Method of and system for encryption and authentication
a technology of electronic encryption and authentication, applied in the field of telecommunications, can solve the problems of introducing and providing an exponential increase in complexity and security of systemic authorization processes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
example
Application to an Authorization Process in an Online Music Store Card
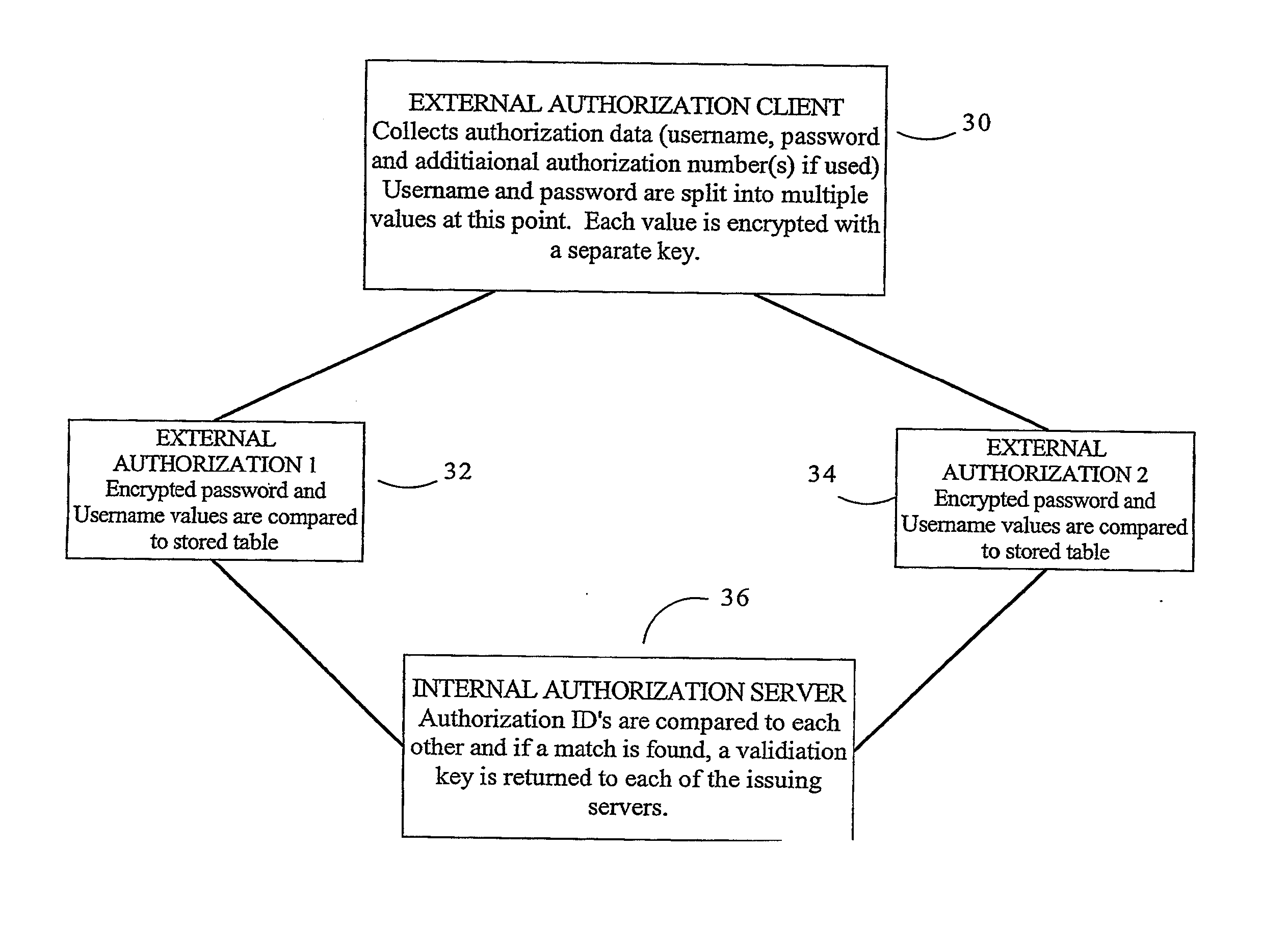
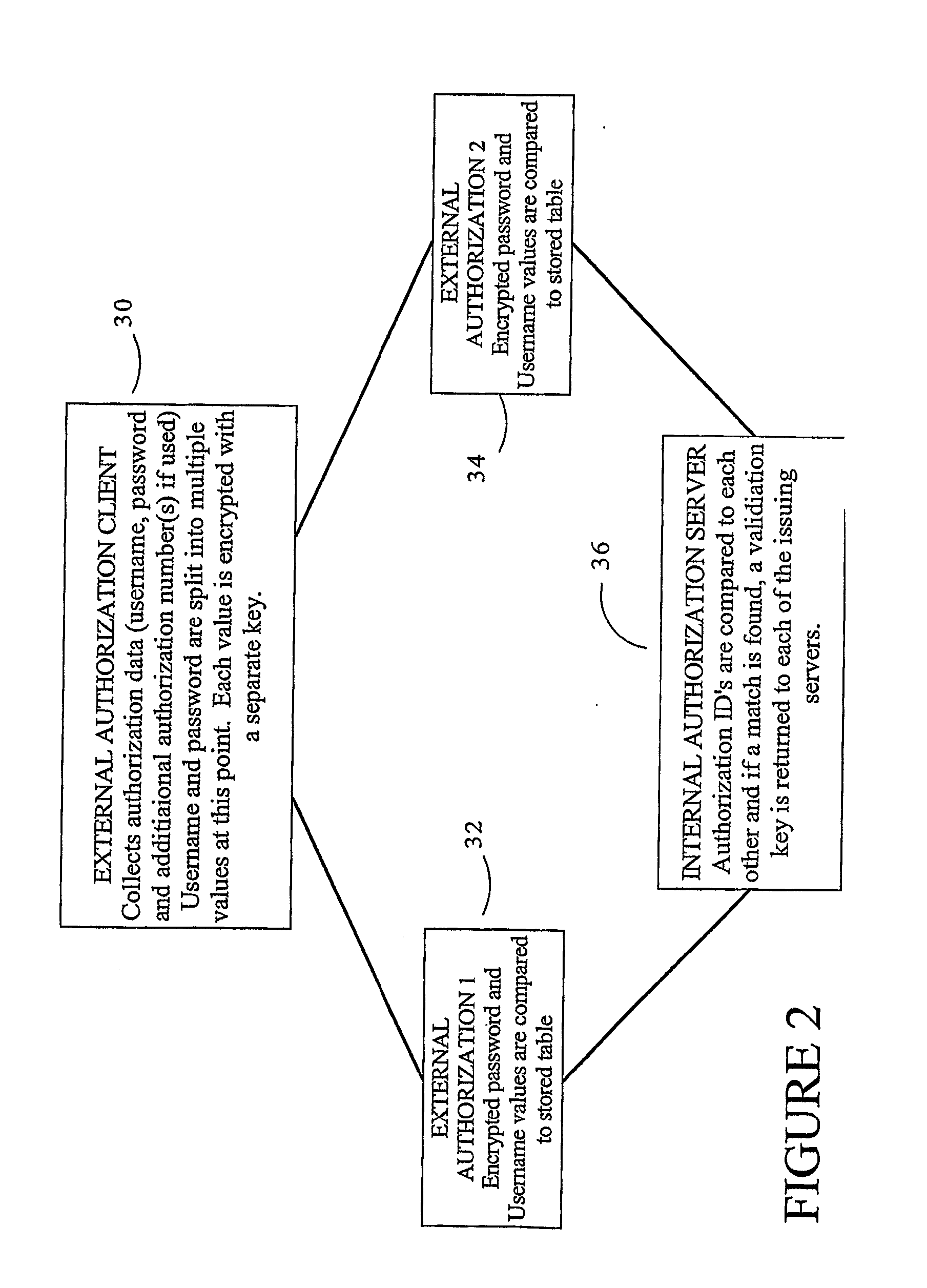
[0071]A User accesses an online music store to make a purchase. After selecting “checkout” in his online shopping cart, the User is prompted for a User name, password and card number (the User's music card was obtained via mail or at physical location. The User could also use credit or debit card for the transaction). The User then enters his User name, password and card number. The User name and password are encrypted using his card number as a seed value (further modified by the use of a time stamp), using, for example, public key based encryption such as PGP. The encrypted User name and password are joined into a single value, then split into byte-sized chunks. The algorithm used to do this is based on byte-generation via alternating bits, starting at each end of full value, the first bit being taken from the beginning of the string, the second bit is the last bit in the string, the third bit is the second in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com