Method for processing wireless network node buffering data package
A wireless network and processing method technology, which is applied in the field of wireless network node buffer data packet processing, can solve problems affecting transmission efficiency, etc., and achieve the effect of sacrificing computing resources, small code space, and fast solution speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0035] Embodiment 1: A splicing method with a fixed output packet length.
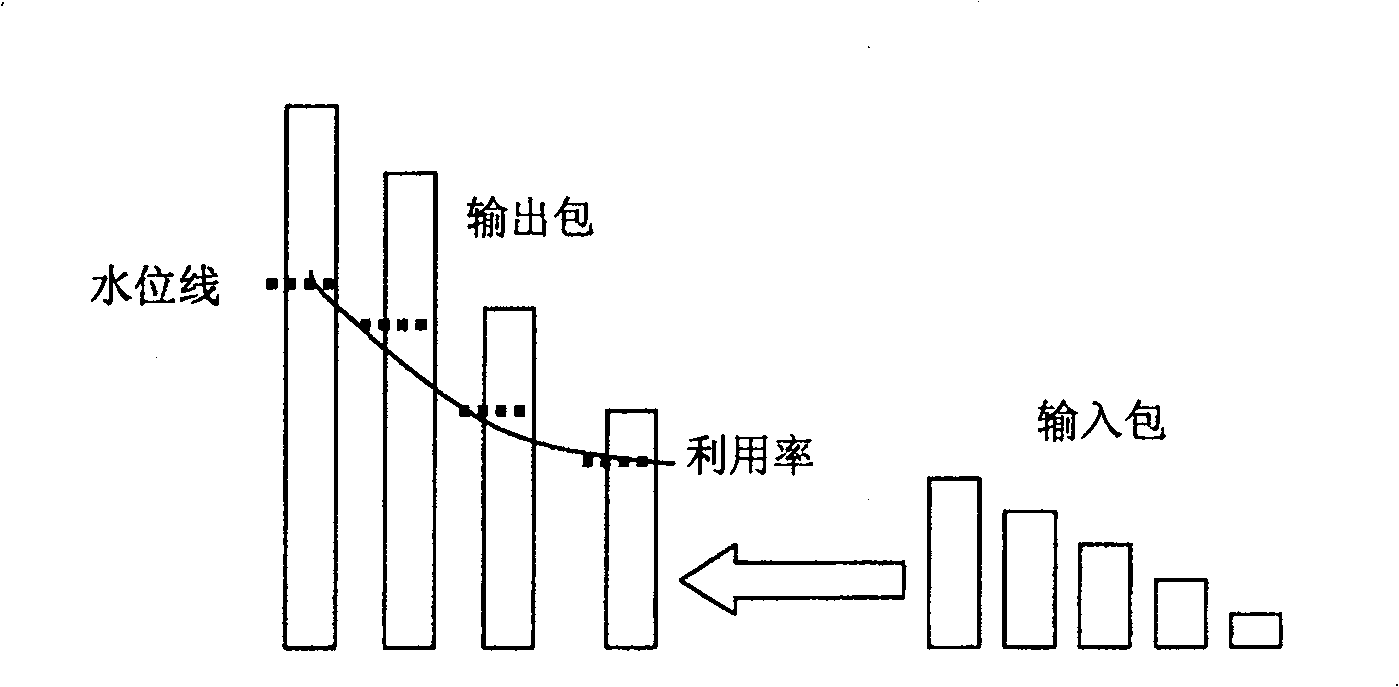
[0036] When the length of the output packet is fixed, to realize the splicing of data packets is to solve the optimal splicing scheme of splicing all n input packets into an output packet of length L. In the method of the present invention, the utilization rate is used as the criterion for judging the effect of data splicing. The utilization rate is the ratio between the total length of the input packet data and the total length of the output packet data, and the higher the utilization rate, the better the effect of the splicing scheme is obviously.
[0037] For this kind of data packet splicing problem, a general greedy algorithm can be used to solve it, that is, each time the current largest input packet is spliced into the output packet, and when the output packet can no longer be accommodated, another new output packet is spliced into it until All input packets are processed. Although this me...
Embodiment 2
[0062] Embodiment 2: Splicing method with multiple output packet lengths.
[0063] In the method of splicing input packets into output packets, the output packet length may not be unique, but there are multiple optional output packet lengths. When there are multiple output packet lengths to choose from, it is necessary to comprehensively consider possible combinations of splicing input packets into output packets of different lengths, so there are multiple search branches. There are two ways to search: depth-first traversal and breadth-first traversal. Depth-first, after the output packet of one length is completely scanned, it goes to the next one. Breadth-first is to scan in parallel in turn on output packets of various lengths according to certain switching rules. The present invention adopts multi-watermark heuristic search algorithm, such as image 3 As shown, the multi-watermark heuristic search algorithm is a breadth-first approach. The method sets a global lower li...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com