Information security threat identification, analysis, and management
a technology of information security and threat identification, applied in the field of information security, can solve the problems of wasting workers' time, serious loss in many ways, and compromising the use of electronic communication, and achieve the effect of facilitating the acquisition of information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] In the following description of the preferred embodiment, reference is made to the accompanying drawings that form a part hereof, and in which is shown by way of illustration a specific embodiment in which the invention may be practiced. It is to be understood that other embodiments may be utilized and structural changes may be made without departing from the scope of the present invention.
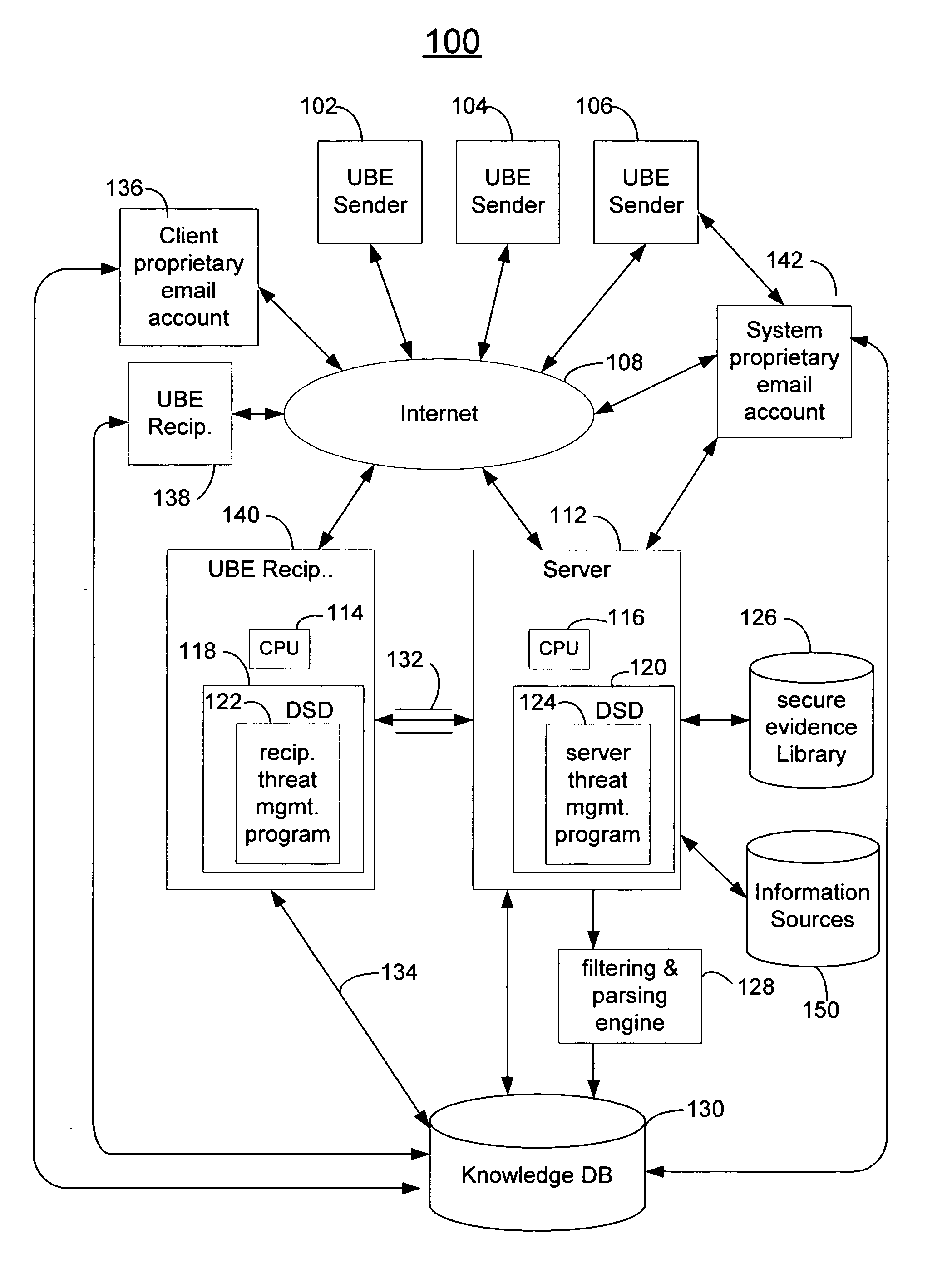
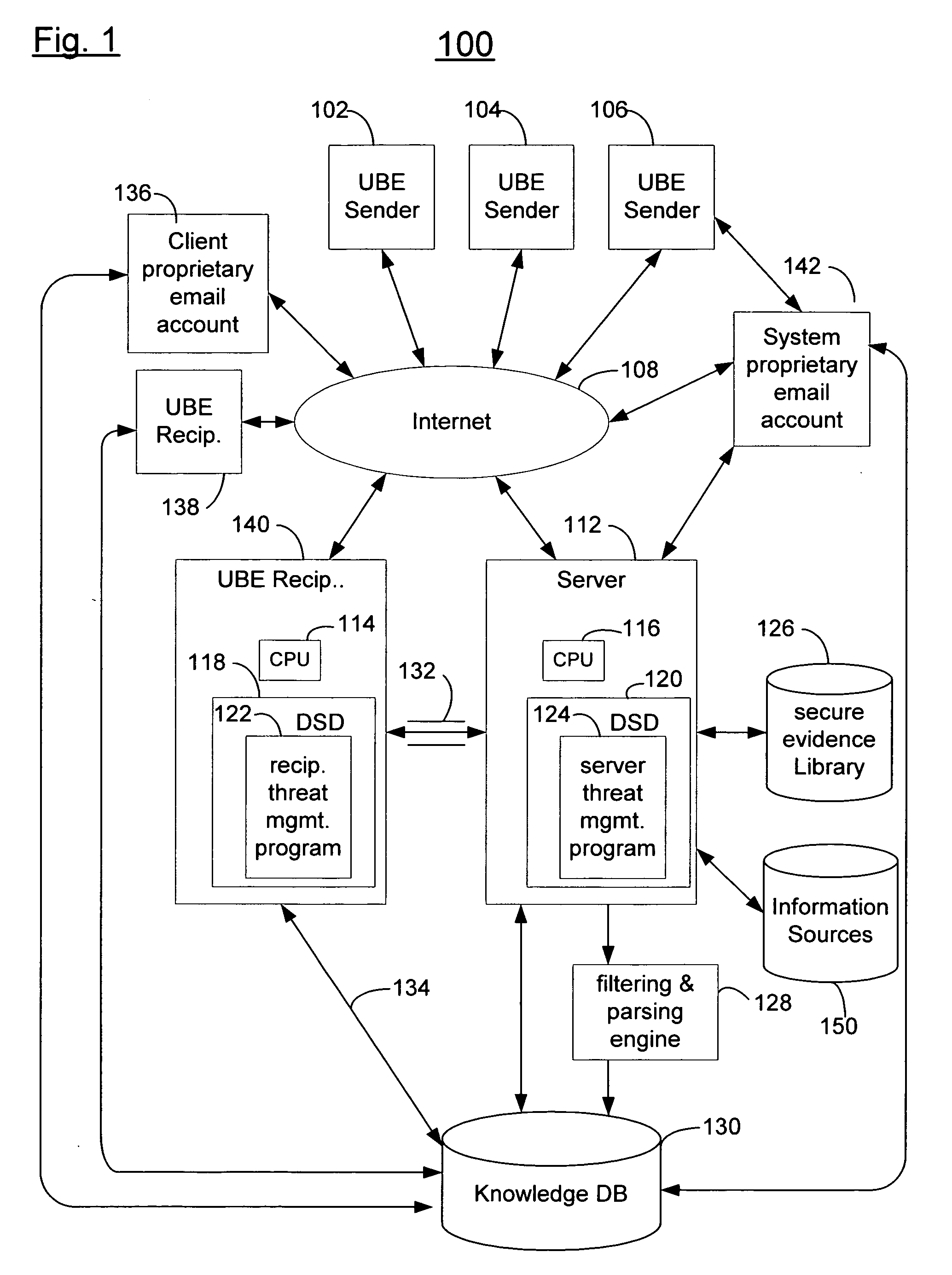
[0037]FIG. 1 is a block diagram of distributed computer system, according to an embodiment of the invention. In computer system 100 depicted in FIG. 1, multiple UBE sender computers 102, 104, 106, multiple UBE recipient computers 138, 140, one or more server computers 112, a system proprietary email account 142 run by the operator of system 100, and a client proprietary email account 136 run by a client of the operator of system 100, are connected to a network such as the Internet 108. Server computer 112 serves as a mail aggregator as discussed below. One or more secure evidence libraries...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com