Binary mode collision-proof method with safe mechanism in RFID
A security mechanism, binary technology, applied in the field of RFID, can solve the problem of small storage capacity, achieve the effect of privacy and security, prevent eavesdropping and tracking, and strong flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
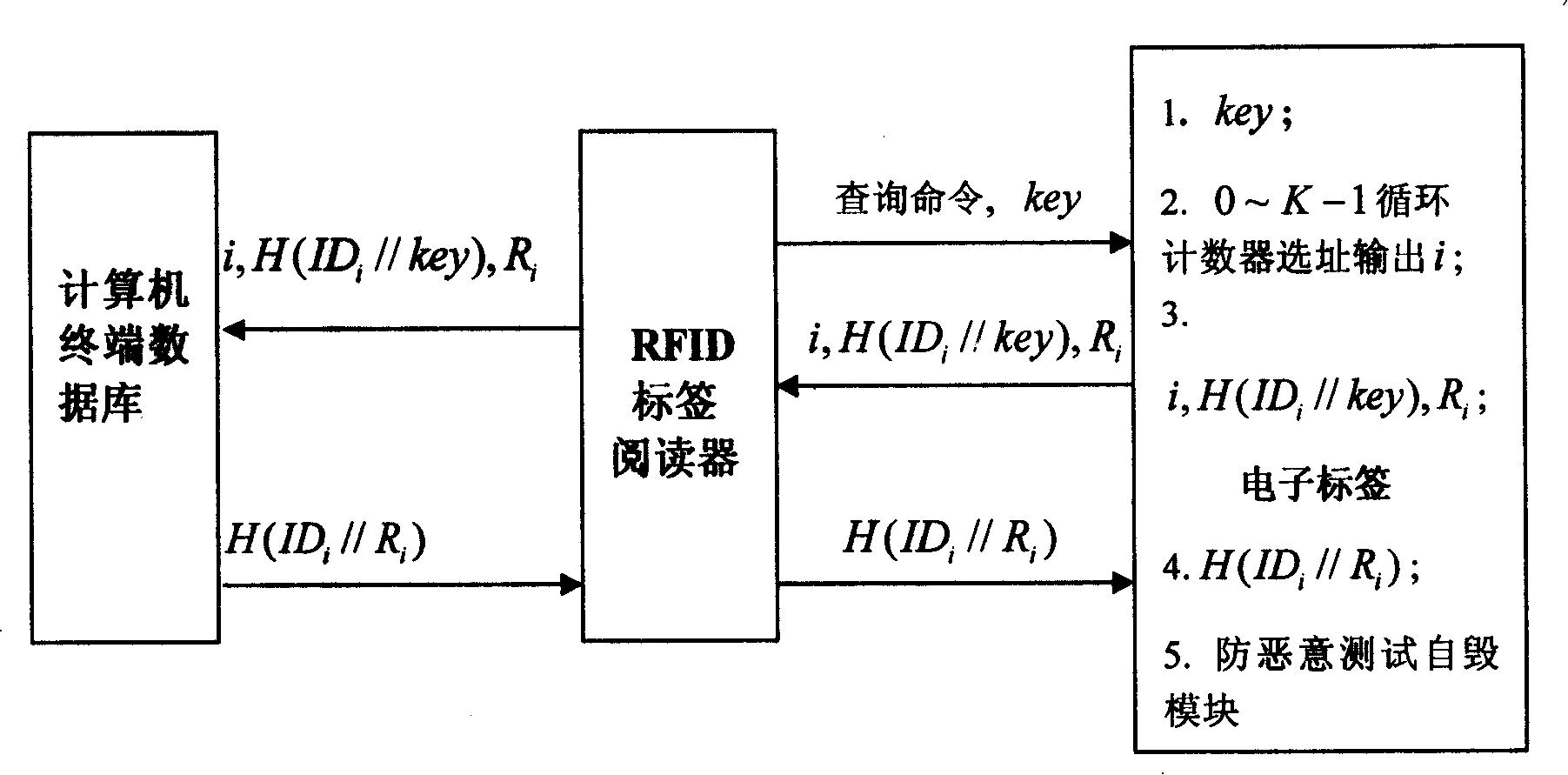
[0046] RFID systems usually consist of tags, readers and data management systems. Before explaining the anti-collision method of the present invention, the tags and tag readers used are firstly described.
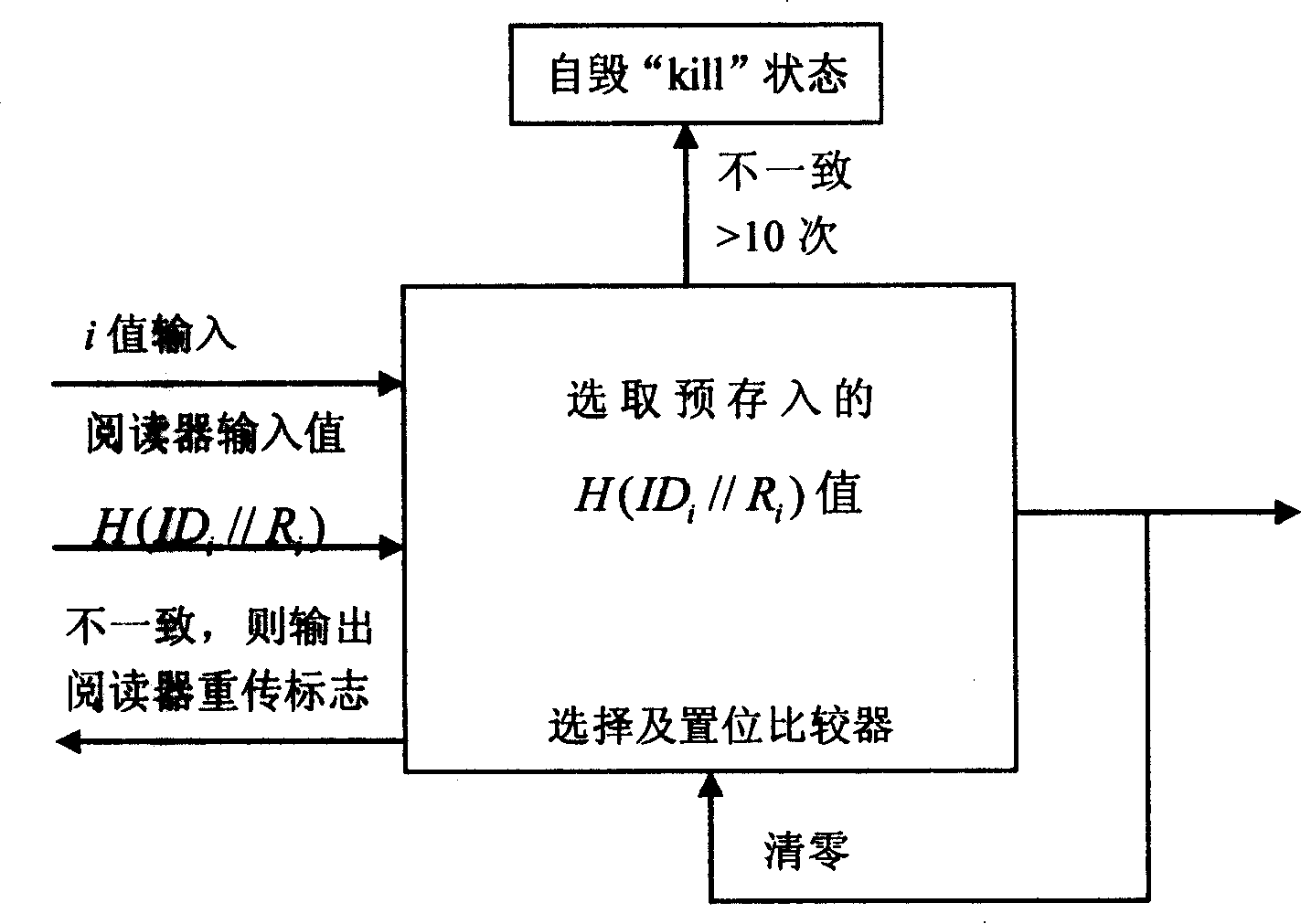
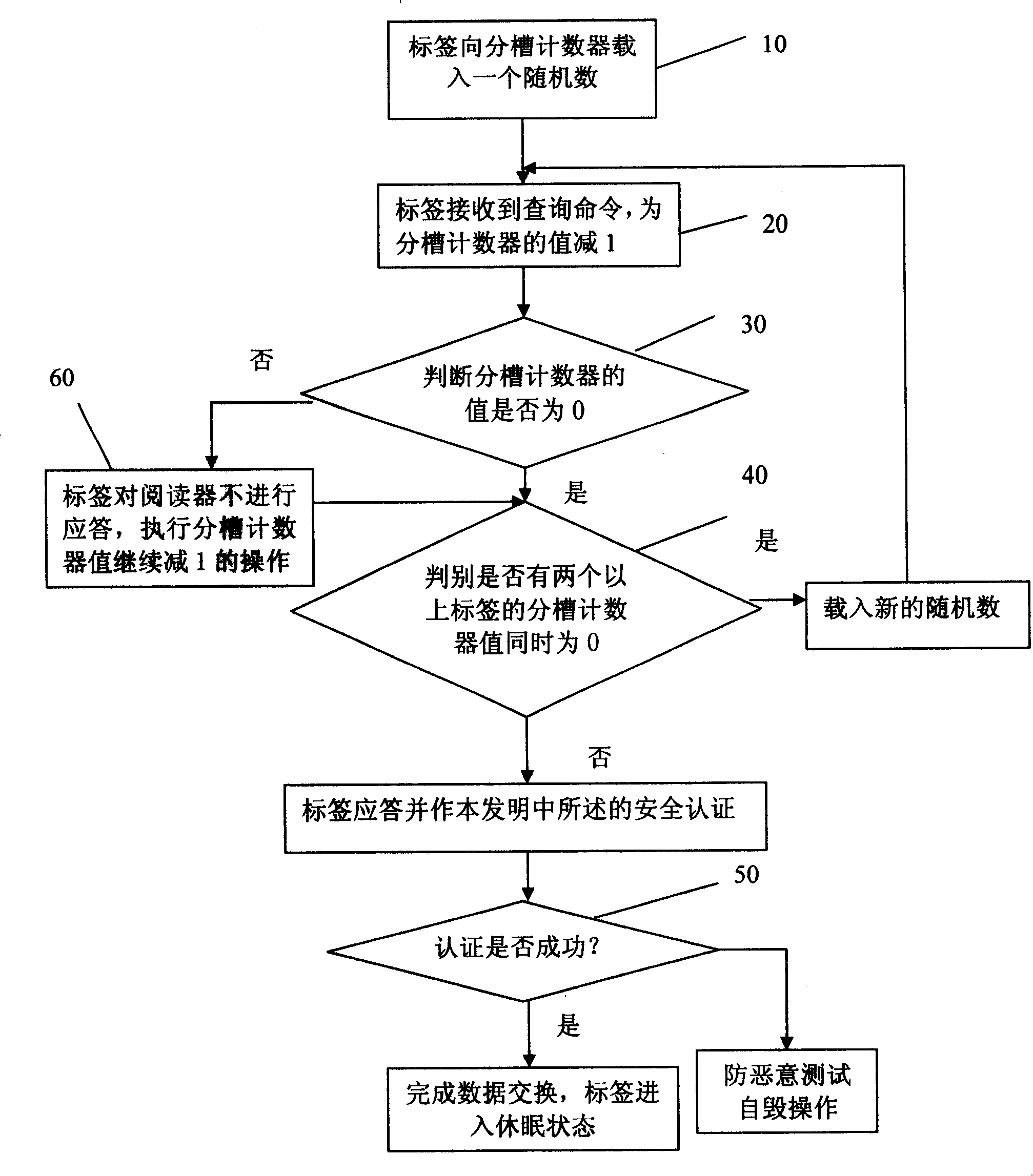
[0047] The tag includes: antenna, modulator, encoder, controller, and memory. The controller includes a slot counter, a loop address counter, and an anti-malicious test self-destruction module. The sub-slot counter is a decremental counter, which is used to complete the binary tree search process; the circular address selection counter is used to circularly select the position number of the ID pseudonym; the anti-malicious test self-destruction module is used when the illegal reader repeatedly tests the label content Automatically destroy the label, so as to achieve the purpose of protecting the label secret.
[0048] The tag reader includ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com