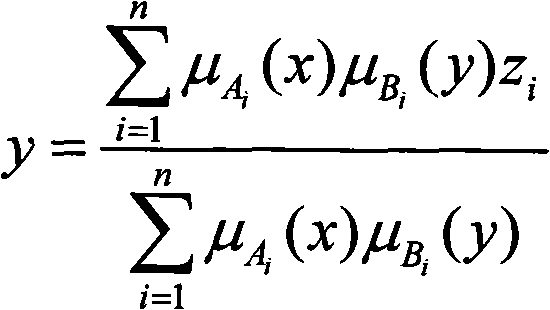Method for detecting TCP/IP protocol concealed channel based on fuzzy neural network
A technology of fuzzy neural network and covert channel, which is applied in the field of information security and neural network, can solve problems such as no special method, and achieve simple, good scalability, and accurate detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
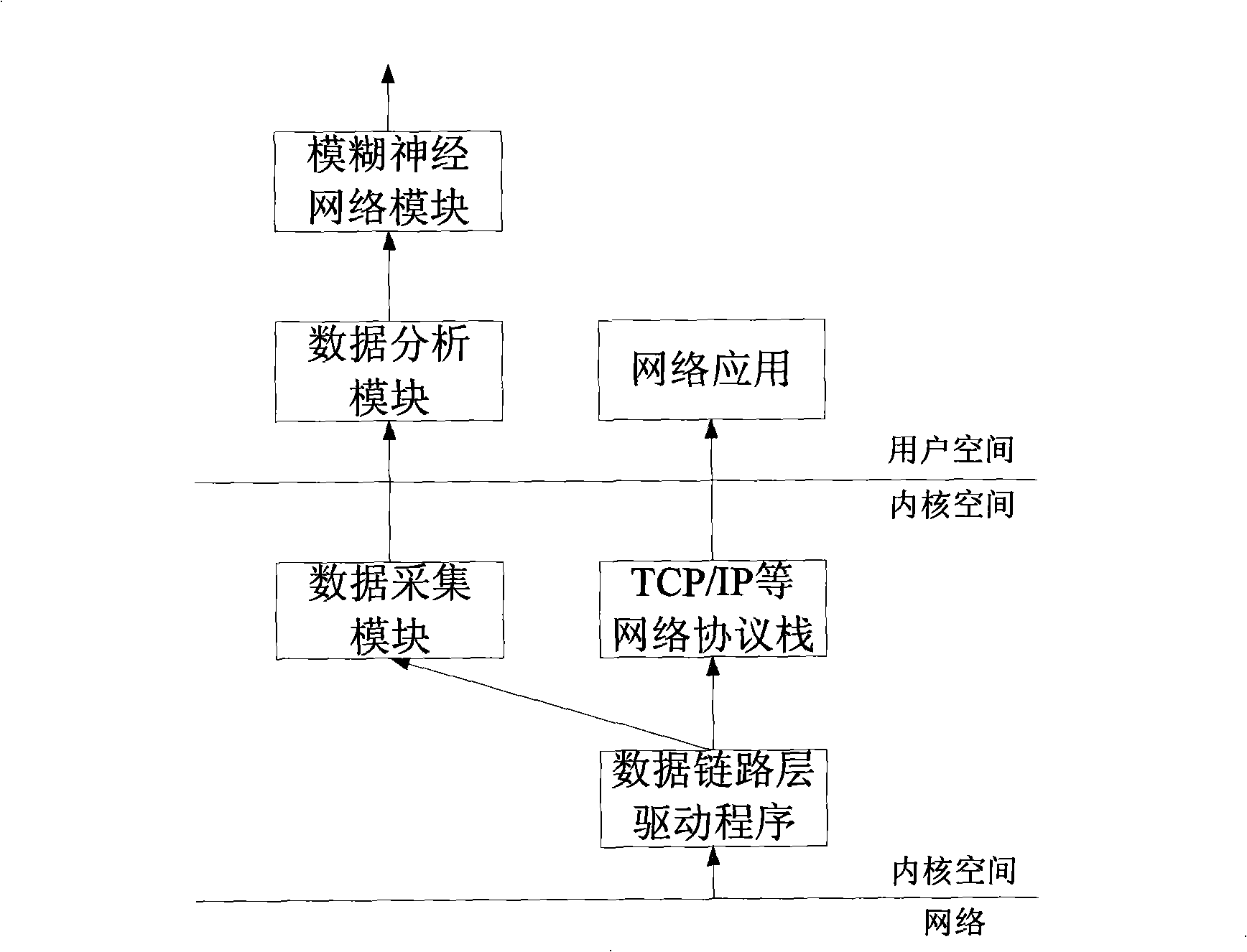
[0029] The TCP / IP protocol covert channel detection method based on fuzzy neural network comprises the following steps:
[0030] 1. Establish a filter, filter the data packets passing through the network interface according to the filtering rules, and capture the TCP / IP data packets output on the network interface;
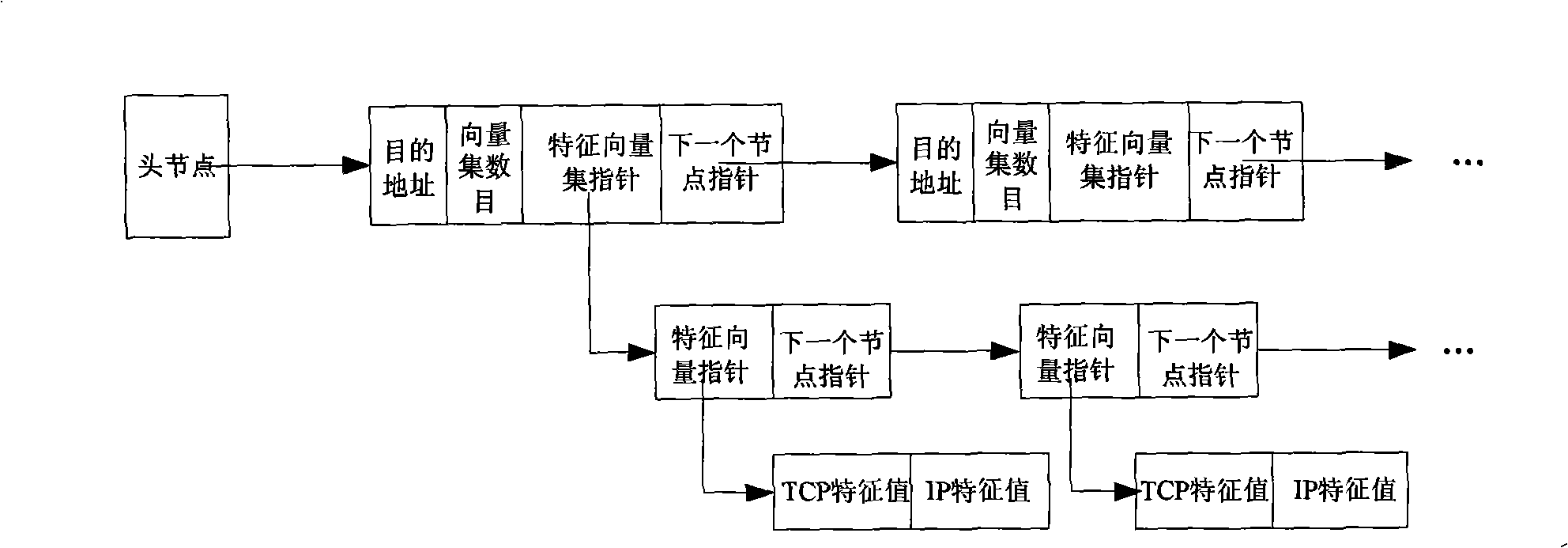
[0031] 2. Analyze the option field in the data packet header structure to form a feature vector, and then input the feature vector into the fuzzy neural network;
[0032] 3. The fuzzy neural network processes the feature vector, and finally performs fuzzy clustering on the output result, and judges whether there is a hidden channel through the output result.
[0033] The TCP / IP protocol packet output on the described capture network interface comprises the steps:
[0034] 1) Create a filter and pass the pointer of the data link layer packet to the filter;
[0035] (1) Create a filter. In order to speed up the filtering, the filter virtual machine method is used ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com