Method for cryptographic key exchange of passive optical network system
A passive optical network and system key technology, which is applied in the field of PON system key exchange, can solve problems such as high risk of failure and key exchange failure, and achieve the effects of improving efficiency, reducing time, and saving resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
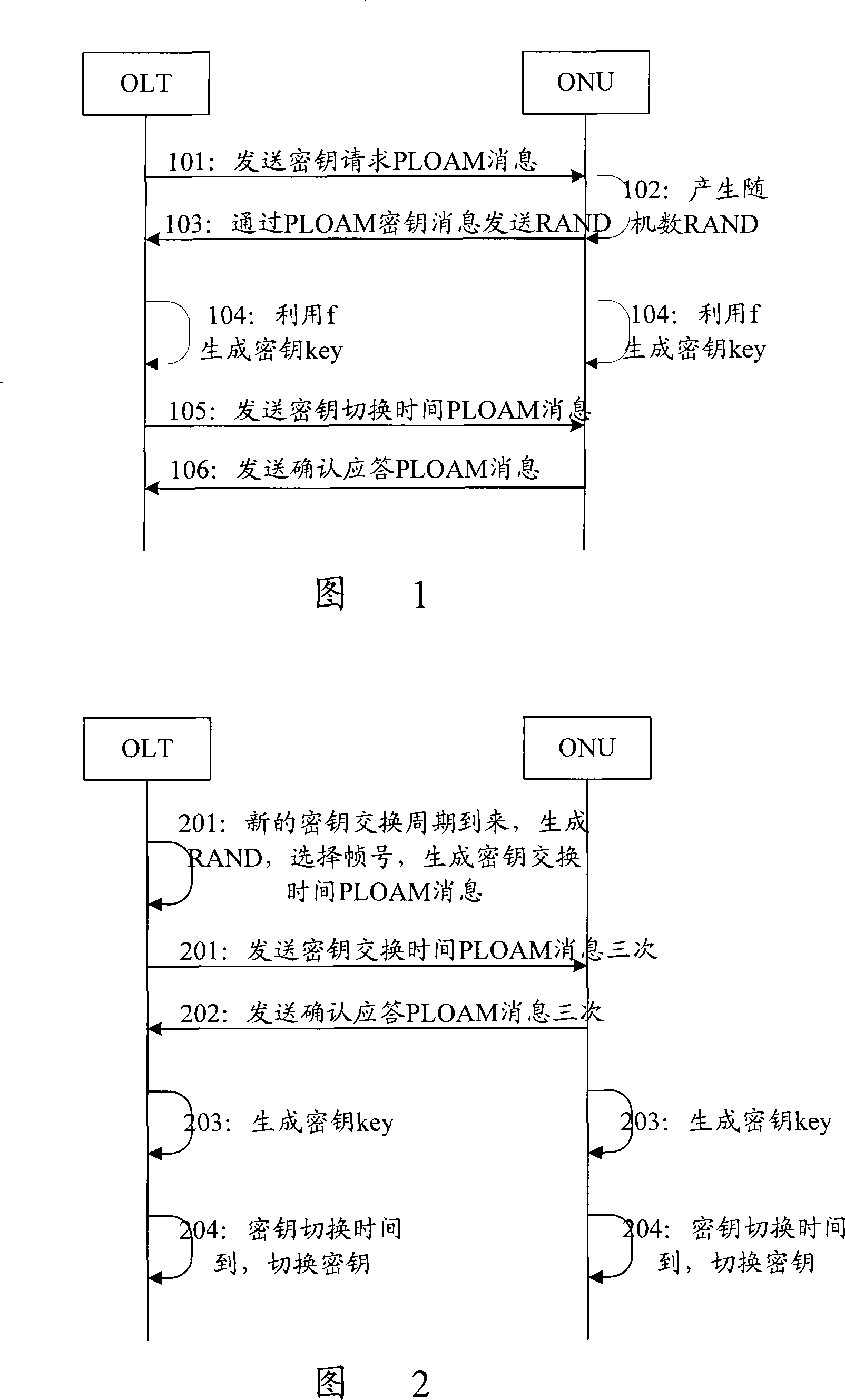
[0037] The basic idea of the present invention is: after the first key exchange of the PON system is successful, the random number generated by the OLT and the key switching time are encrypted using the key (current key) generated by the last key exchange, and at the same time Send it to the ONU, and then the OLT and the ONU simultaneously generate a new round of encrypted keys based on the random number and the current key, and switch the key at the specified time at the same time.
[0038] The specific implementation of the present invention will be described in further detail below in conjunction with the accompanying drawings.
[0039] When the first key update period arrives, the PON system first performs the first key exchange according to the ITU-T G.984.3 key exchange method in the prior art;
[0040]Here, the PON system generally performs the first key exchange according to the ITU-T G.984.3 key exchange method in the prior art. The reason why the first key exchange...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com