Method for estimating distinguish of voice, registering and validating authentication of speaker and apparatus thereof
A speaker authentication and resolution technology, applied in the field of information processing, can solve the problems of weak speaker resolution, inconvenient, checking password validity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Various preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
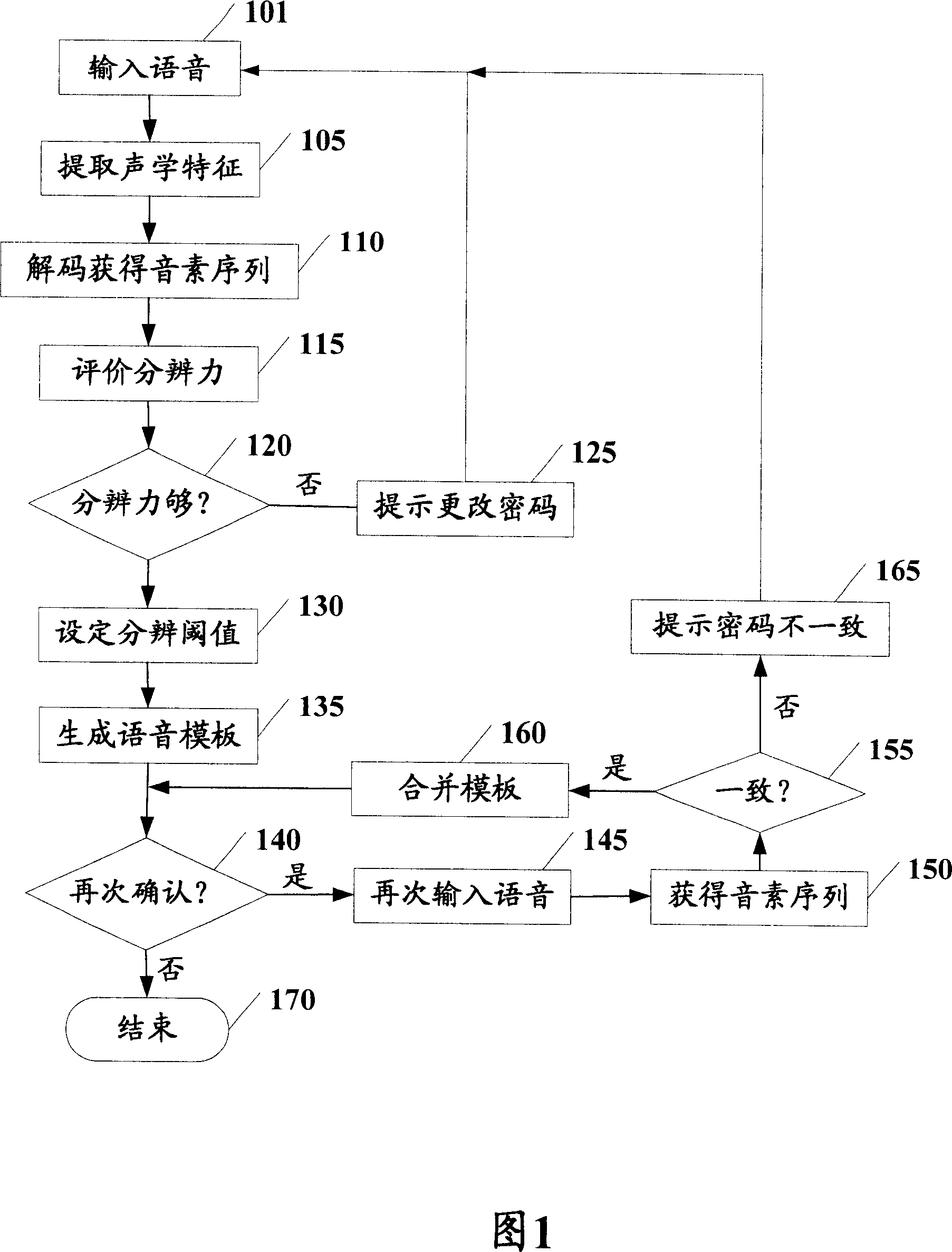
[0021] FIG. 1 is a flowchart of an enrollment method for speaker authentication according to an embodiment of the present invention. As shown in FIG. 1 , first at step 101 , a voice including a password uttered by a speaker is input. Here, in this embodiment, it is not necessary for the system administrator or developer and the speaker (user) to agree on the content of the password in advance as in the prior art, but the content of the password can be determined by the user and then spoken out.
[0022] Next, in step 105, acoustic features are extracted from the speech. Specifically, in this embodiment, an MFCC (Mel Frequency Cepstrum Coefficient, Mel Frequency Cepstral Coefficient) method is used to represent the acoustic features of speech. However, it should be pointed out that the present invention is not particularly limited to t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com