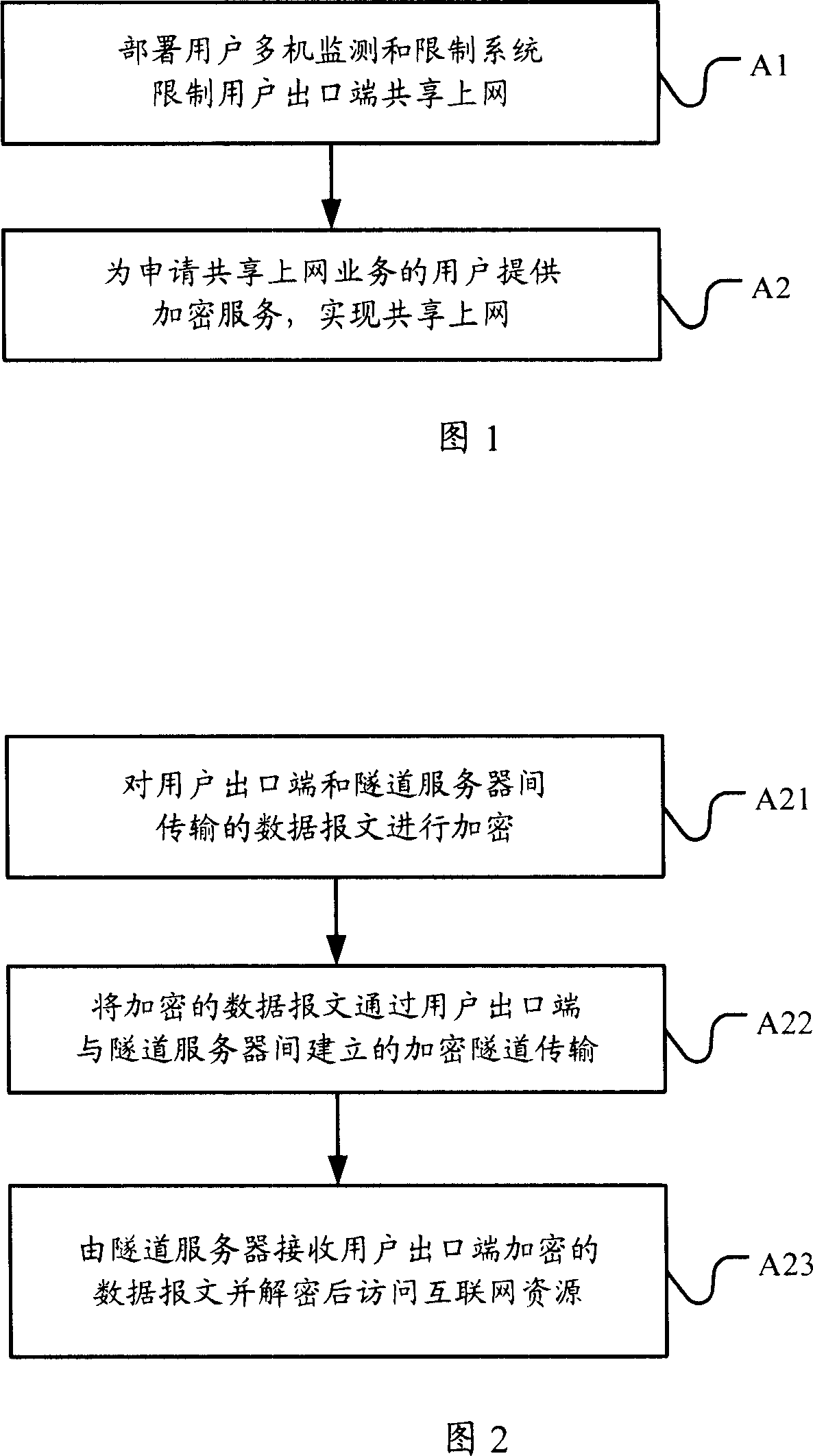
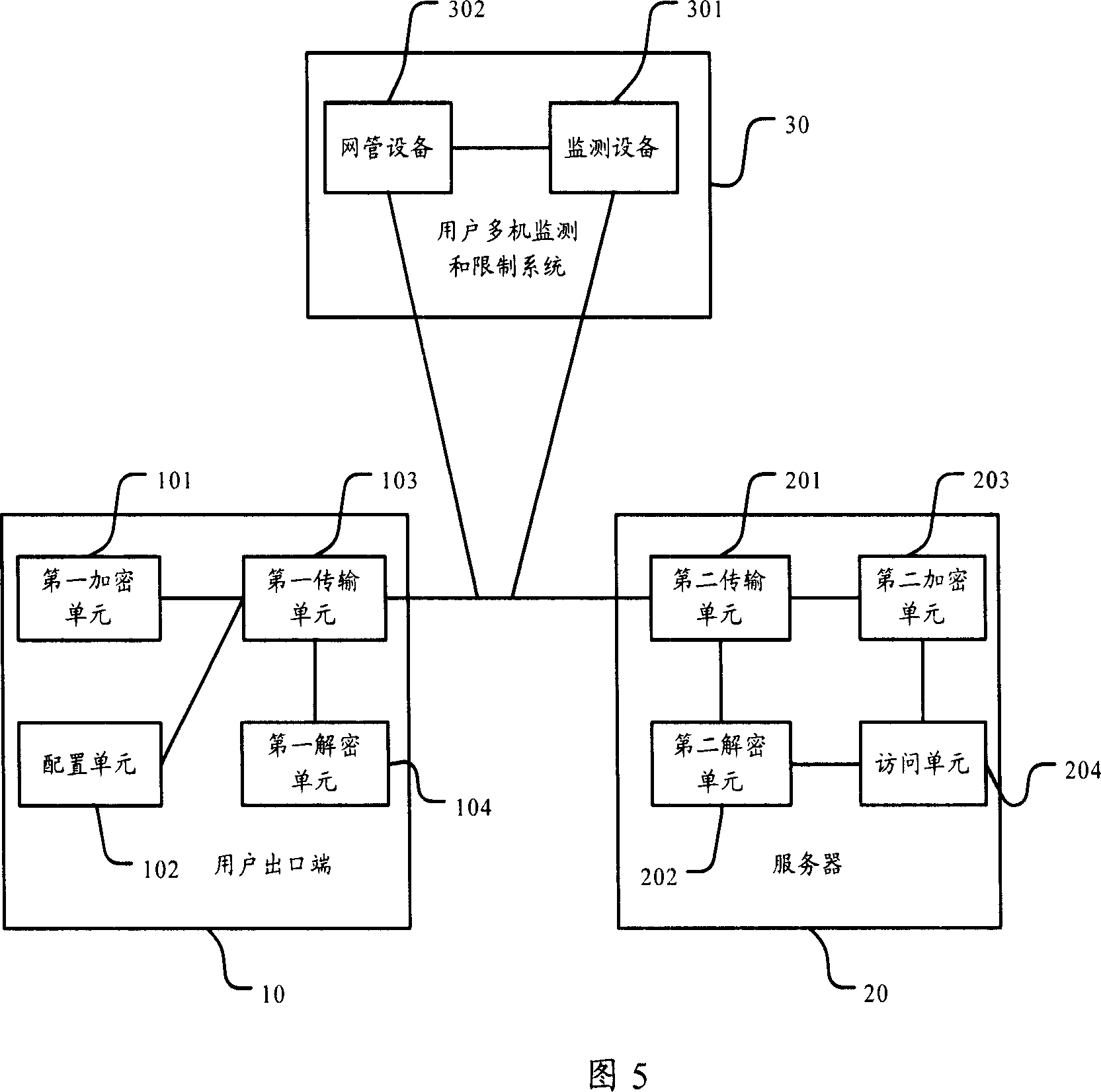
Subdivision method of the user network access style and network system
A network system and user technology, applied in the Internet field, can solve problems such as ignoring users, and achieve the effect of adding business value
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
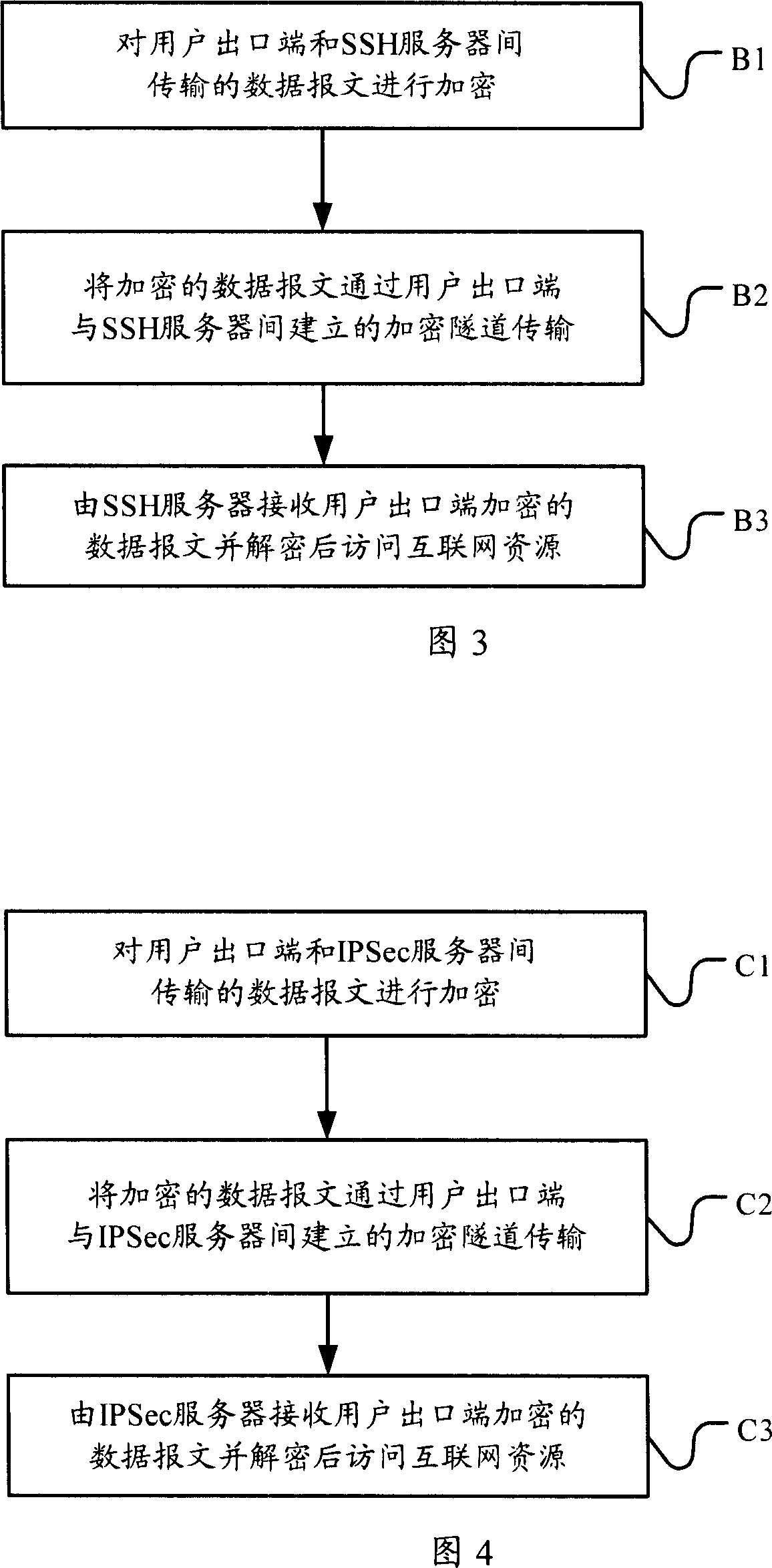
[0043] Firstly, the first embodiment is introduced, using the secure shell SSH (Secure Shell) protocol to establish an encrypted tunnel to realize shared Internet access. The Secure Shell SSH protocol is a family of protocols formulated by the Network Working Group of the Internet Engineering Task Force IETF (Internet Engineering Task Force), whose purpose is to provide secure remote login and other secure network services on non-secure networks . The SSH protocol supports identity authentication and data encryption, and encrypts all transmitted data. There are many ways to implement the SSH protocol, such as open source OpenSSH software, commercial Tectia, SecureCRT and other software. They are relatively simple to configure and use, and they support the compression function, so that the actual transmission efficiency will not be reduced due to the overhead of the SSH protocol.
[0044] Please refer to Figure 3, which is a flow chart of Embodiment 1 of providing encryption ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com