Method and device for managing WPI cipher key in 802.11 chips
A key and chip technology, applied in the field of managing WPI keys in 802.11 chips, can solve problems such as occupying a large storage space, achieve efficient acquisition, realize pipeline processing, and reduce the effect of on-chip cache
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] specific implementation plan
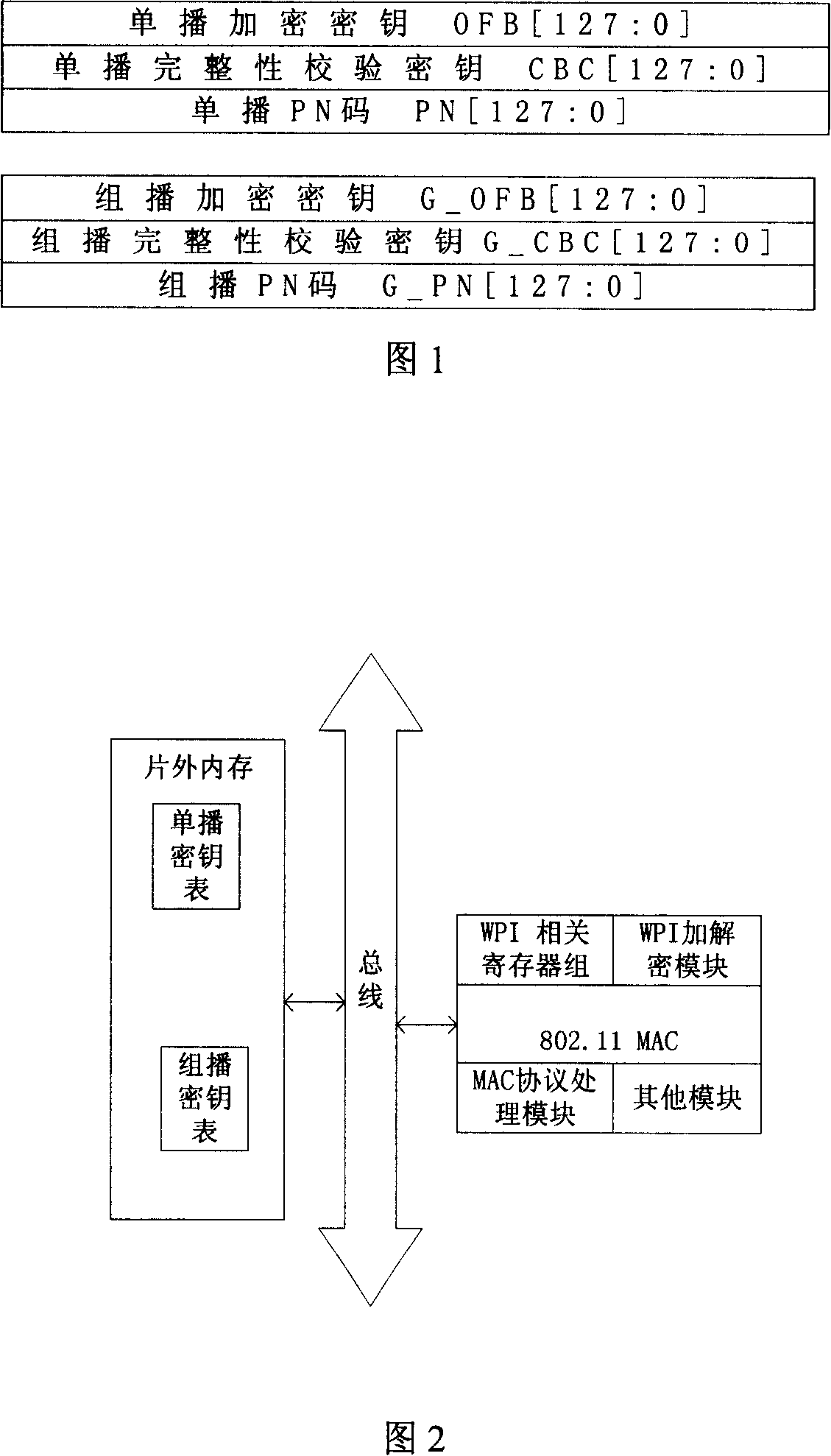
[0065] Please refer to Figure 2, which depicts the structure of an 802.11 MAC system that implements the WPI function.
[0066] Realize that the parts of the 802.11 MAC system with WPI function include: an 802.11 MAC hardware, responsible for realizing the 802.11MAC protocol; an off-chip memory, used to store data, in the present invention, the unicast key table and the multicast key table stored here. In the 802.11 MAC device, a WPI-related register group is included to realize the storage and state storage of the WPI key; a WPI encryption and decryption module is included for WPI encryption and decryption; an 802.11 protocol module is included for processing the protocol; Also contains some other modules.
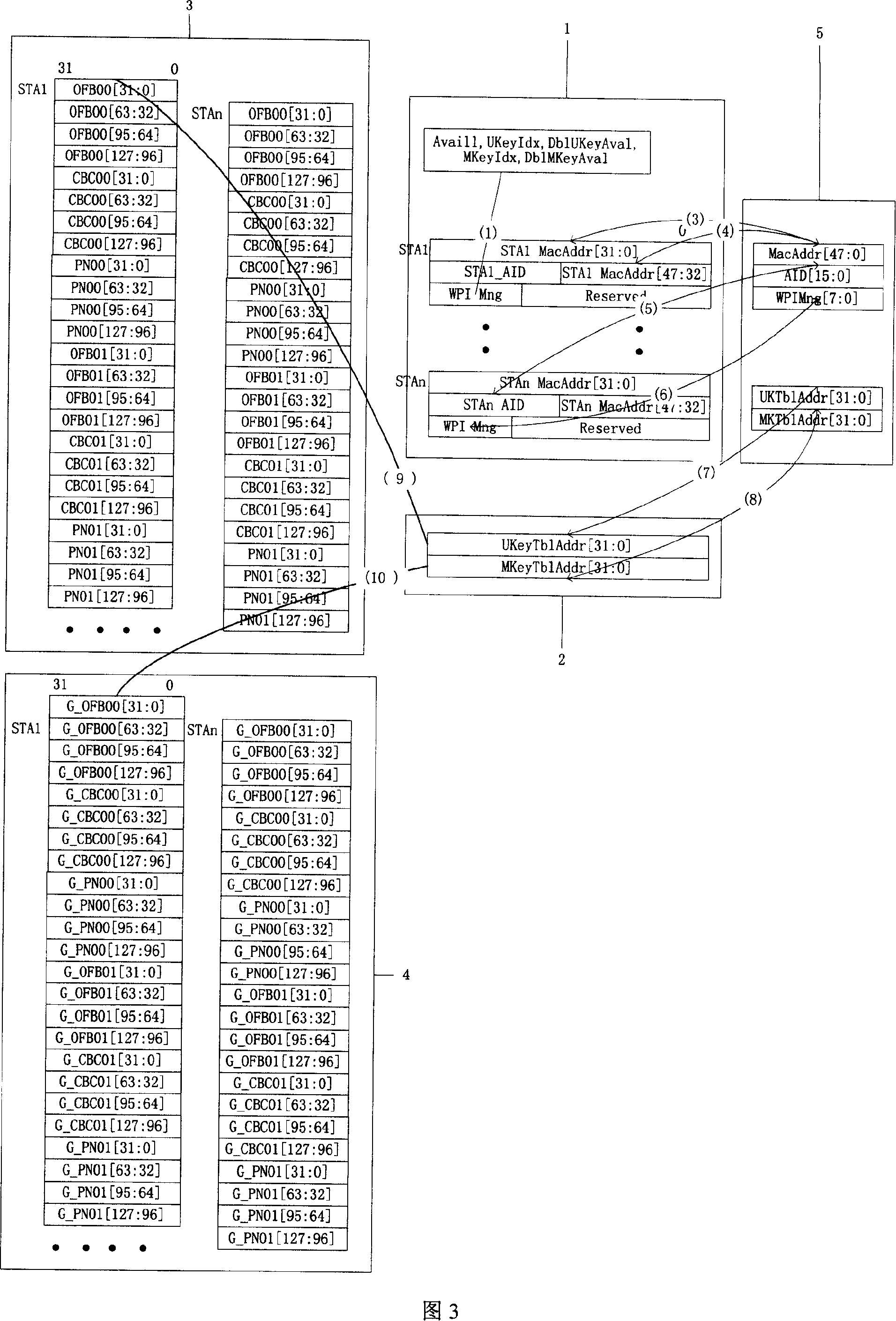
[0067] The unicast key table, multicast key table, WPI related register group, member index table and key table base address on the IO interface together constitute the WPI key management module.
[0068] Please refer to FIG. 3 , w...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com