Information safety protecting method and protector based on network software
A network software and information security technology, applied in the direction of secure communication devices, electrical components, digital transmission systems, etc., can solve the problems of high cost and inconvenience, and achieve the effect of saving the amount of use and reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
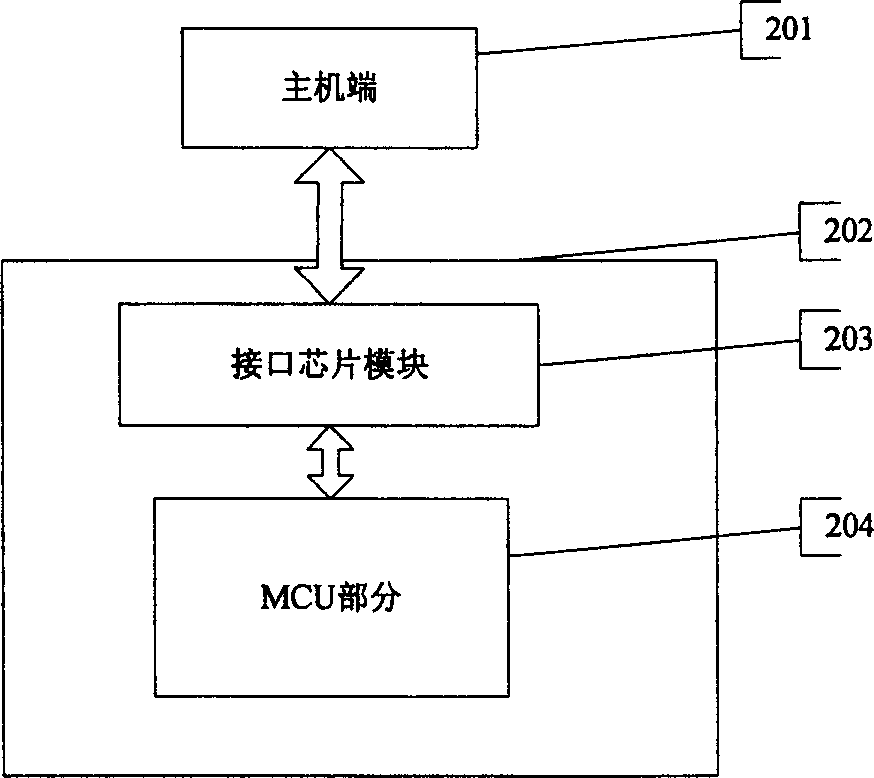
[0025] Example 2 as figure 2 As shown in , it includes an MCU 204 integrated with a memory and a communication interface 202, and an interface module 203 for analyzing the communication protocol is connected between the communication interface 202 and the MCU.
Embodiment 3
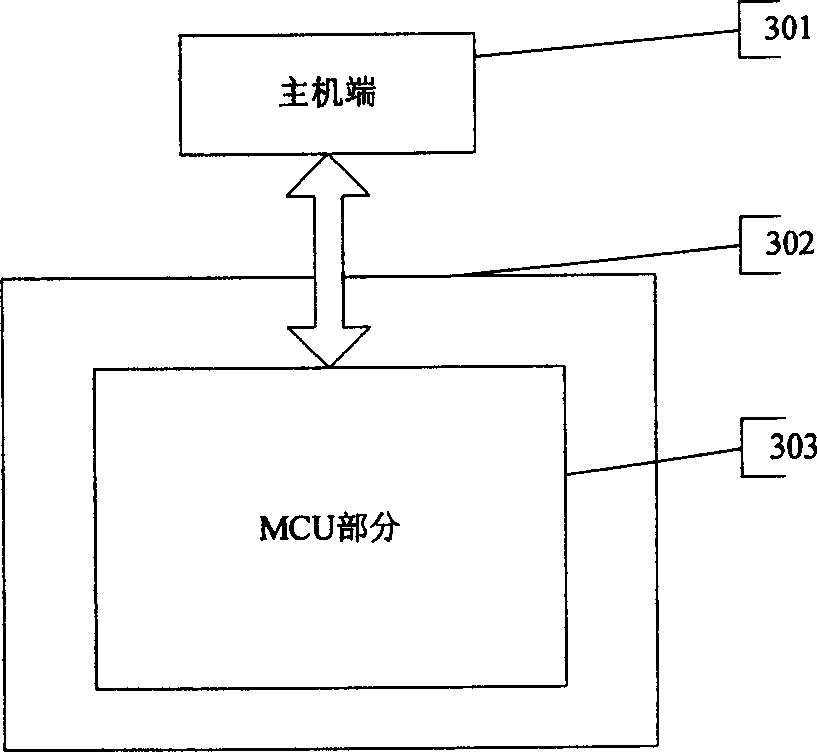
[0026] Example 3 as image 3 As shown in , the MCU 303 integrating memory and interface modules is connected to the host through the communication interface 302 .
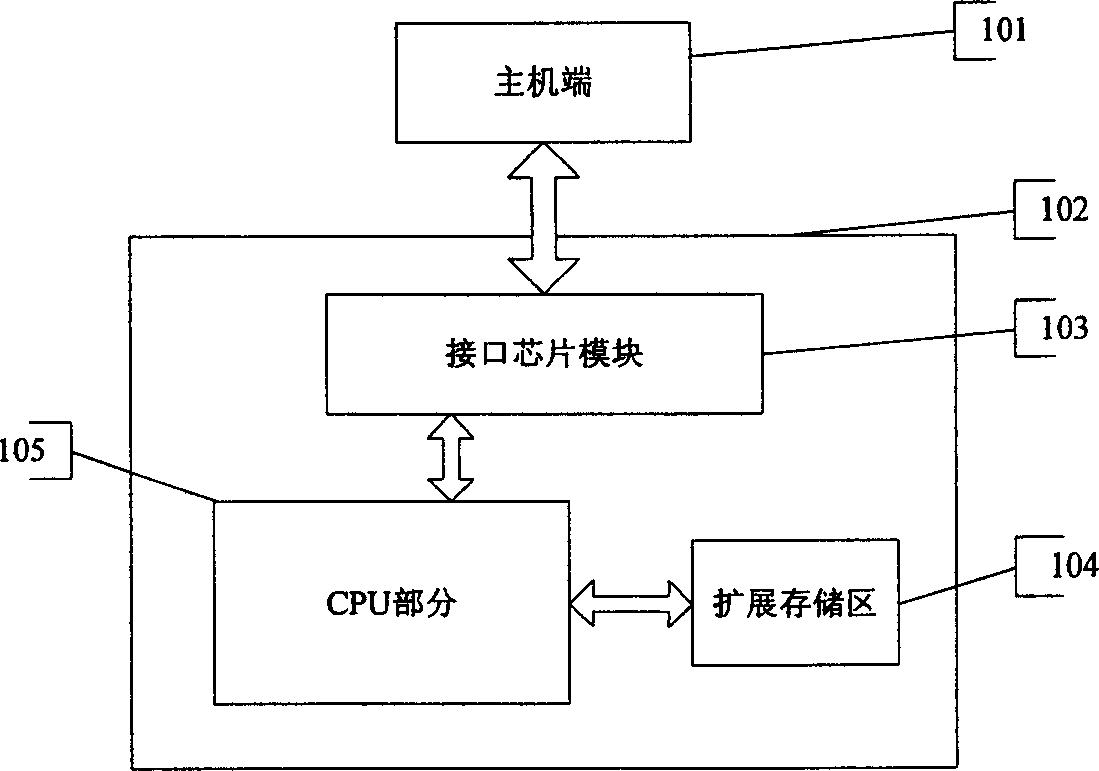
[0027] The MCU and CPU are used as main control units to run firmware programs and user programs, and can also be replaced by micro-processing chips such as single-chip microcomputers or smart cards. The memory is used to store device firmware programs, user data, status information and corresponding encryption algorithms, including RAM, ROM, EPROM, EEPROM, FLASH, etc. The memory should have enough storage space for storing the preset encryption algorithm, or the algorithm can be selected or downloaded by the user, and if it is necessary to store part of the user code, it needs to have a large enough storage space. The interface modules 103 and 203 are used to analyze the communication protocol when the device communicates with the host, and adopt a USB HID interface chip. The firmware program part includes: the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com