Automatic weapon user identification and safety module
a technology for user identification and safety modules, applied in the direction of safety arrangements, weapons components, electrical equipment, etc., can solve the problems of reducing the effectiveness of firearms in emergency situations, operation by a person, injury or death,
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
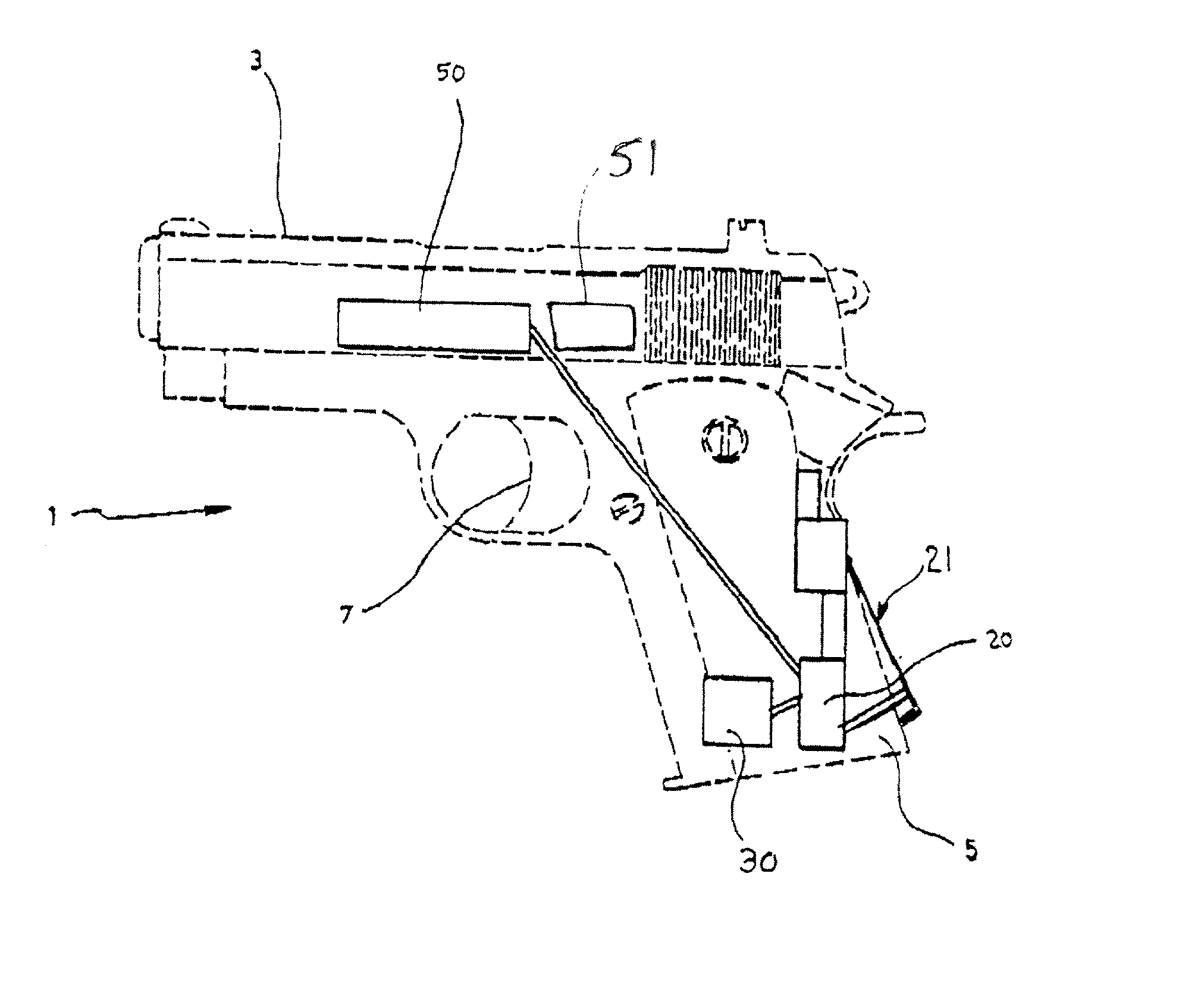
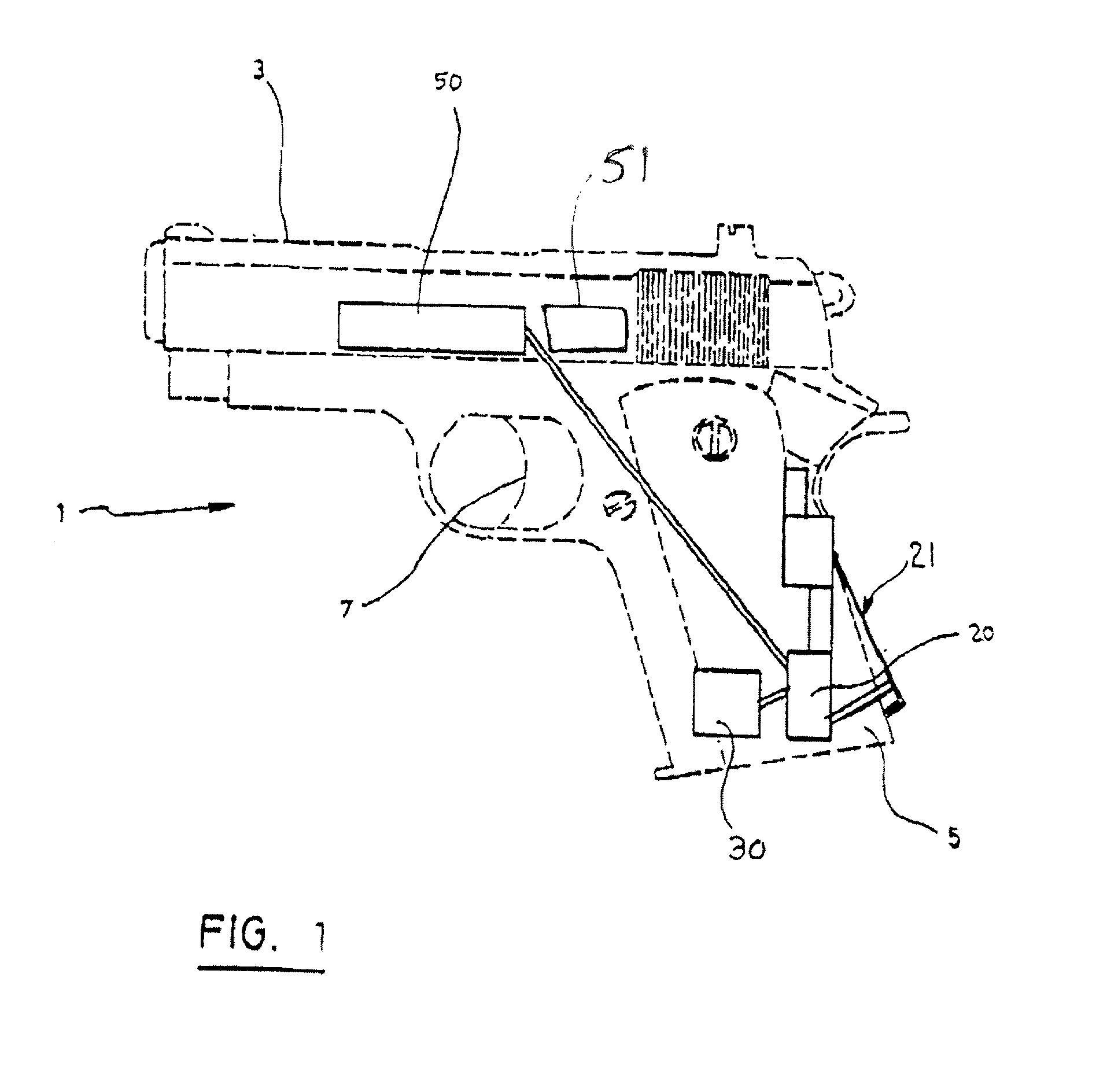
[0021] As mentioned above, the invention is directed to an automatic safety system for a weapon 1. In the context of the present invention, weapon includes firearms such as rifles, handguns, pistols, etc., and also includes stun guns, and, more broadly, any weapon which includes a handgrip for a user to grip. The invention may easily be adapted to any type of weapon 1, with the proper modifications. For the purposes of explaining the functioning of the present invention, it will be described as incorporated in a handgun 1, shown in FIG. 1. The handgun 1 has a barrel 3, a handgrip 5, a trigger 7 and a firing mechanism, all of which are well known. However, it should be understood that the following description is equally applicable for any type of weapon.
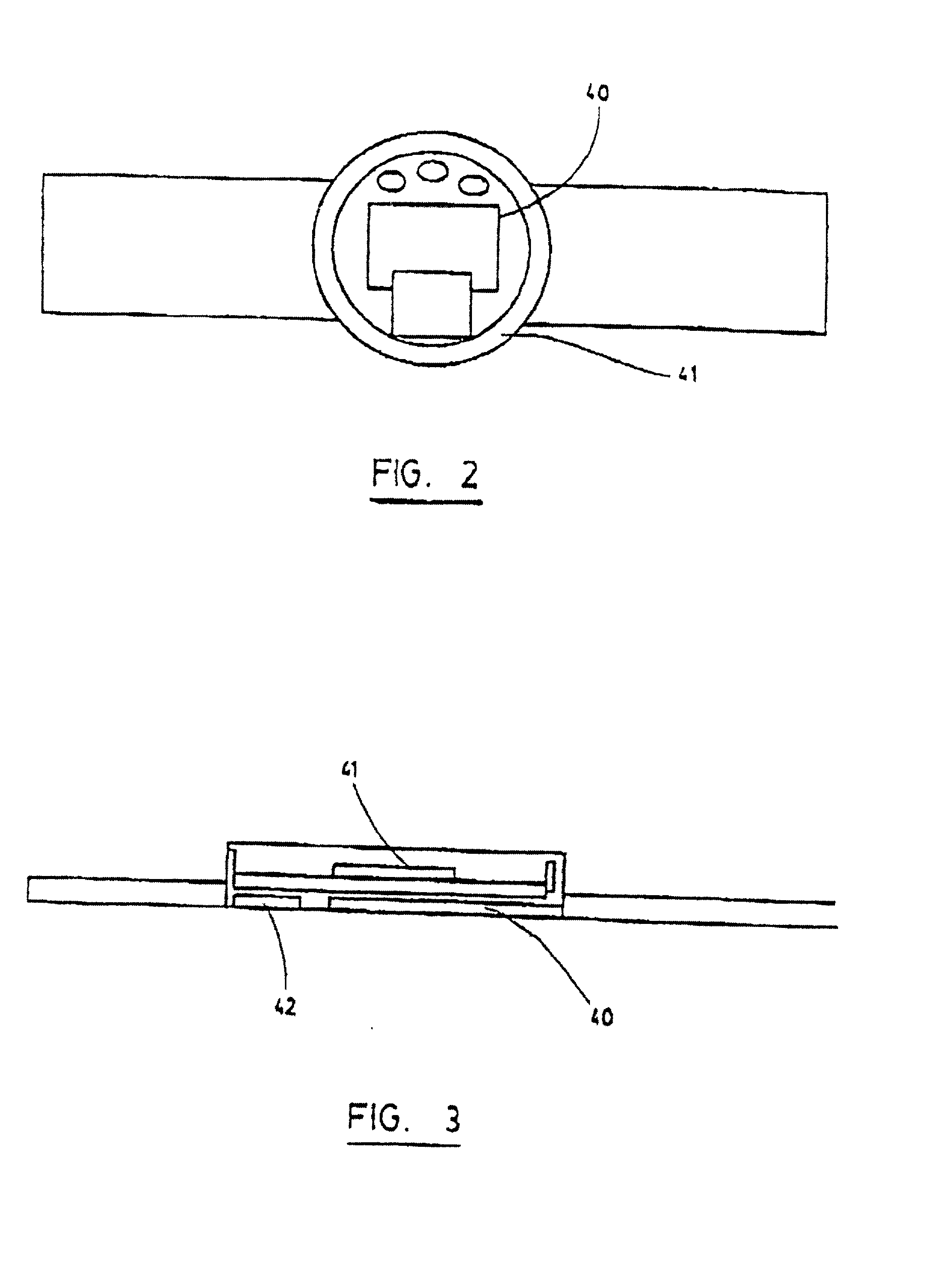
[0022] The system according to a preferred embodiment thereof includes a unit which is integrated into the firearm 1, and at least one token 40 which is remote from the firearm 1. The unit which is integrated into the firearm is some...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com