Full text search system based on ciphertext
A retrieval system and full-text technology, applied in the field of full-text retrieval systems based on ciphertext, can solve problems such as increased information volume and ciphertext information processing, and achieve the effects of ensuring secure retrieval, strong security, and high execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Below in conjunction with accompanying drawing and example the present invention is described in further detail.
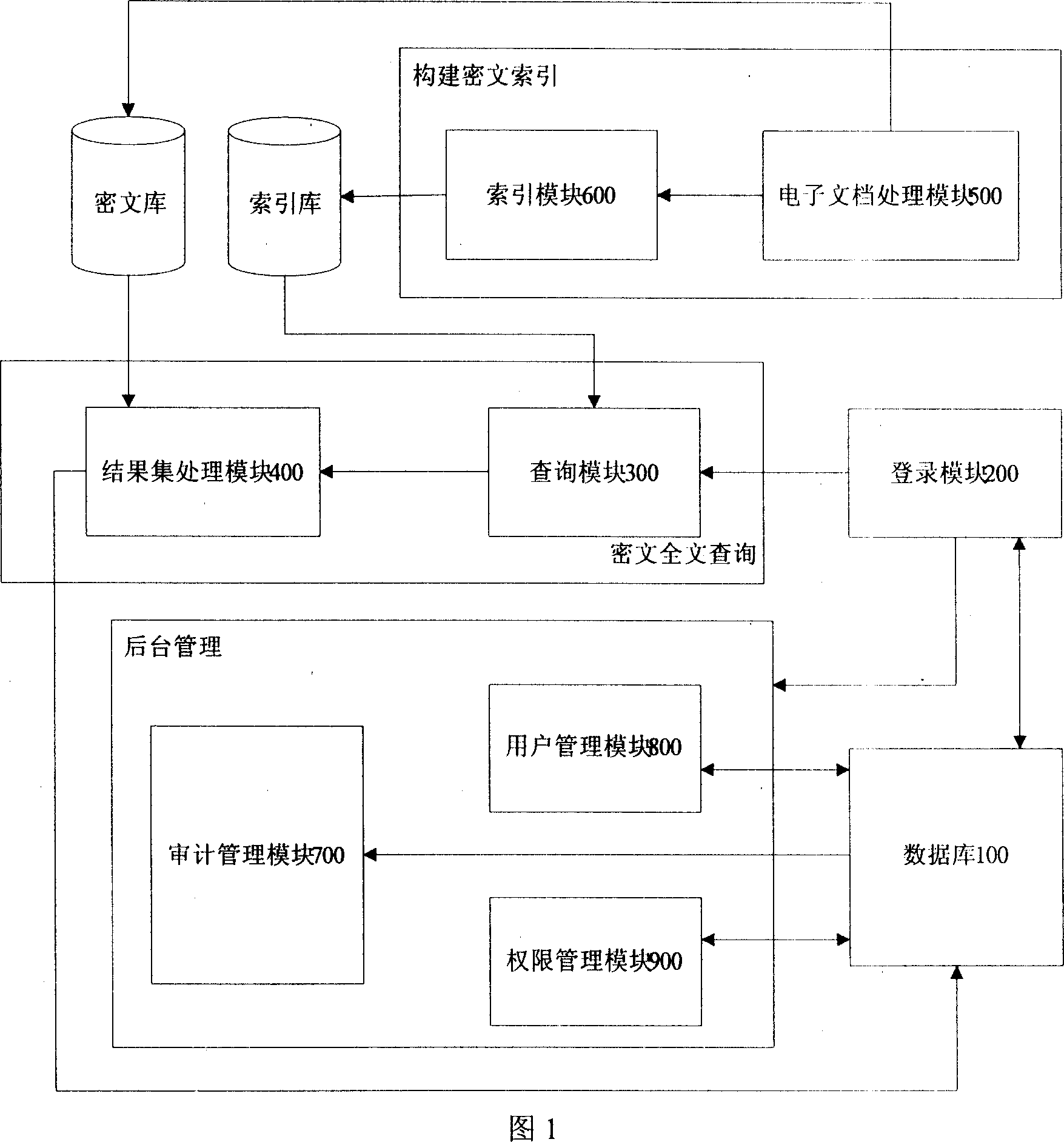
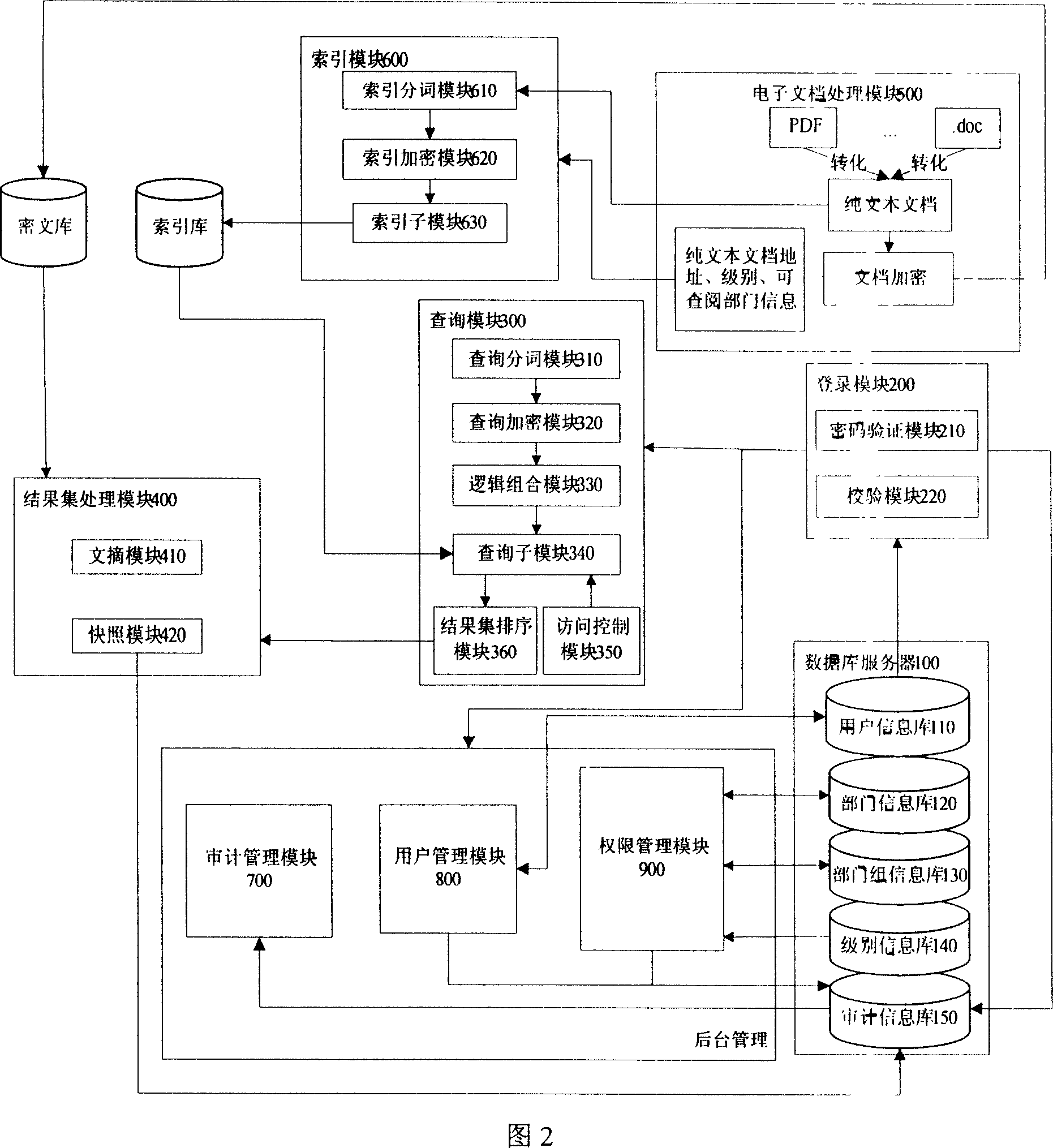
[0028] As shown in Figure 1, the function of the system of the present invention can be divided into: build ciphertext index, ciphertext full-text search and background management, this system comprises database 100, login module 200, query module 300, result set processing module 400, electronic document Processing module 500 , index module 600 , audit management module 700 , user management module 800 and authority management module 900 .
[0029] The database 100 is used for storing information on users and user rights.
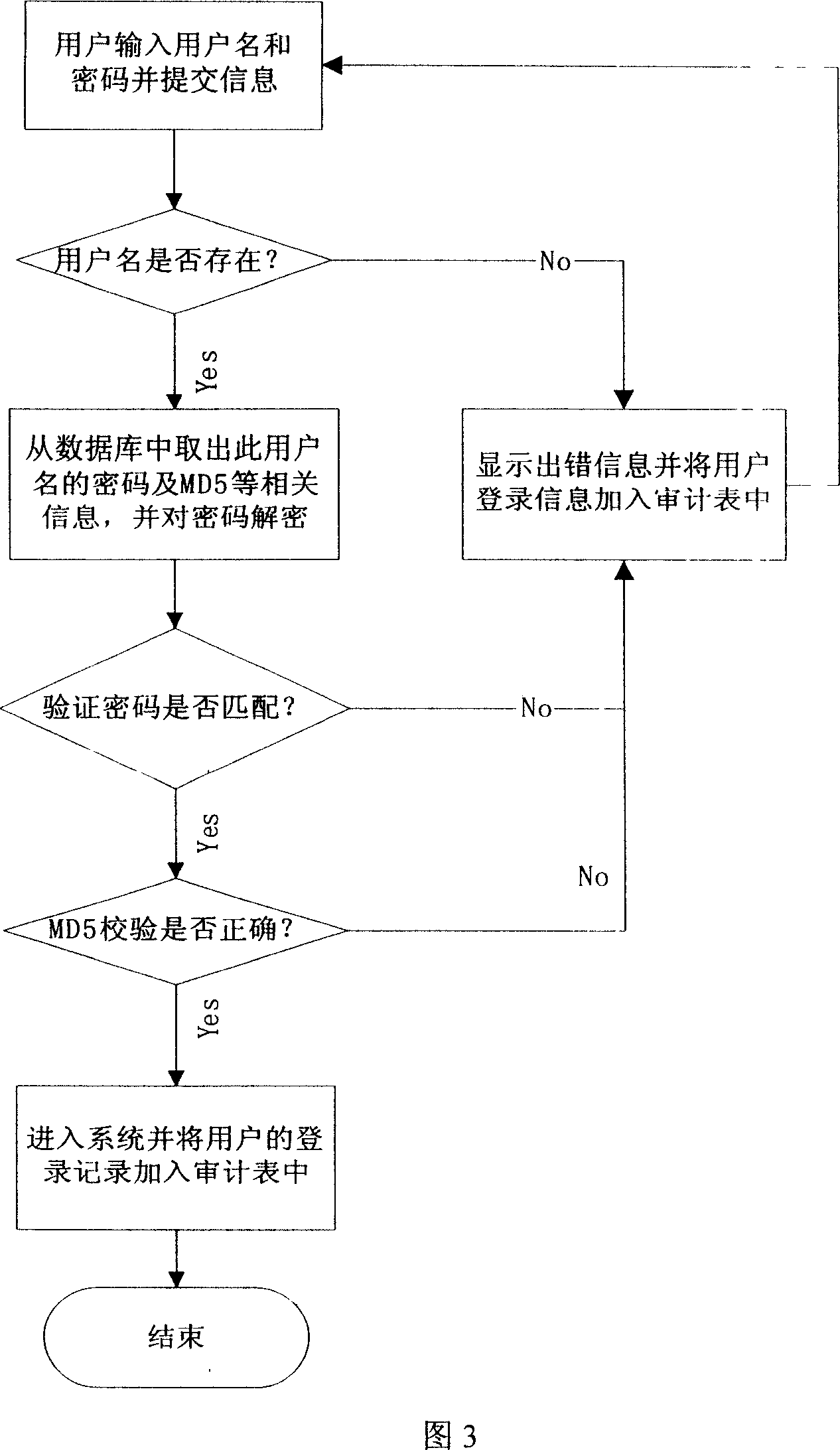
[0030] The login module 200 is used to receive the service request from the user input information, and verify the service request by interacting with the information of the database 100. If the verification is successful, the user is allowed to enter the system, and at the login module 200, the relevant information of the user in the d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com