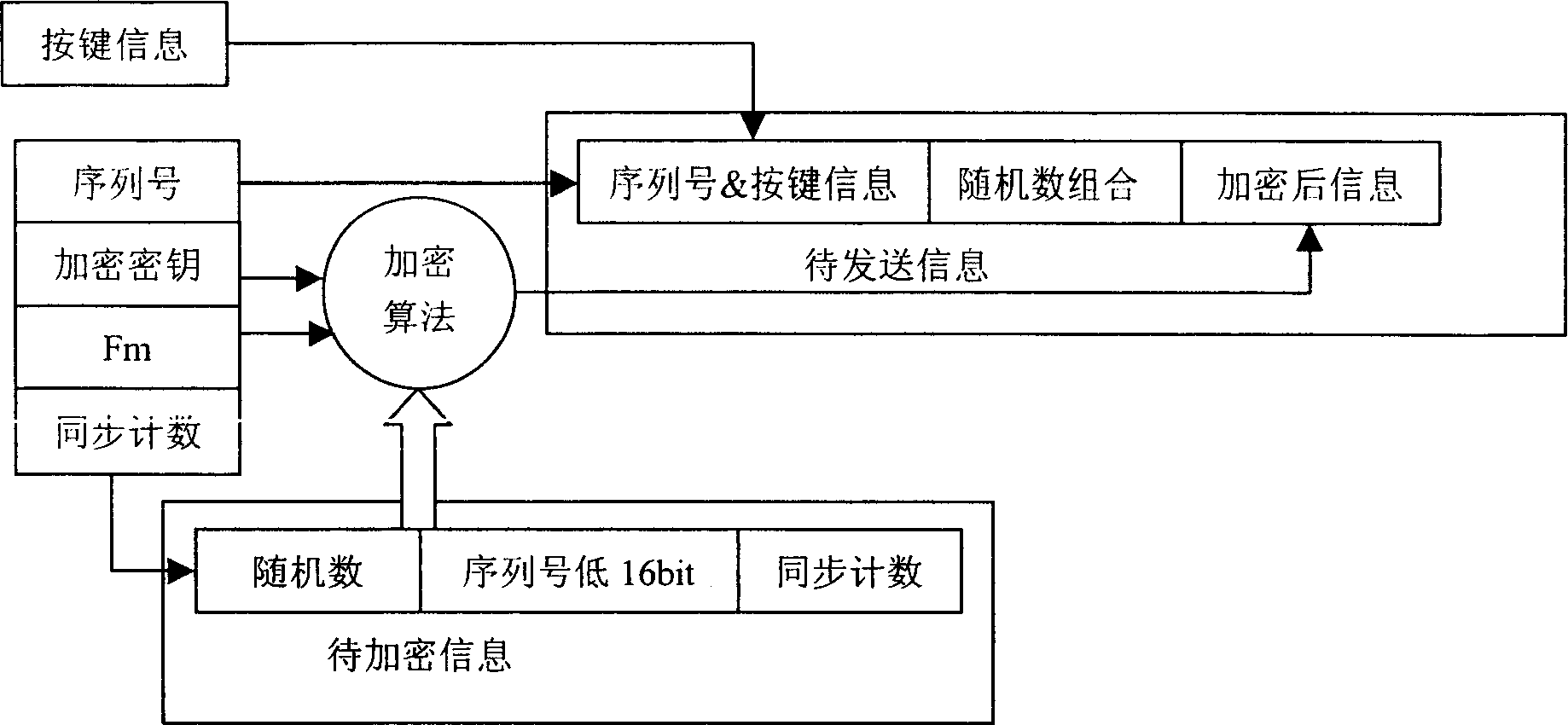
[0017] System main parameters:
[0018] Encryption key (CryptKey) 32bit, used in the encryption process;
[0019] Decryption key (DecryKey) 32bit, used in the decryption process;
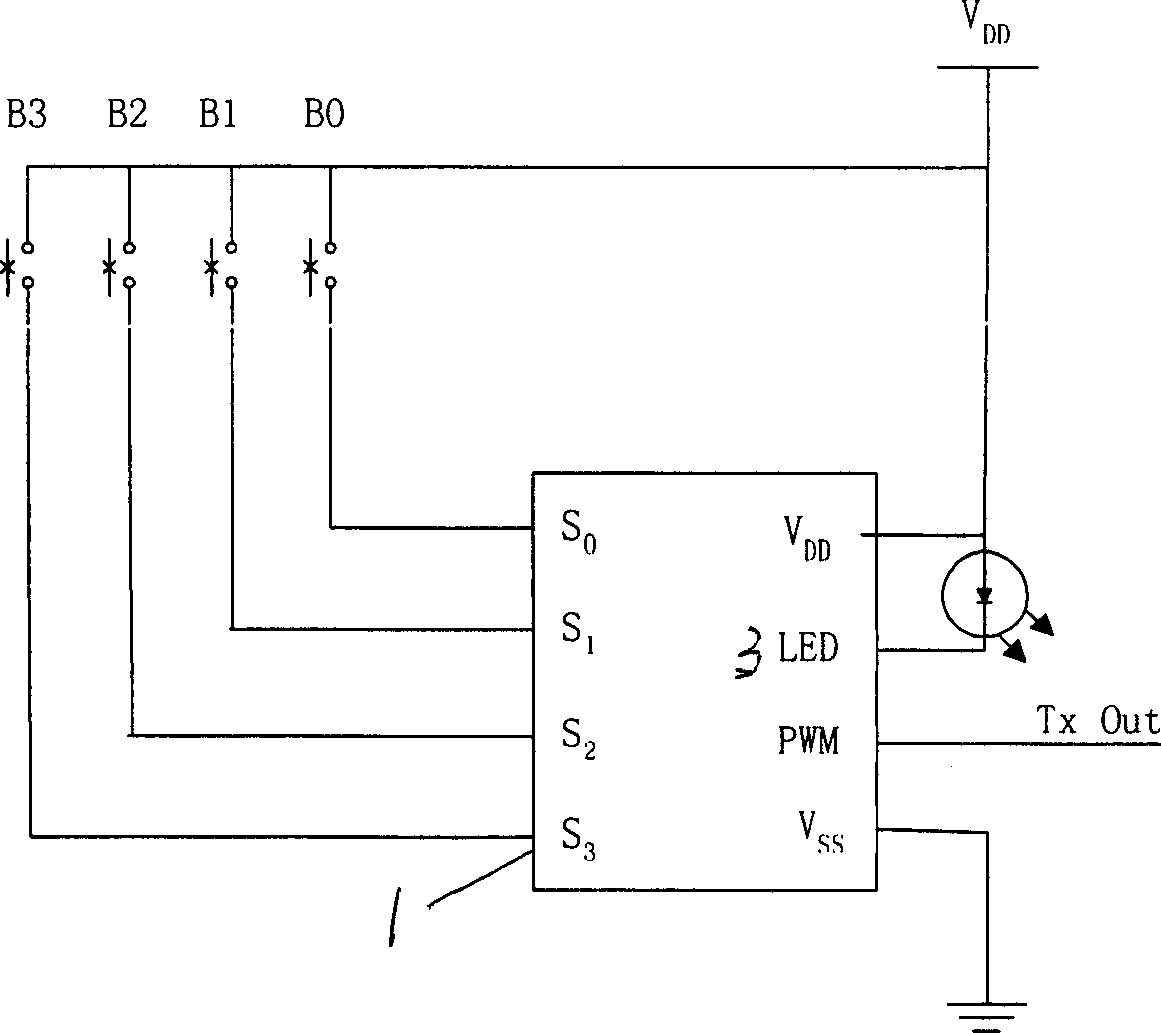
[0020] Button information (ButtonInfo) 4bit, the information to be transmitted, the receiving end will perform corresponding operations according to the button information;
[0021] Serial number (Serial Numbs) 28bit, the unique sign of each electronic key, the door lock system relies on this sign to identify whether it is its own electronic key;
[0022] Synchronous counting (Counter) 16bit, every time the electronic key is pressed, the number is incremented by one, which is used to generate hopping codes and some security checks after encryption;
[0023] Manufacturer ID (ManufactureID) 32bit, the unique logo of each car manufacturer, which is combined with the serial number to generate the encryption key and decryption key;
[0024] The encrypted data (Encrypted Data) 32bit, that is, the chang...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com