Message processing method, system and equipment
A message processing and message technology, which is applied in the field of network communication, can solve the problems of message attack security, fault location and troubleshooting, and behavior without tracking records, etc., to achieve the effect of convenient location and troubleshooting
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below with specific embodiments in conjunction with the accompanying drawings.
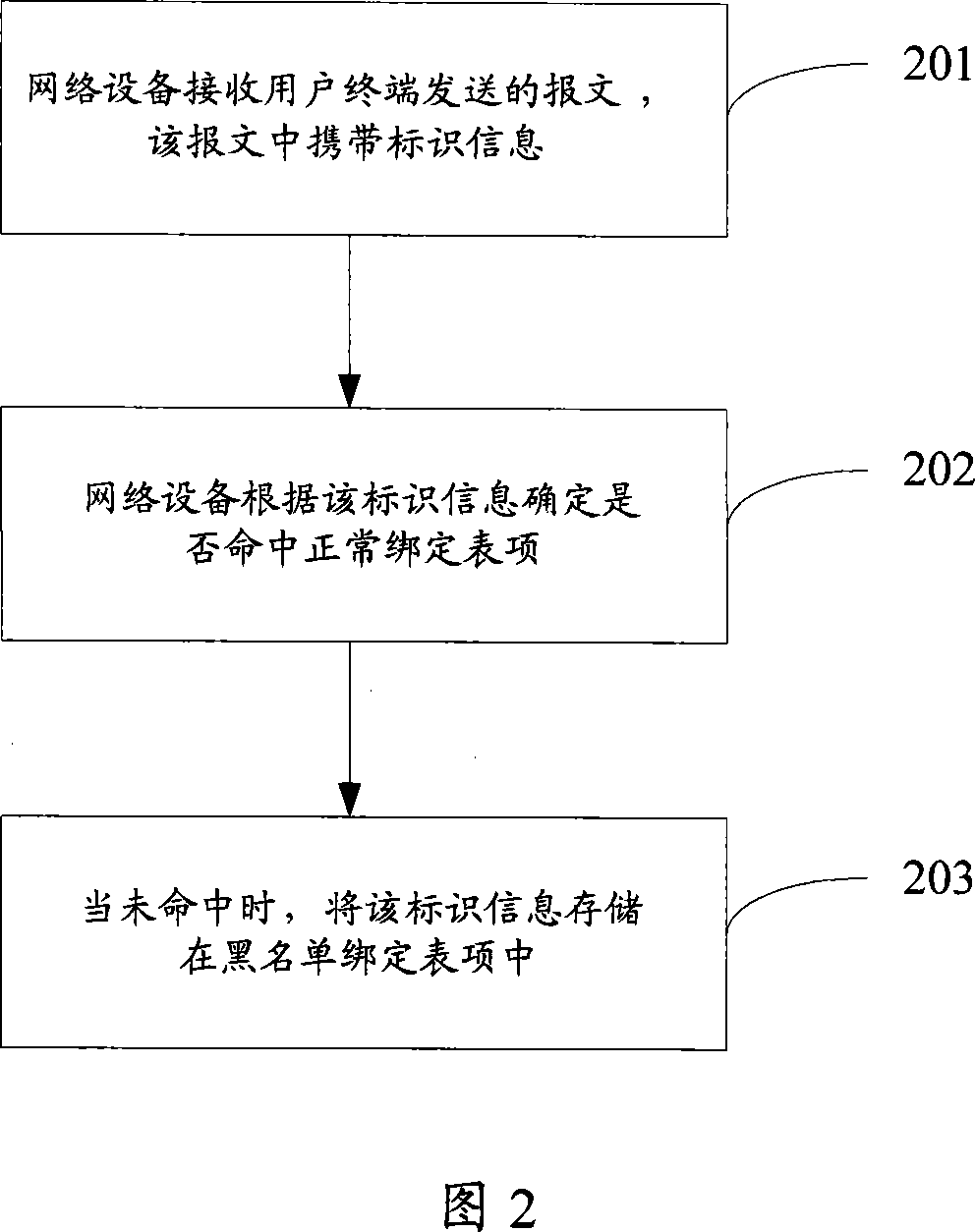
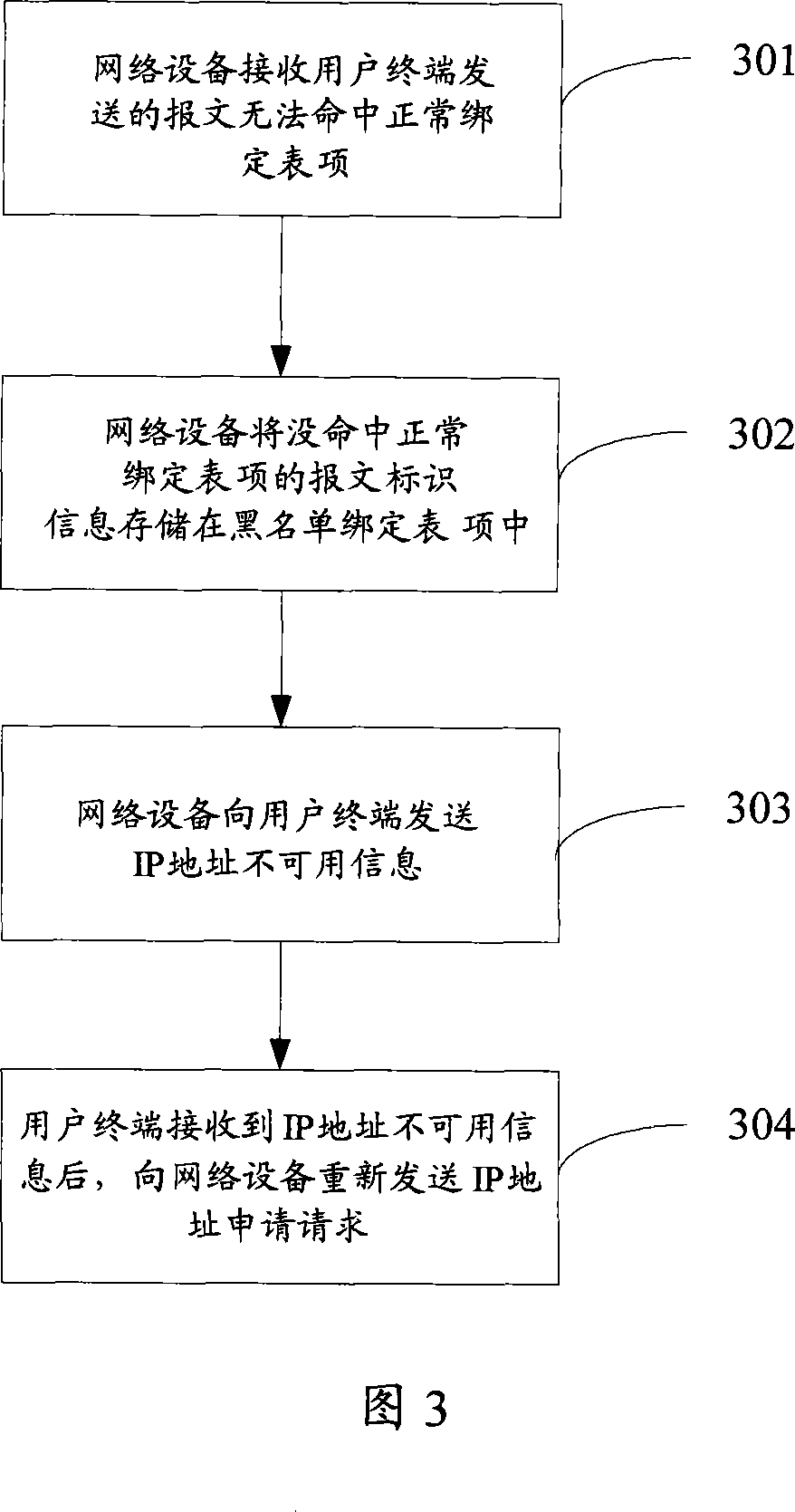
[0028] The embodiment of the present invention provides a message processing method. The binding table in the prior art only includes KEY, such as source MAC, source IP, PORT and VLAN as shown in Figure 1, the embodiment of the present invention adds two One field is used to indicate the type of the binding table, one is the normal DHCP Snooping binding entry, the other is the abnormal DHCP Snooping binding entry, because a message does not hit the normal binding entry The binding entry created by extracting relevant information from the message is also called a blacklist binding entry; another field is used to indicate the frequency of the blacklist binding entry being hit. Through the statistics of the hit frequency of the user terminal information in the blacklist binding table entry, the attacker's behavior and information can be effectiv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com