Instruction cipher system and processing method
A cryptographic system and processing method technology, applied in the field of command cryptographic system, can solve problems such as inconvenient use of multi-command cryptographic system, loss of account funds, etc., and achieve the effects of easy acceptance by customers, clear responsibilities, and reduced possibility of profit
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
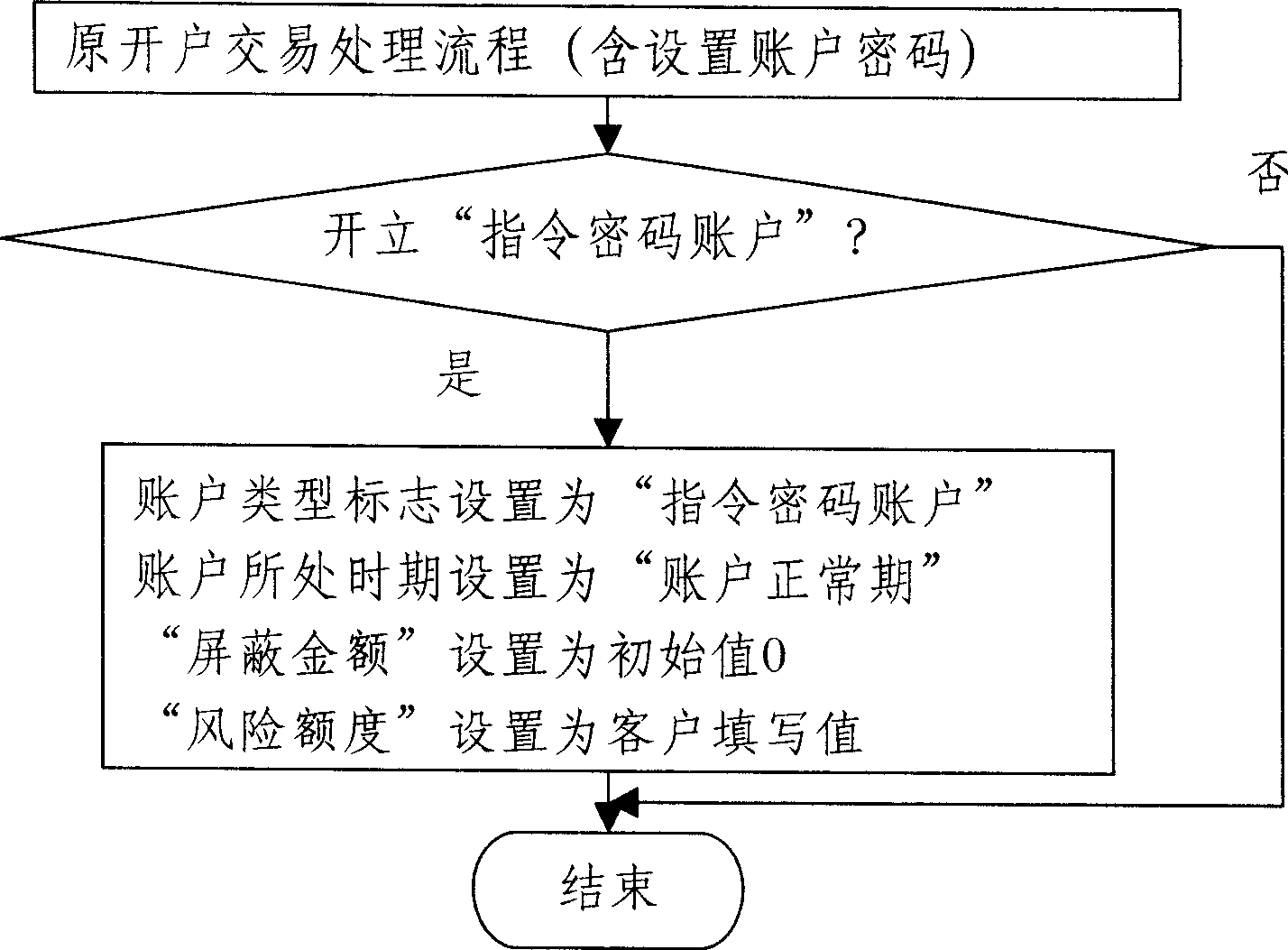
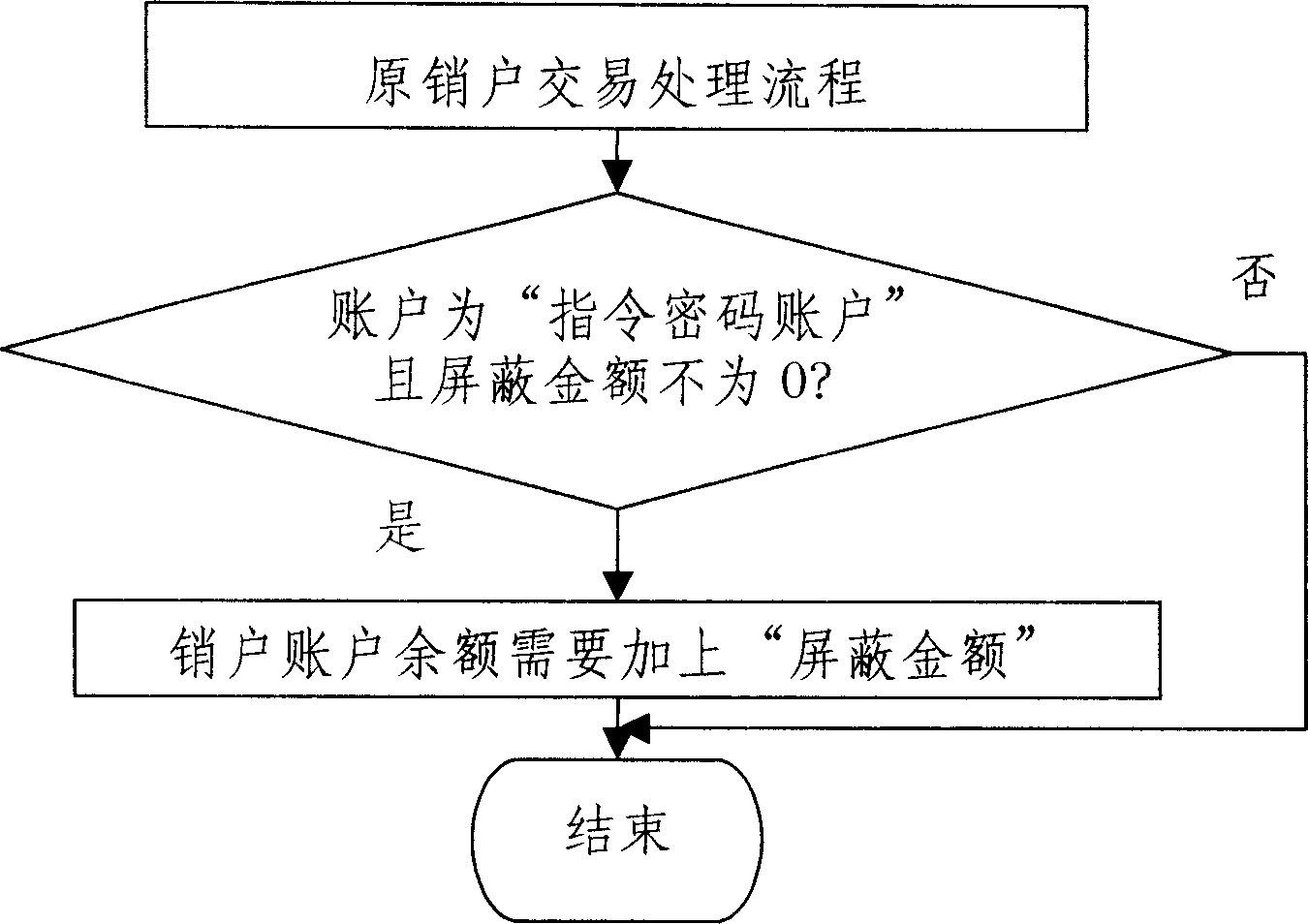
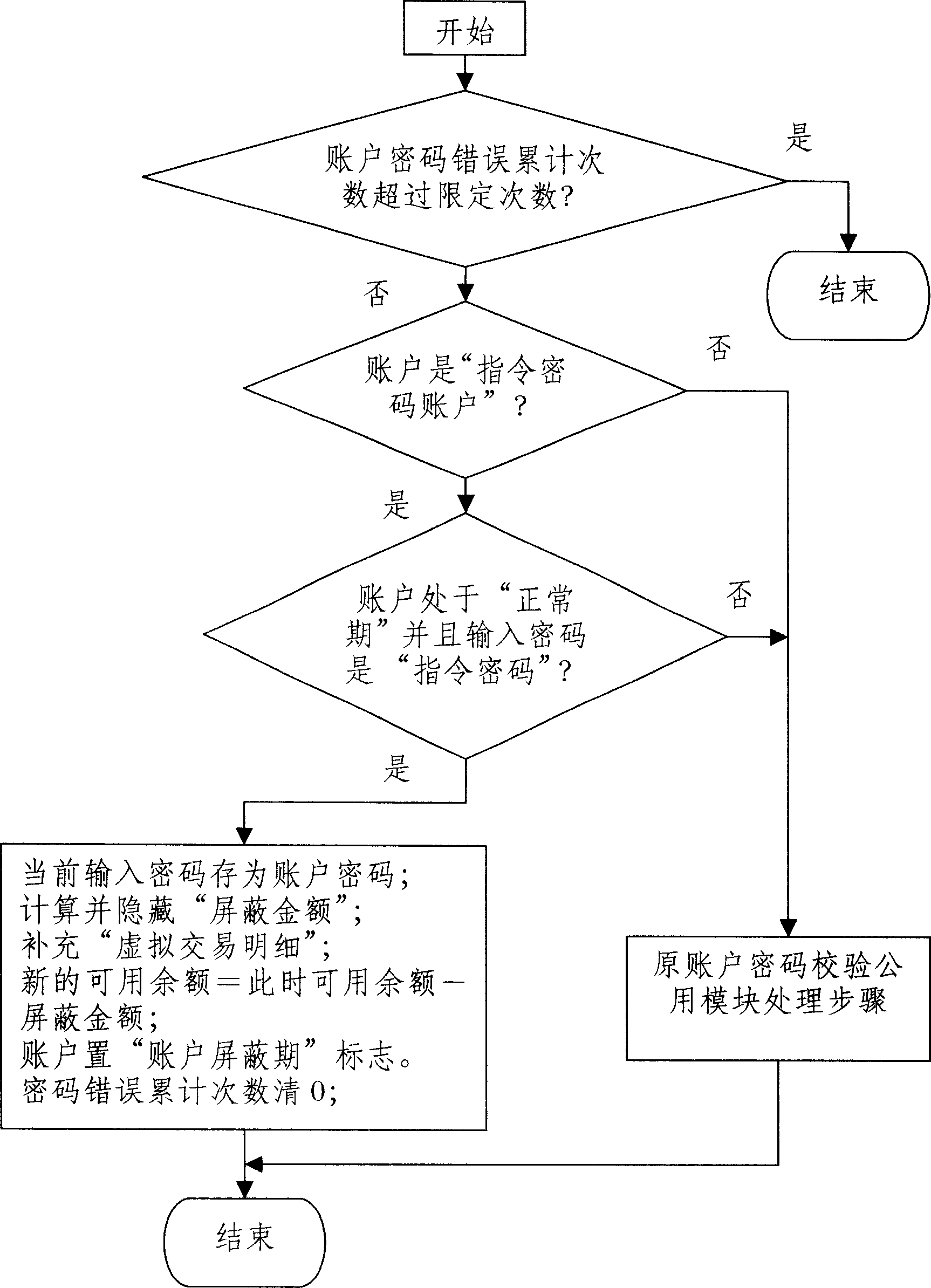
[0017] The principle of the invention: In order to solve the resource loss risk problem caused by the involuntary leakage of the password without changing the reserved single password method of the existing command password system, such as the risk of fund loss in the bank account, the invention proposes a command password The theory of the system hides the instructions in the input password, and the input of the real password, instruction password or wrong password corresponds to different results. When entering the command password, only part of the resources can be controlled—that is, part of the balance of the account; it is very secretive, and after involuntary leakage, it not only protects most of the account balance, but also ensures personal safety. At the same time, the present invention provides a practical algorithm for parsing instruction pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com