Method for searching and killing virus and computer therefor
A computer and virus technology, applied in computer security devices, computing, instruments, etc., can solve problems such as system vulnerability weakening actual effects, inability to perform anti-virus operations, affecting the normal operation of anti-virus software, etc., to achieve the effect of ensuring security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be described in further detail below in conjunction with the accompanying drawings.
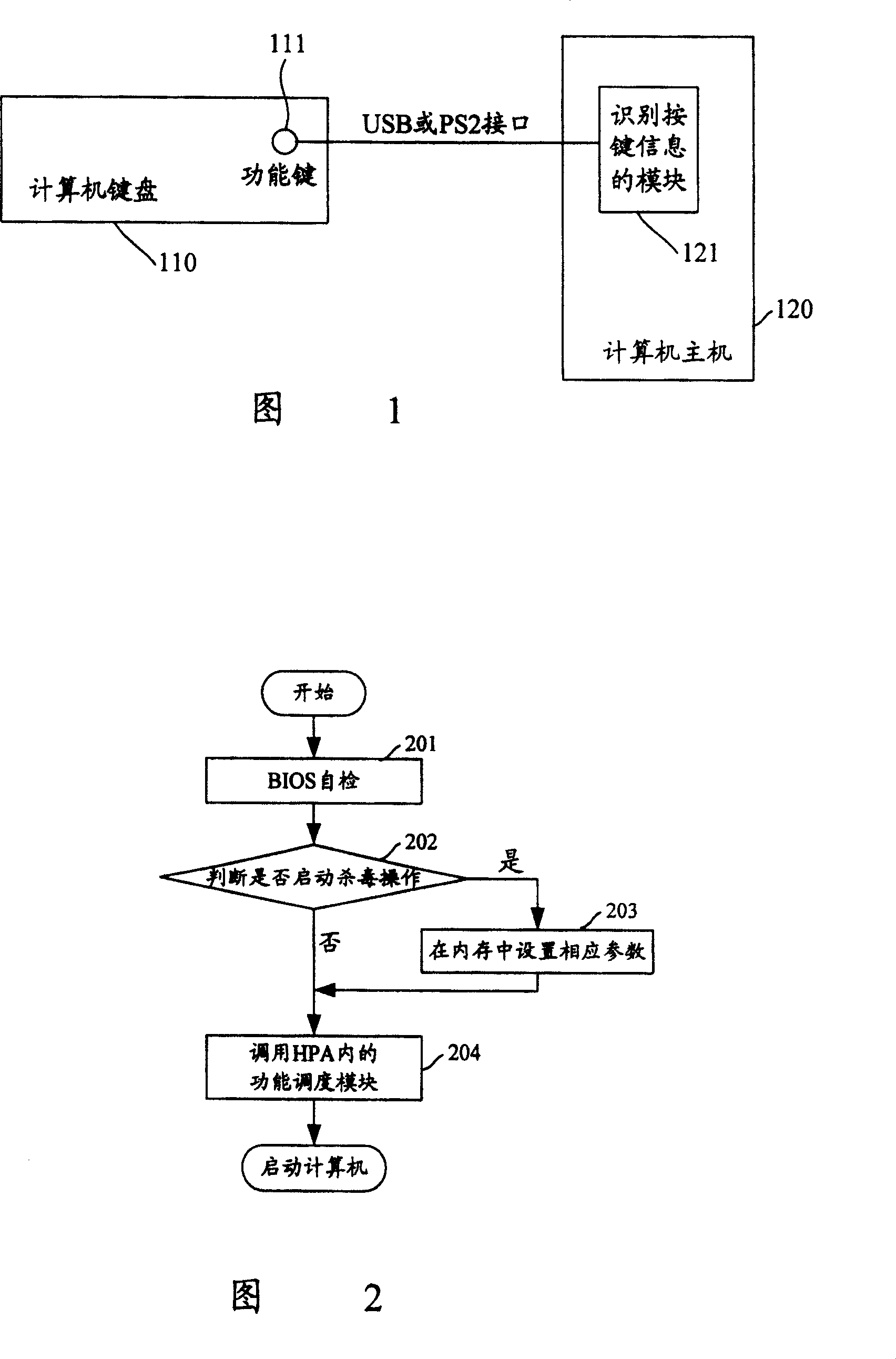
[0026] FIG. 1 is a schematic diagram of an embodiment of a computer for detecting and killing viruses. In this embodiment, a function key 111 for directly starting the antivirus function is added on the keyboard 110 of the computer. The module 121 for identifying key information can identify the added function key 111 for directly starting the antivirus function. Wherein, the function key 111 and the module 121 for identifying key information can be connected through a PS2 interface, or a USB interface, or a wireless interface, or a 1394 interface, or other interfaces, and the connection method is not limited here. The module 121 for identifying key information includes a module for identifying key information in the BIOS and a module for identifying key information in the operating system.
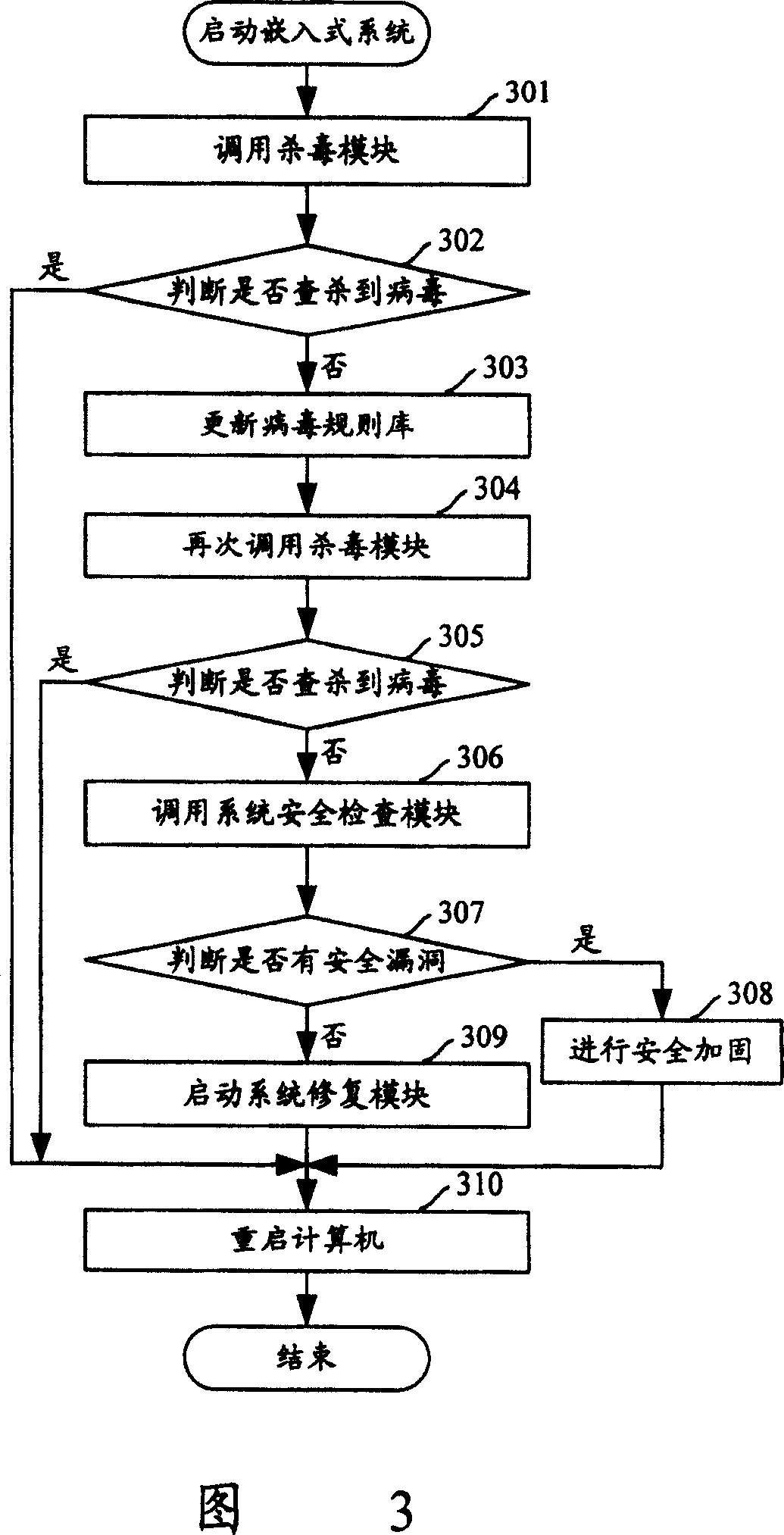
[0027] In this way, regardless of whether the operating system ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com