A JPEG lossless compression image hide writing method based on predictive coding
A lossless compression and predictive coding technology, which is applied in image communication, television, electrical components, etc., can solve the problems of large embedded data, image statistical characteristics, poor ciphertext image quality, weak anti-attack ability, etc., and achieve high algorithm security , strong practicability, and less damage to image statistics
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
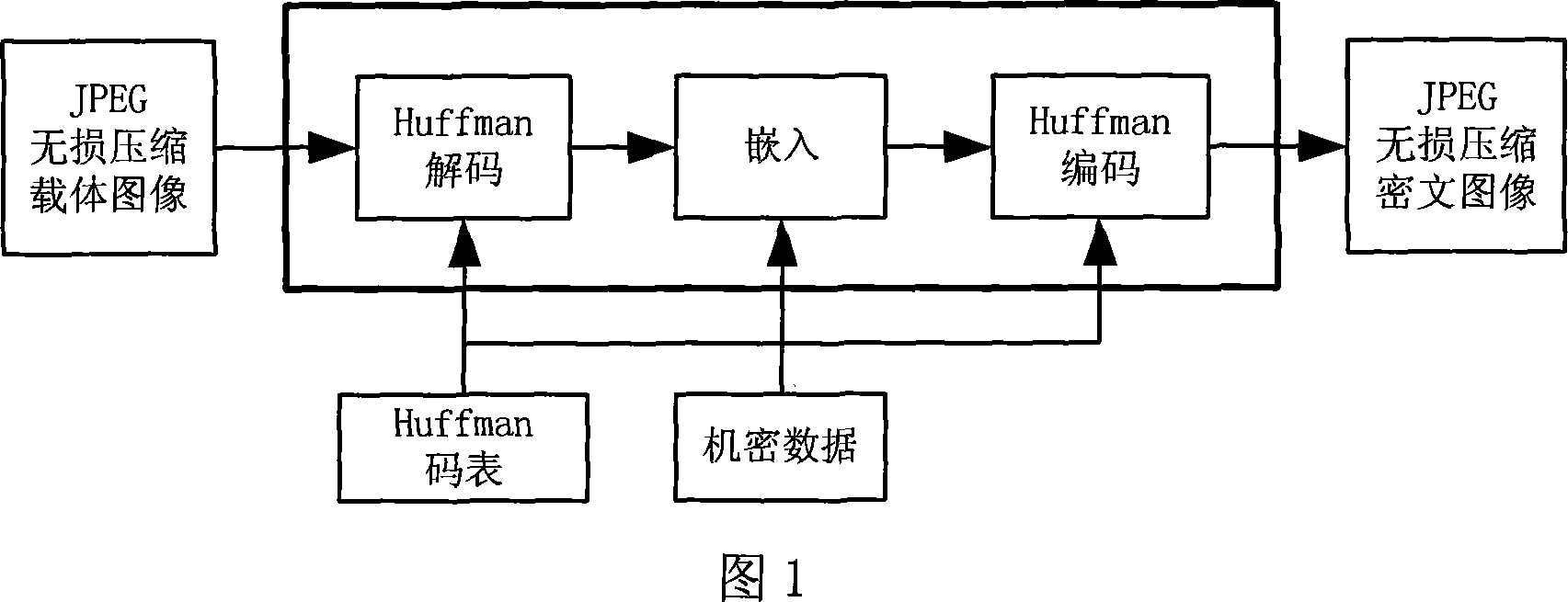
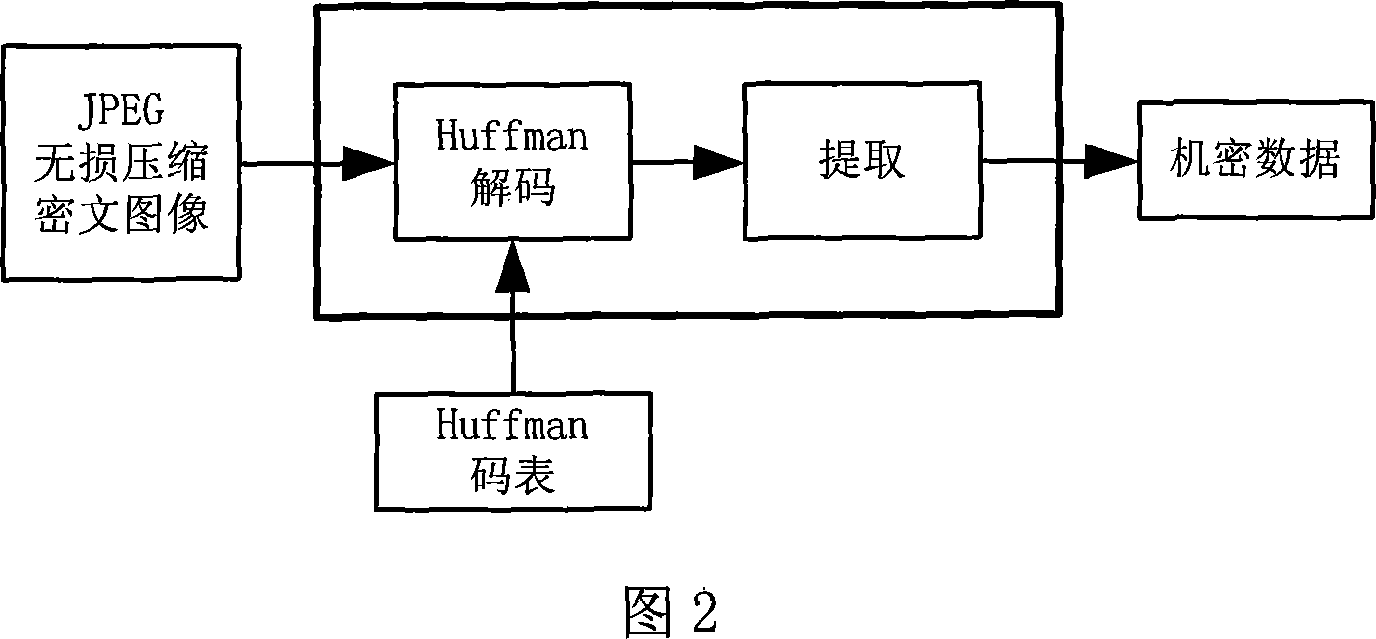
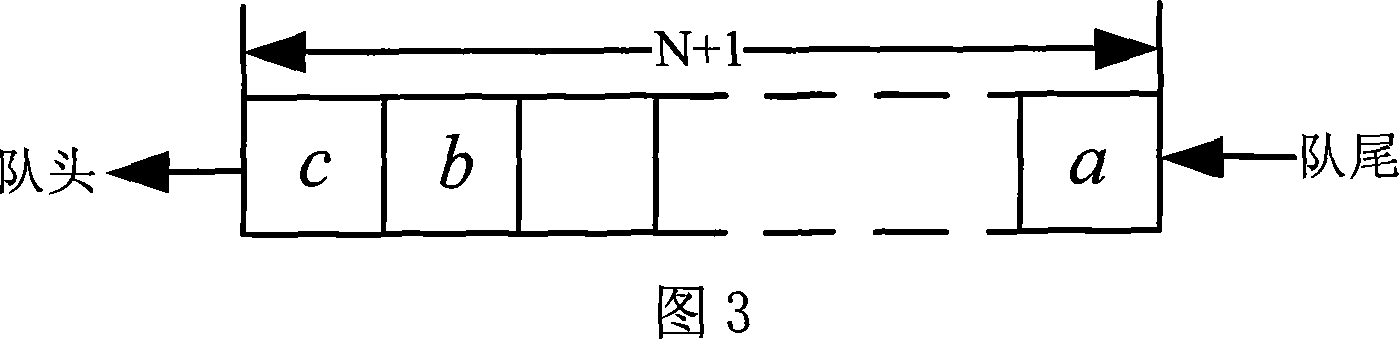
[0038] The present invention will be further described below in conjunction with the embodiments and accompanying drawings.
[0039] As shown in Figures 1 to 6, the embedding process of the inventive method is as follows:
[0040] First, select the secret message to be delivered, which can be any file such as text, image, audio, etc., and convert it into a binary sequence. In this example, the 95×90 grayscale image shown in Figure 6(b) is used as the secret information, and the file size is 1142 bytes. It is encrypted and converted into a binary sequence of 01000010...0, a total of 9136 bits.
[0041] Secondly, choose a carrier image with JPEG lossless compression. The size of the image can be used as a reference for the length of the secret information, that is, an appropriate embedding rate h should be selected. In this example, the 512×512×8bits Lena image as shown in Figure 7(a) is used as the carrier image, the total file size is 169140 bytes, and the gray value is shown...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com