Systems and methods for event detection
a technology of event detection and event analysis, applied in error detection/correction, instruments, computing, etc., can solve the problems of increasing complexity of computer use, increasing the difficulty of consumer phone calls to help centers regarding spyware adware, and increasing the difficulty of finding
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
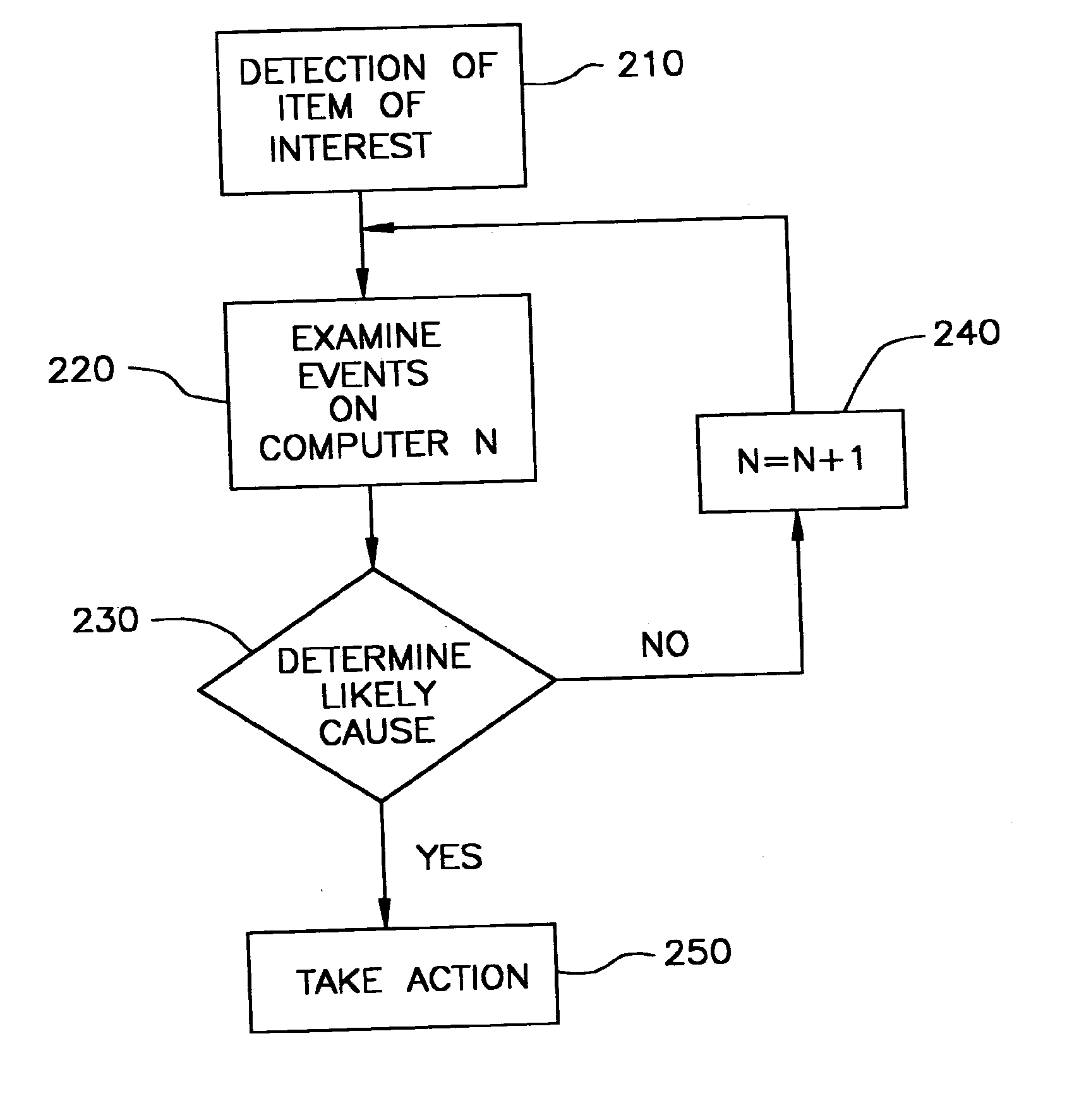
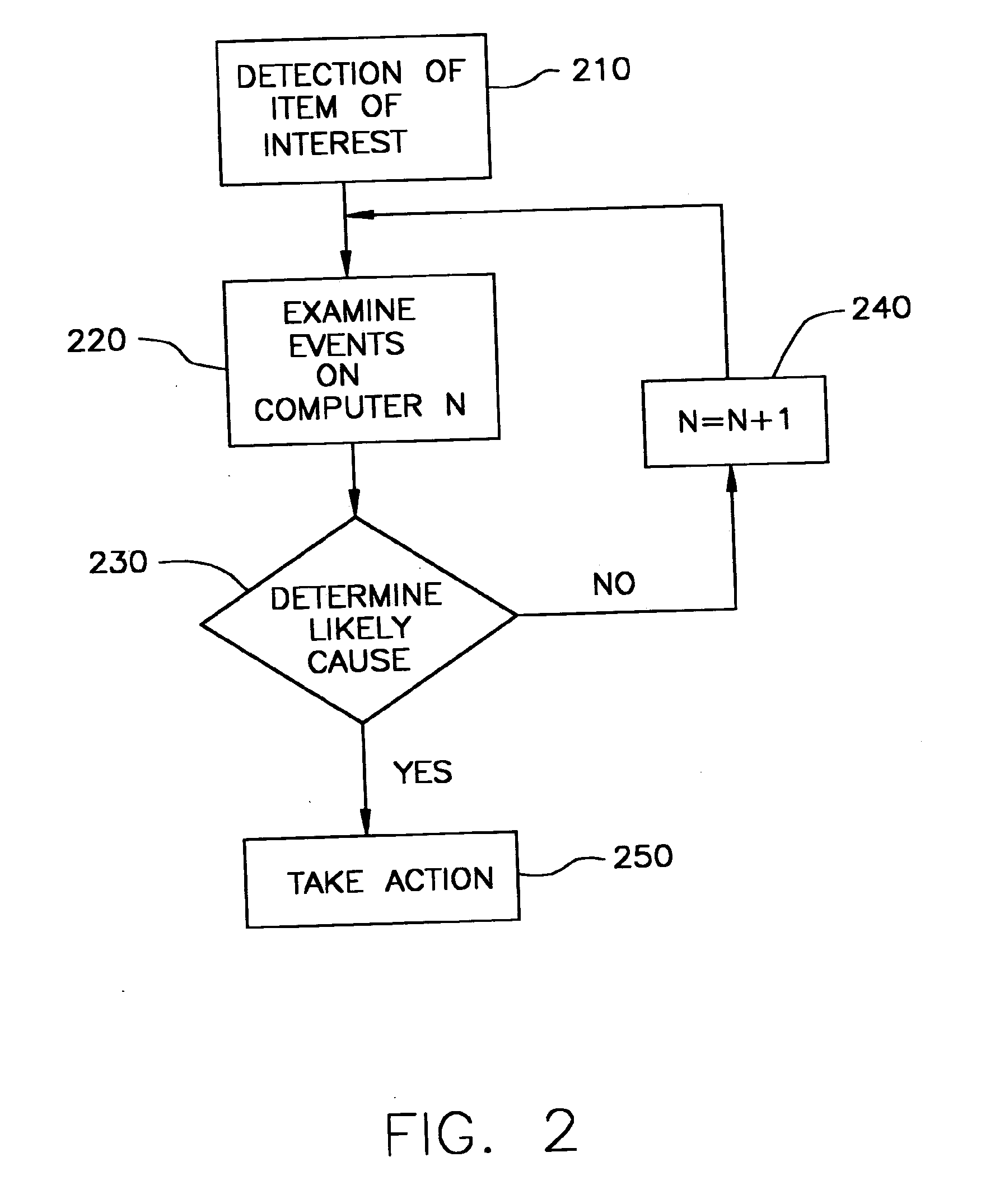
[0020]The present invention provides a detection service that facilitates the automatic localizing the cause of items of interest associated with computer systems.
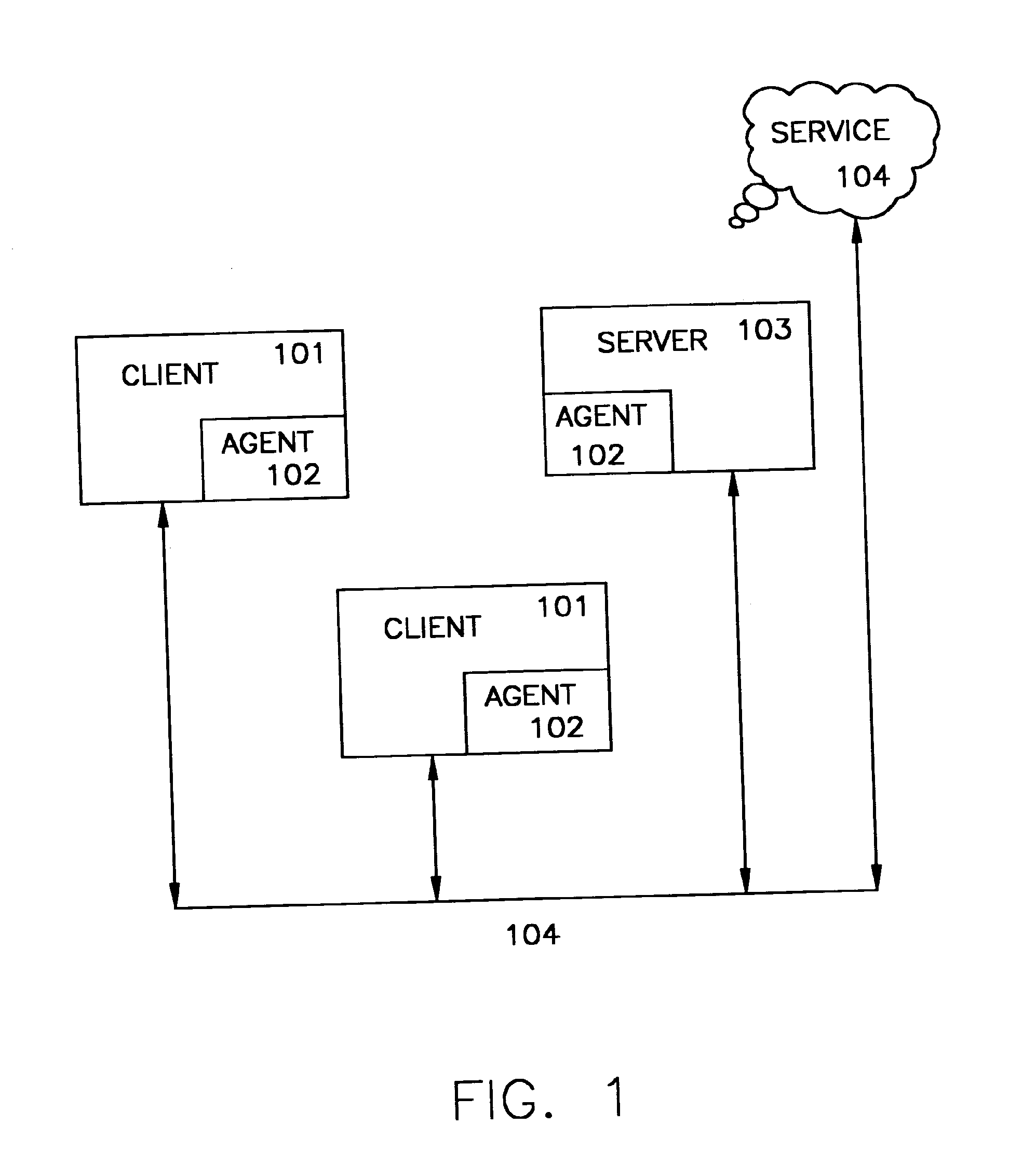
[0021]With reference to FIG. 1, there is provided in accordance with at least one presently preferred embodiment of the present invention an agent 102 that is installed on a client 101 or server system 103 and that is responsible for tracking specific events. These events may be caused by software, the user, services provider, company, or group of users, and include, for example, such trackable events as mouse events, keyboard events, browser requests via http and ftp, mail events via SMTP, and various other events that could affect the functioning and response of a user's system, such as system 101. Often, the events of most interest will be those that may affect the system in a negative fashion, such as associated with adware, spyware, software installations, and viral and nonviral threats. However, these items of intere...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com