Network boundary treatment method
A processing method and network boundary technology, applied in the field of communication, can solve the problems of too many peripheral interfaces, inability to transmit, and the calling party cannot predict the network situation of the called party.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
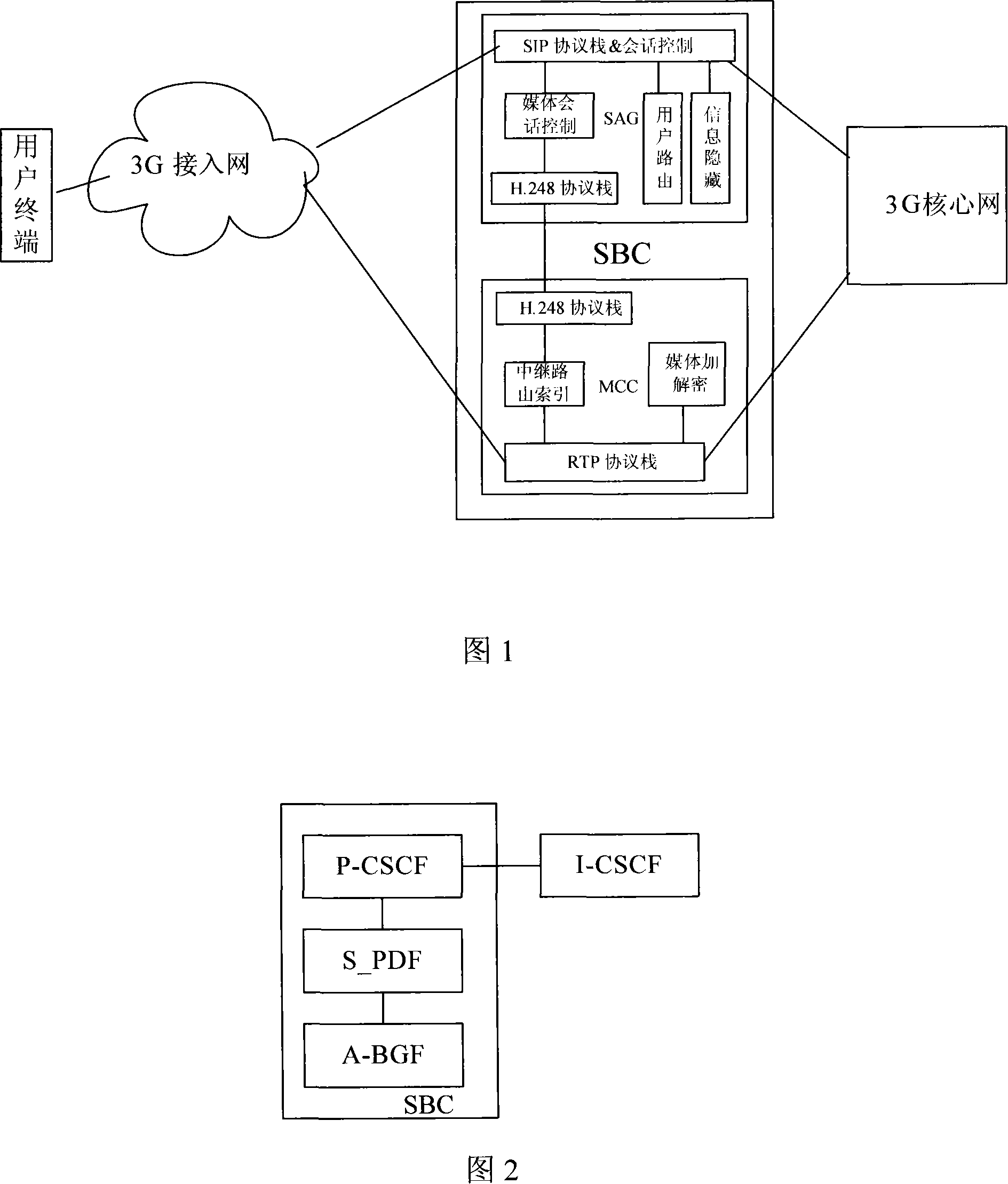
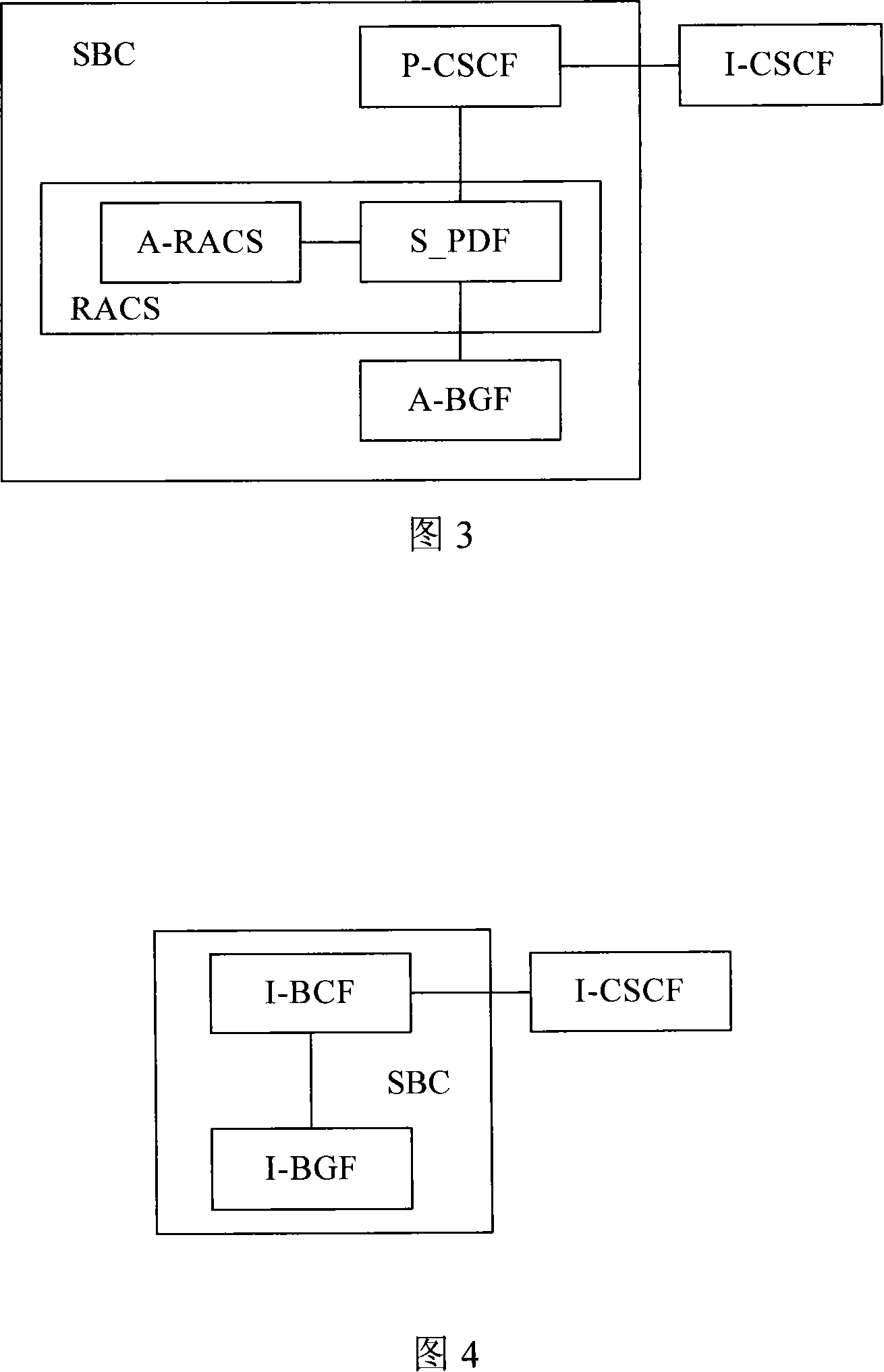
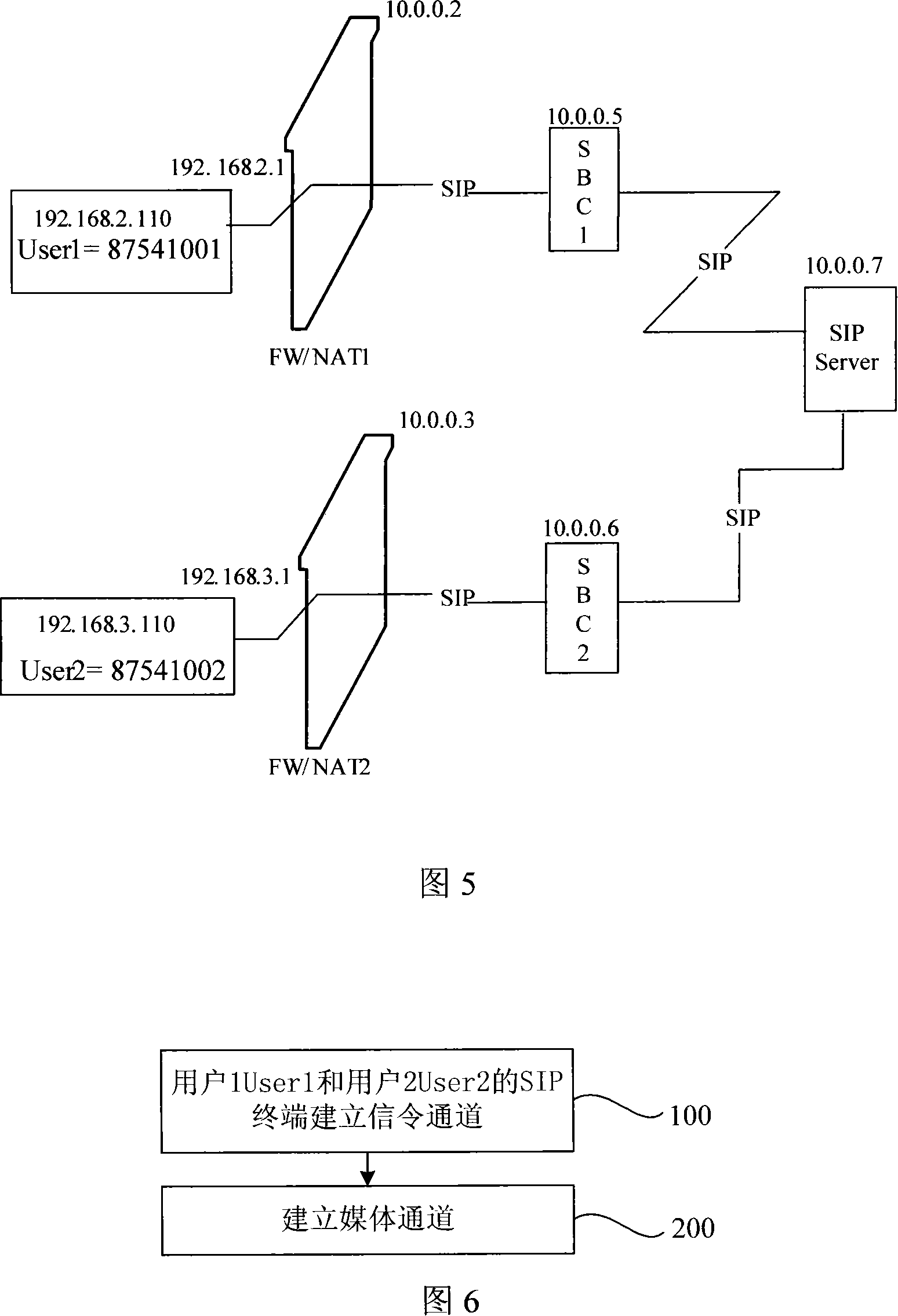
[0070] The present invention provides a network boundary processing method. When firewall / NAT traversal is required, an SBC server is set up between the user's intranet and a VoIP (Voice over Internet Protocol, VoIP) server. The implementation of the present invention as shown in FIG. 1 For example, an SBC server is set up between the 3G access network and the core network. The SBC server includes a SAG module and an MCC module. The SAG module includes the SIP protocol stack and session control functions, media session control functions, user routing and information hiding functions, and has H .428 protocol stack; communicate with the MCC module through the H.428 protocol SAG module, the MCC module has the functions of trunk index, media encryption and decryption, and RTP protocol stack. By modifying the entry corresponding to the call server (Call Server) in the domain name server, the IP address of the SBC is used as the IP address of the call server to respond to the user te...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com