Design method of asynchronous block cipher algorithm coprocessor
A block cipher algorithm and coprocessor technology, applied in the direction of electrical digital data processing, special data processing applications, encryption devices with shift registers/memory, etc., can solve the problem of high resistance to power consumption attack protection capabilities, difficulties in implementing asynchronous circuits, lack of Aided design tools and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
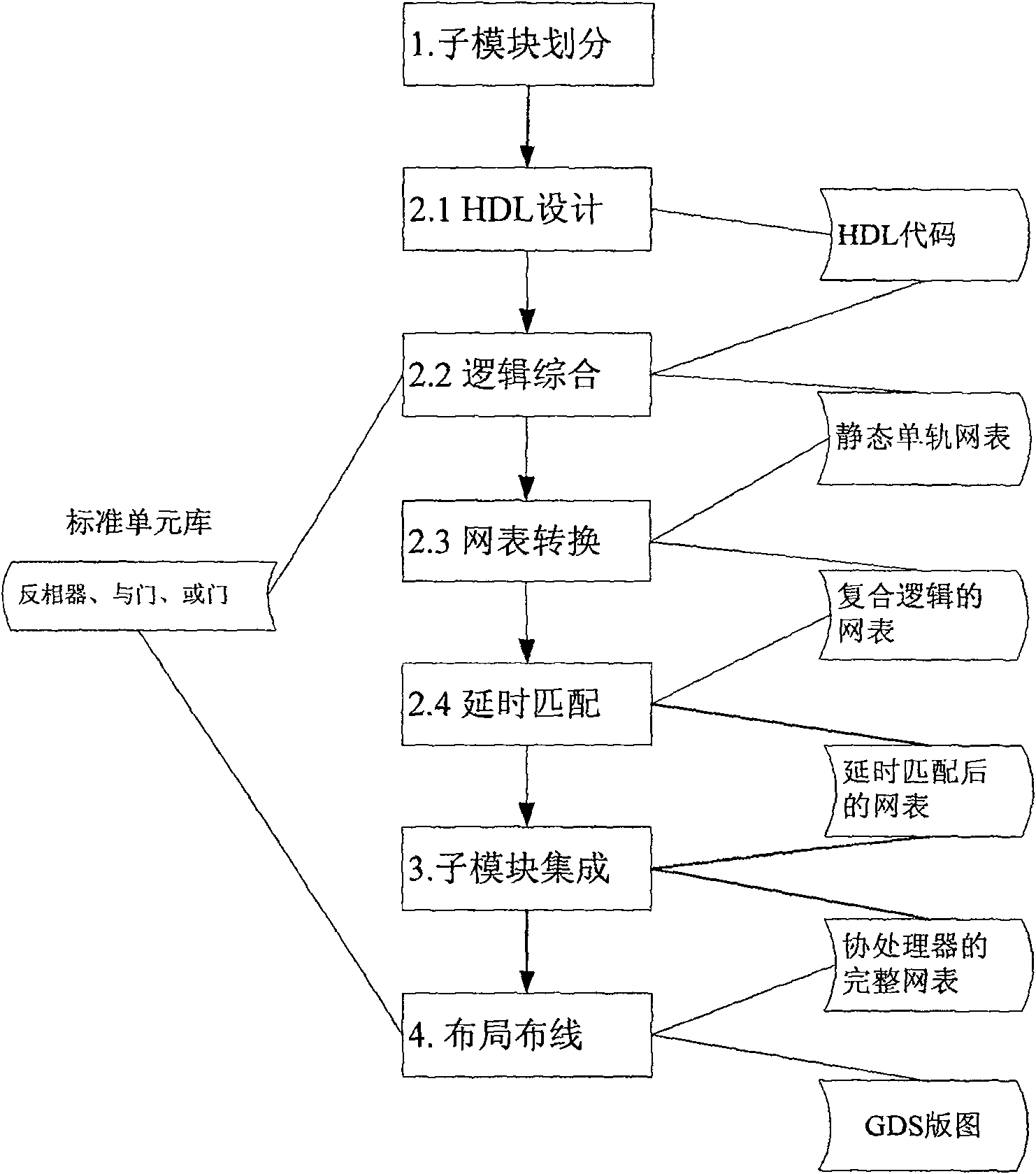
[0039] figure 1 For adopting the present invention to carry out the design flowchart of asynchronous block cipher algorithm coprocessor, mainly comprise the following steps:
[0040] 1. Divide the block cipher algorithm into sub-modules to obtain sub-modules;
[0041] 2. Sub-module design, including the following steps:
[0042] 2.1 HDL design, get the HDL code of the sub-module.
[0043] 2.2 Logically synthesize the HDL code of the sub-module to obtain the static monorail netlist of the sub-module.
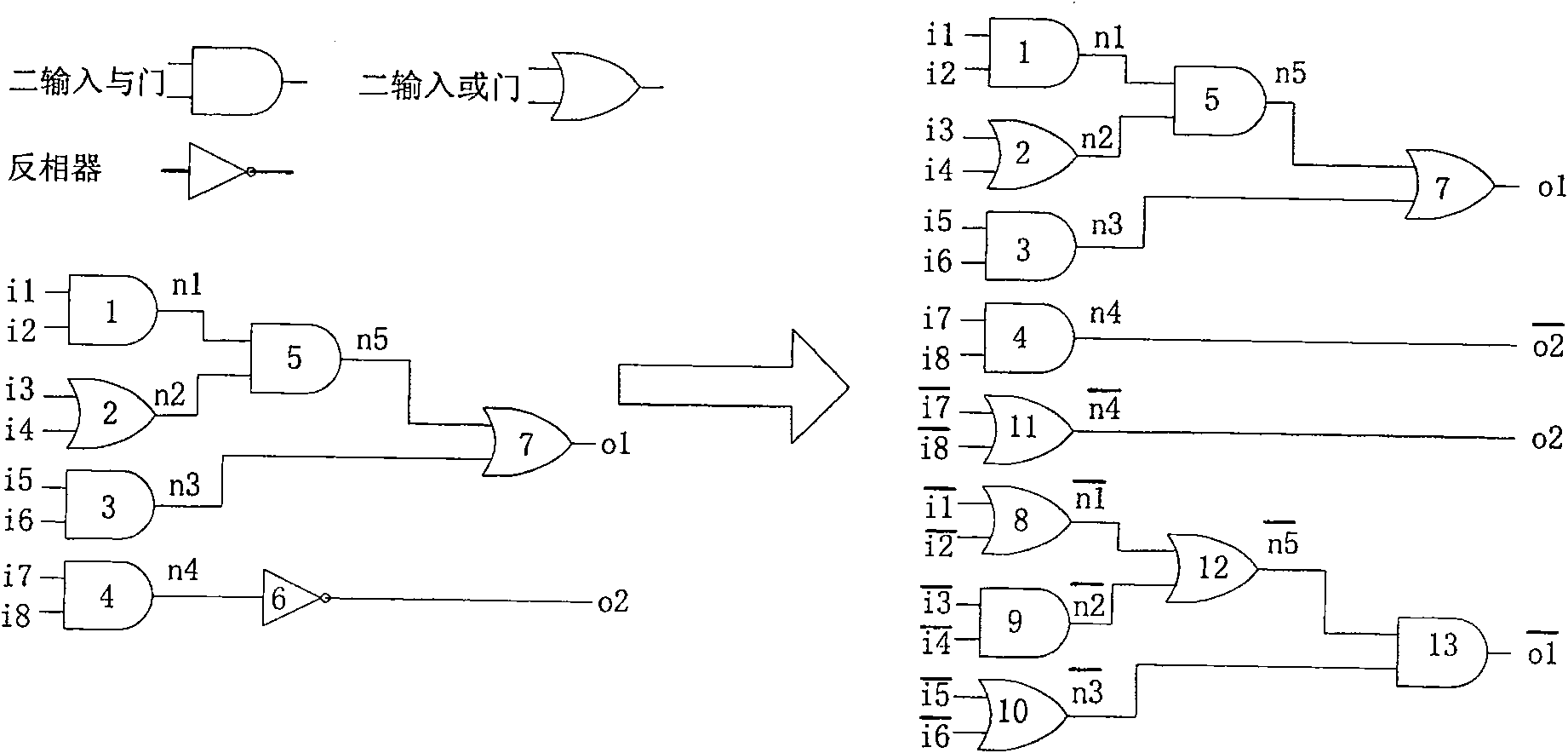
[0044] 2.3 Convert the static single-rail netlist into a netlist composed only of complementary two-input AND gates and OR gates to obtain a composite logic netlist.
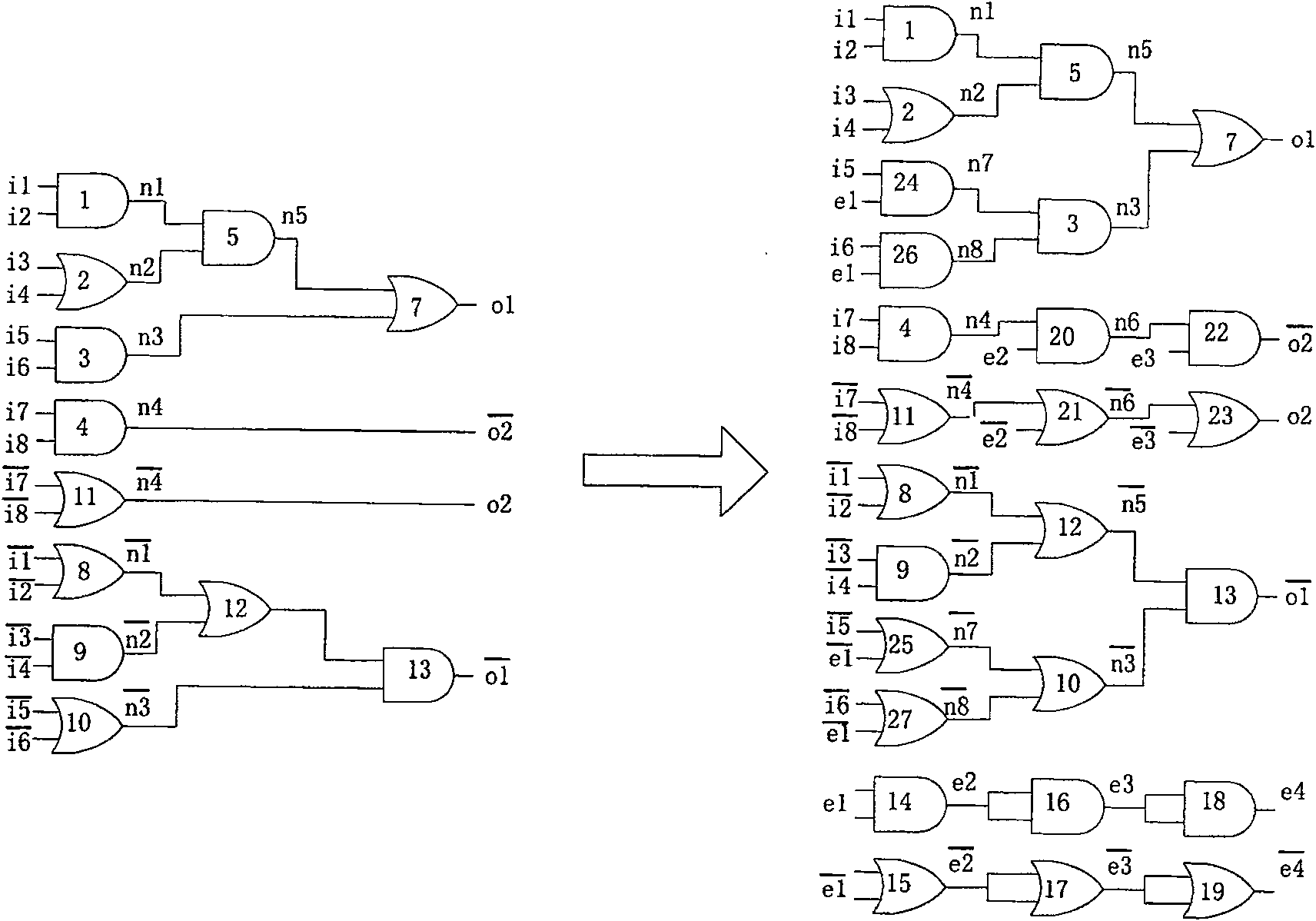
[0045] 2.4 Add a delay matching module with the same delay as the sub-module to ensure that the delay from any input signal to the output signal of each sub-module is the same, and the arrival time of any two inputs in the circuit is the same as the two inputs of the gate and the OR gate .
[0046] 3. Integrat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com