Protection against unsolicited communication for internet protocol multimedia subsystem
a technology of multimedia subsystems and internet protocol, applied in special service provision of substations, instruments, digital computers, etc., can solve the problems of high network workload and inability to detect unsolicited calls, and achieve the effect of high network workload, high performance of puci systems, and inability to d
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
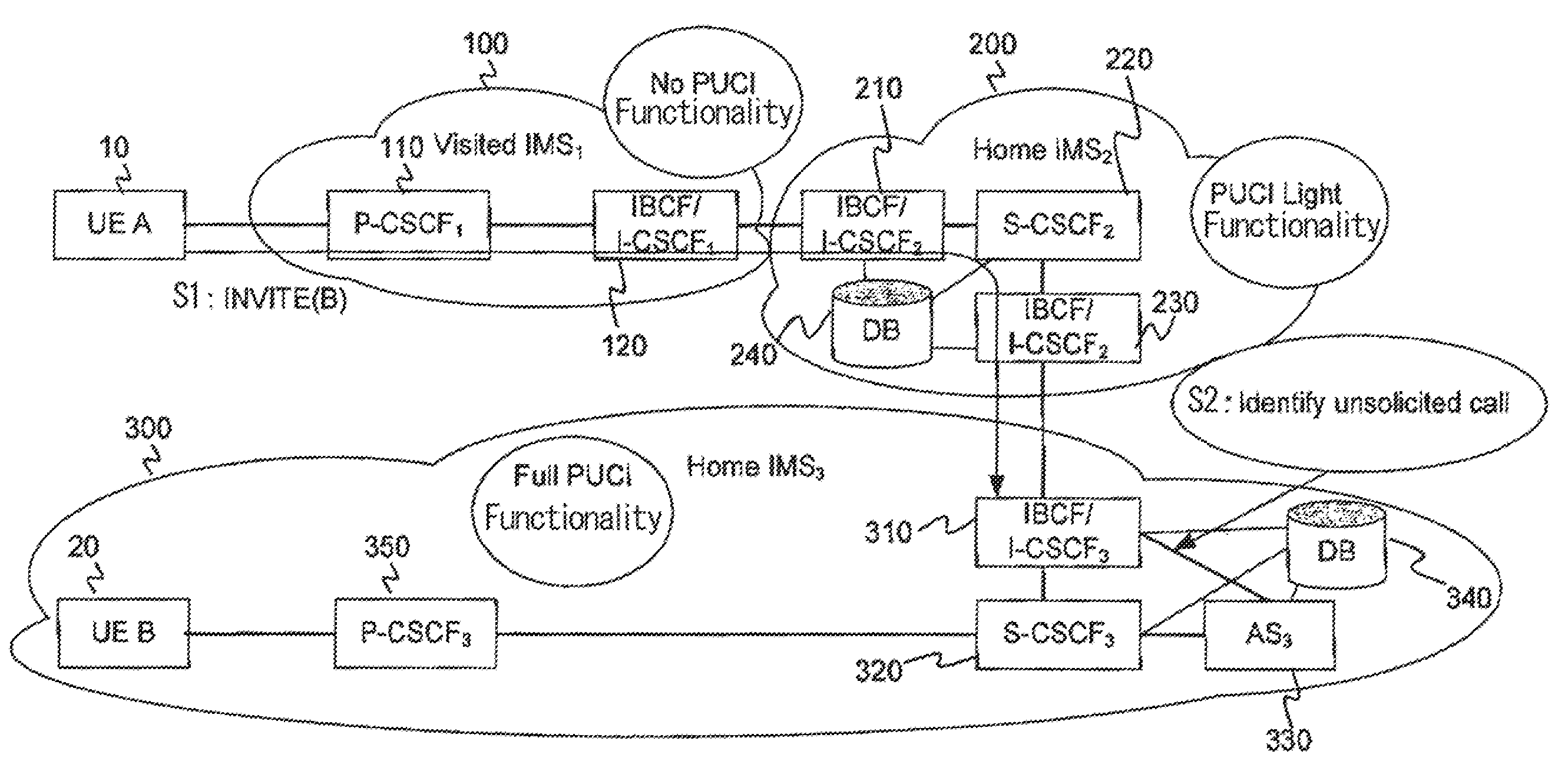
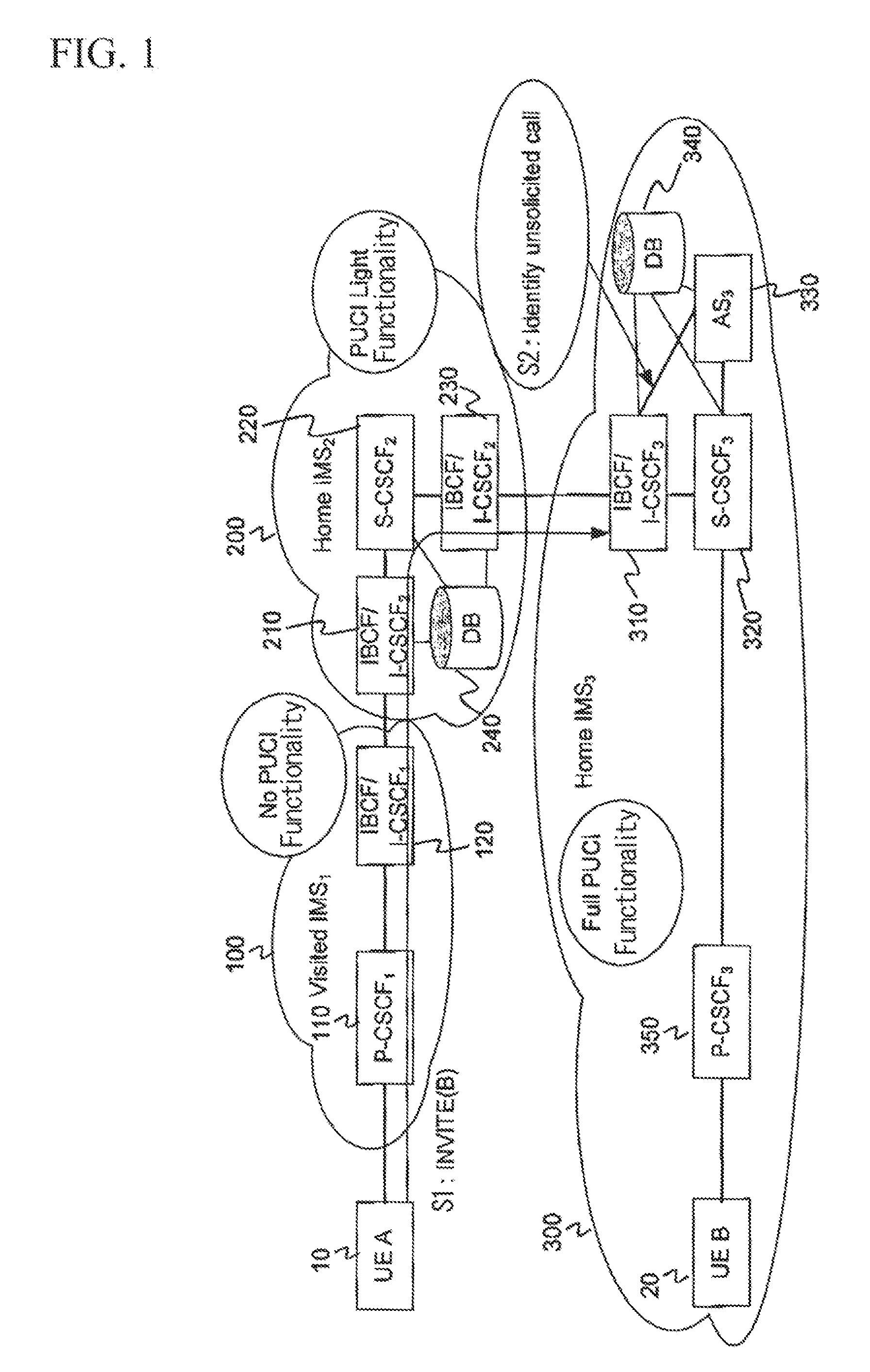
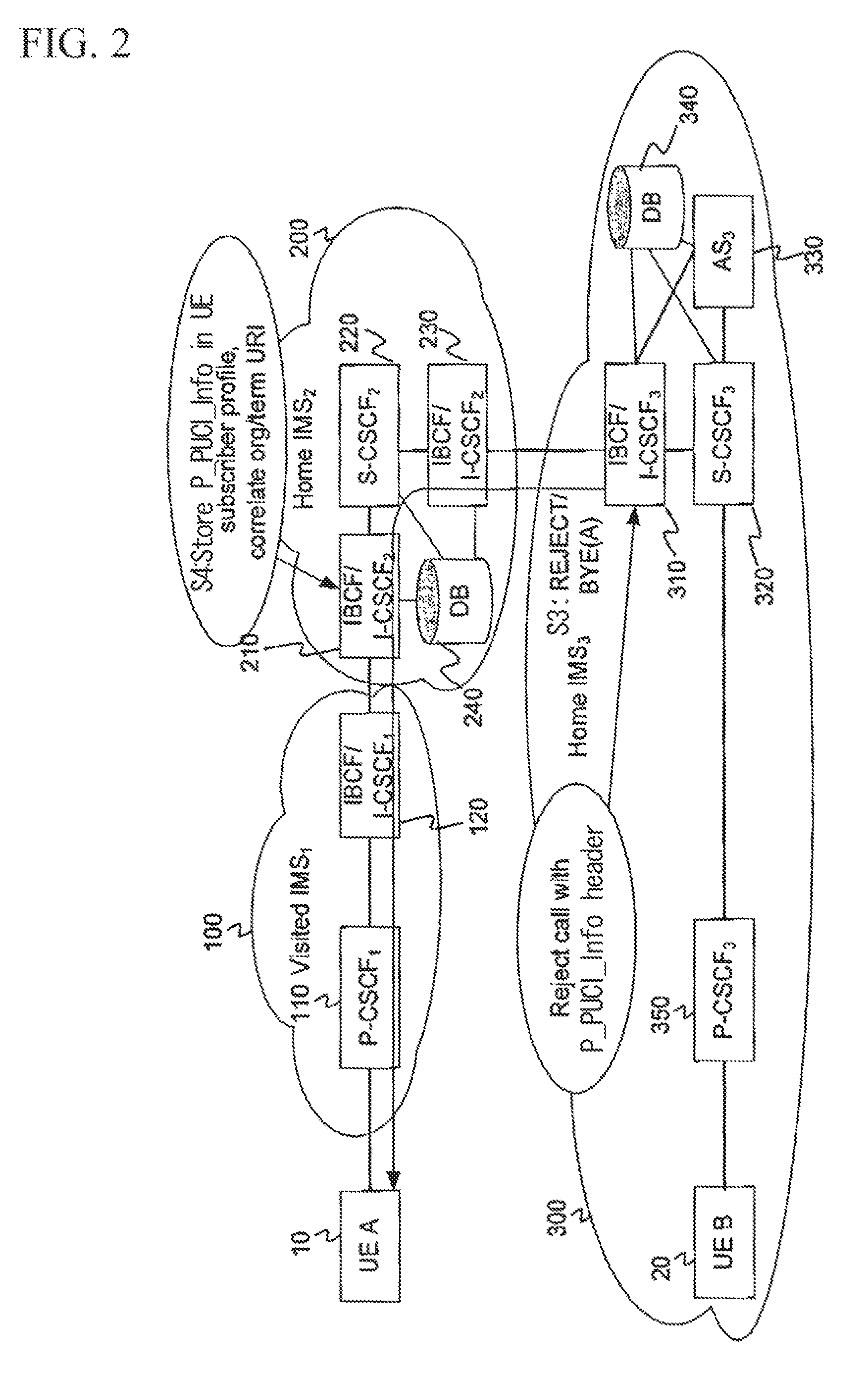
[0021]The overall PUCI functionality is reduced to a limited functionality which is directly implemented as a part of the IMS. The present invention seeks a method as to how to exchange the PUCI information related to specific calls among the interconnected networks, thus directly blocking further unsolicited communications.
[0022]The present invention is designed to implement one of global operator policy (OP) databases in the first contact point of the user equipment (UE) to the IMS, and the proxy call session control function (P-CSCF) or the interconnect border control function (IBCF) and / or the interrogating call session control function (I-CSCF) in the case of the IMS peering. The PUCI-light functionality is implemented not only as a part of the core IMS functionality (i.e. an integral part of the P-CSCF, I-CSCF, S-CSCF, and IBCF) but also as any other SIP-based systems (e.g. SIP proxy / server, SBC), thus achieving the PUCI-light functionality at the edge of the network.
[0023]The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com