A method for improving stability of 802.1X authentication equipment
A technology for authentication equipment and stability, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as increasing equipment costs, failing to meet business development needs, reducing the number of access users, etc. The effect of scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
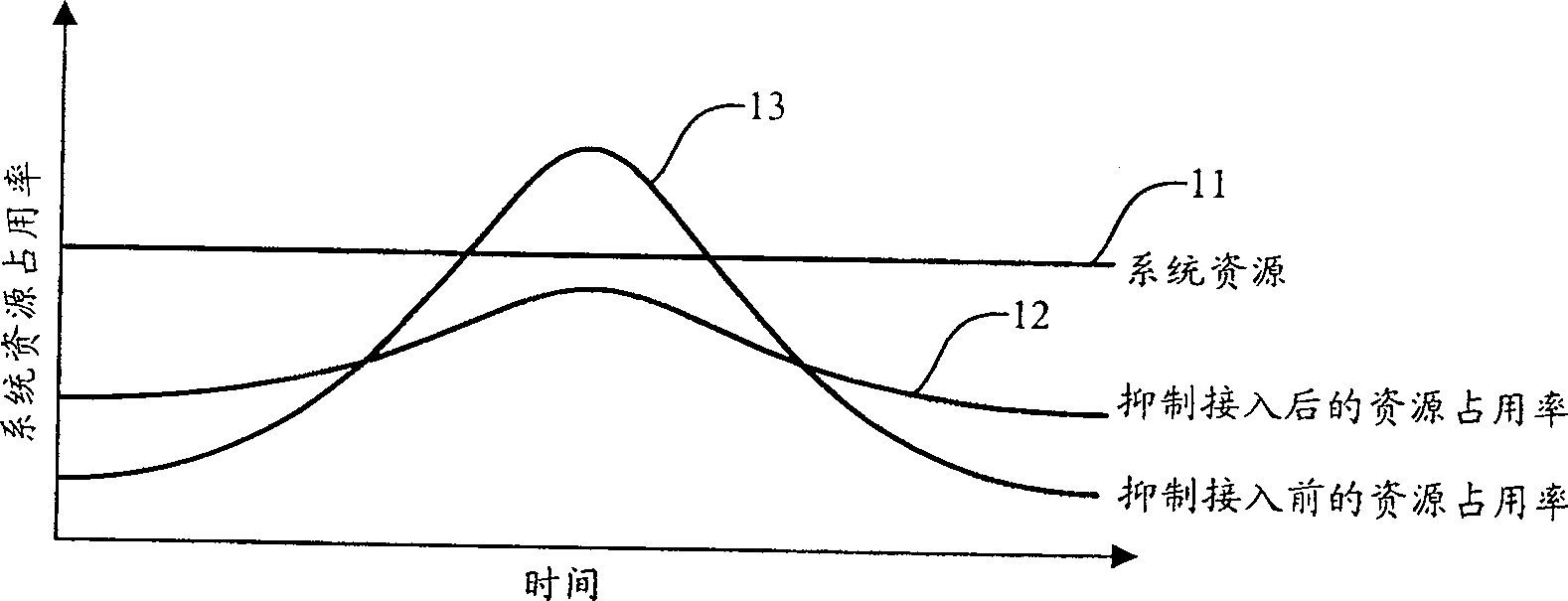
Image
Examples
Embodiment 1
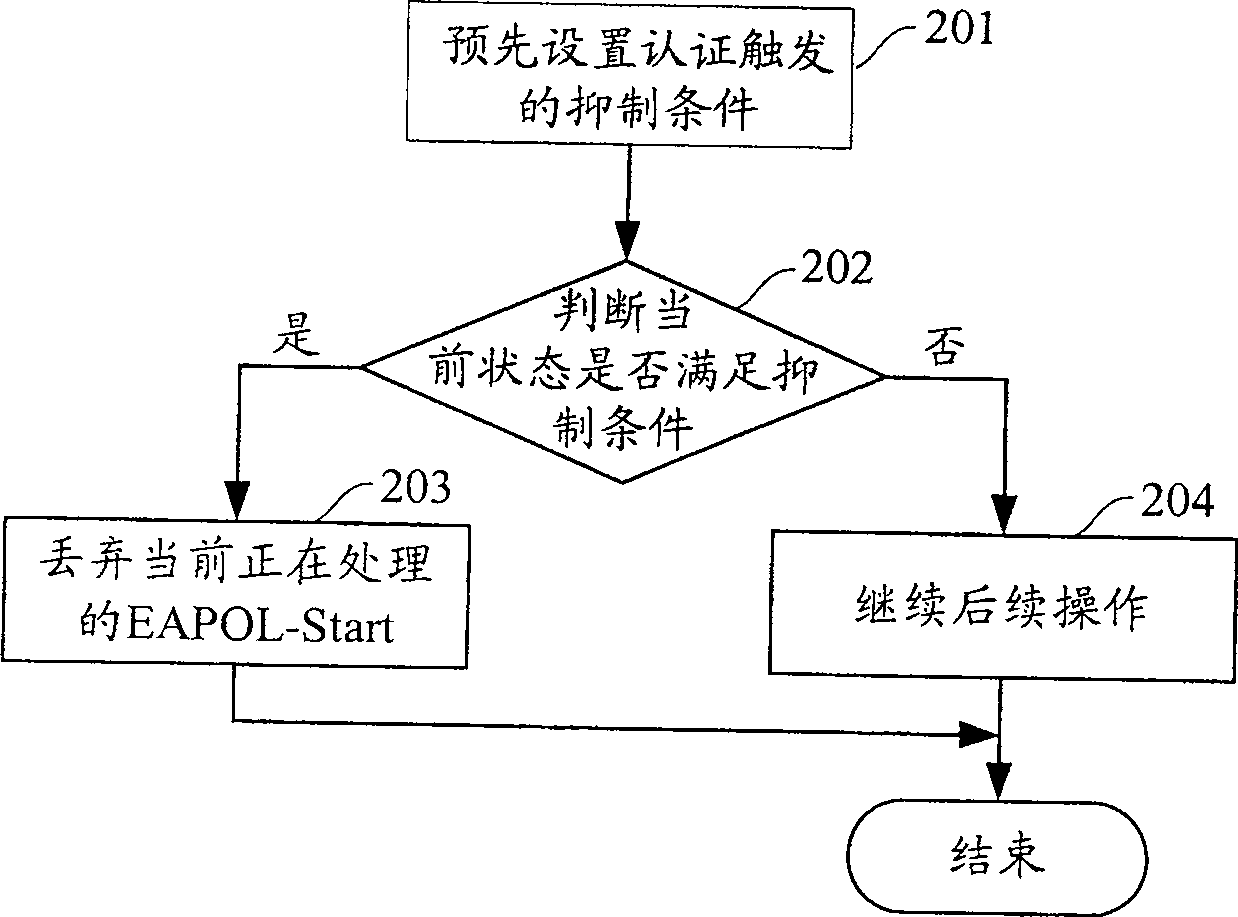
[0029] When the Authenticator takes out a protocol message to be processed from the protocol message receiving queue, it first judges its type as an authentication information frame (EAP-Packet), EAPOL-Start, an exit request frame (EAPOL-Logoff), and a key information frame (EAPOL-Key), select which one of the message frame (EAPOL-Encapsulated-ASF-Alert), if confirm that the type of protocol message to be processed is EAPOL-Start, then check whether the current protocol message receiving queue occupancy If the preset threshold is reached, the EAPOL-Start is discarded, and the packet processing process ends.
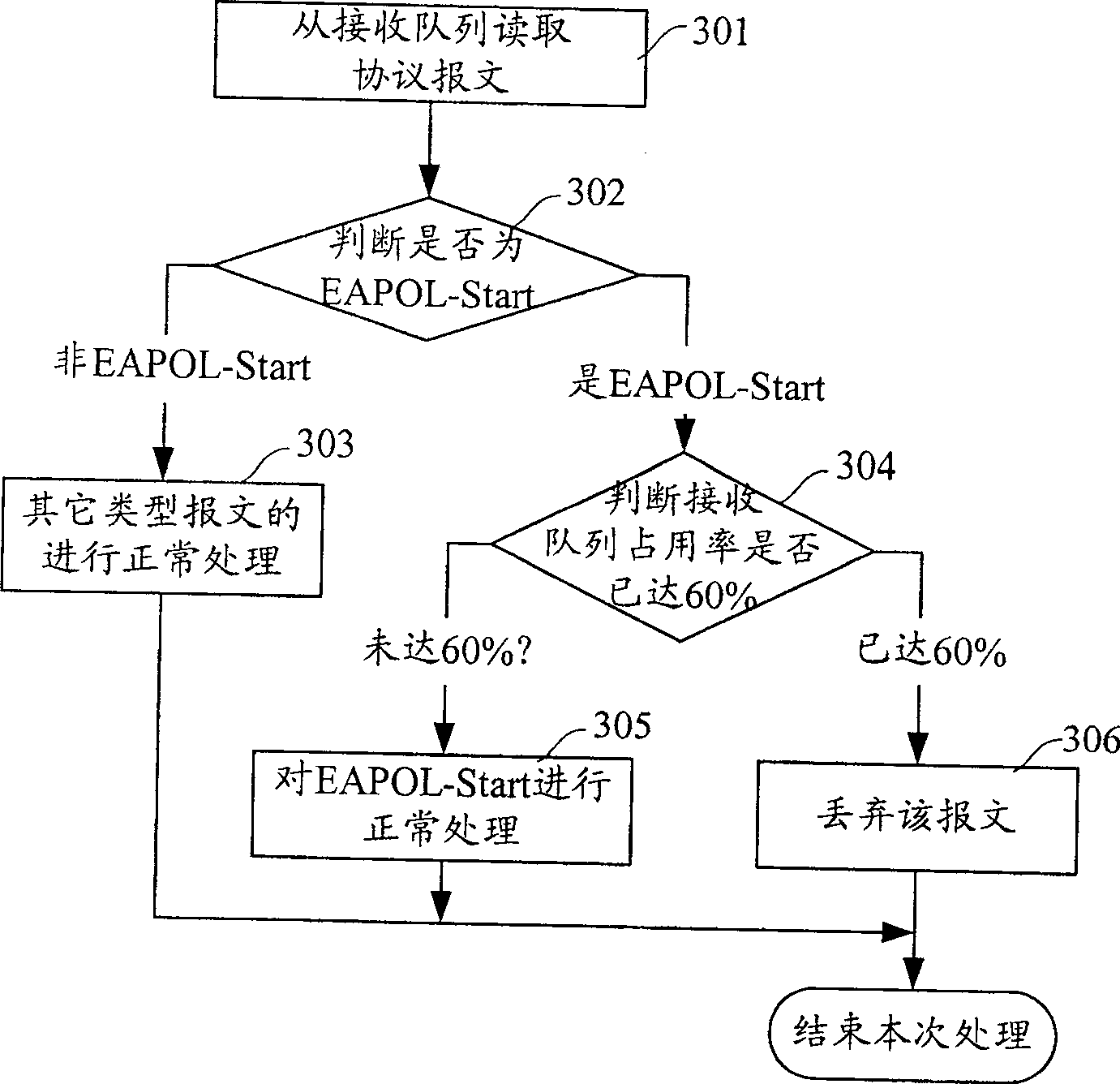
[0030] image 3 Shown is a flowchart of Embodiment 1 of applying the present invention to perform access suppression processing.
[0031] Step 301, the Authenticator takes out a protocol message to be processed from the protocol message receiving queue;
[0032] Step 302, judging whether the type of the protocol message taken is EAPOL-Start, if yes, then execute step 30...
Embodiment 2
[0039] In practical applications, since the underlying driver forwards the received protocol packets to the protocol packet receiving queue of the Authenticator, the type of EAPOL can be sent to the protocol packet receiving queue of the Authenticator by controlling the underlying driver program within a unit time -The number of protocol packets of Start, so as to achieve the purpose of the present invention. Its specific operation is as follows:
[0040] Preset the threshold of the number of protocol packets of the EAPOL-Start type that the system receives within a unit time in the underlying driver. If the number of protocol packets of the EAPOL-Start type received by the system within a unit time is within the threshold, it means that the system resource occupancy rate is within the control capability of the system, and it will be processed according to different types of protocol packets; if the underlying driver is in If the number of EAPOL-Start type protocol packets re...
Embodiment 3
[0042] The system judges the busyness of the system according to the number of times the process is called or the amount of data processed by the CPU per unit time through the underlying driver program or the logic circuit in the switching chip. When the busyness of the system reaches a certain value, the underlying driver is controlled. Program sends the number of the protocol message of EAPOL-Start of the protocol message receiving queue of upper layer Authenticator, and then reaches the purpose of the present invention.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com