Information safety processing method and system, communication equipment
A security processing and information security technology, applied in the field of information security processing methods, information security processing systems, and communication equipment, can solve the problems of non-automatic startup, high cost, inconvenience, etc., to reduce management costs, prevent Trojan horse attacks, and ensure security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
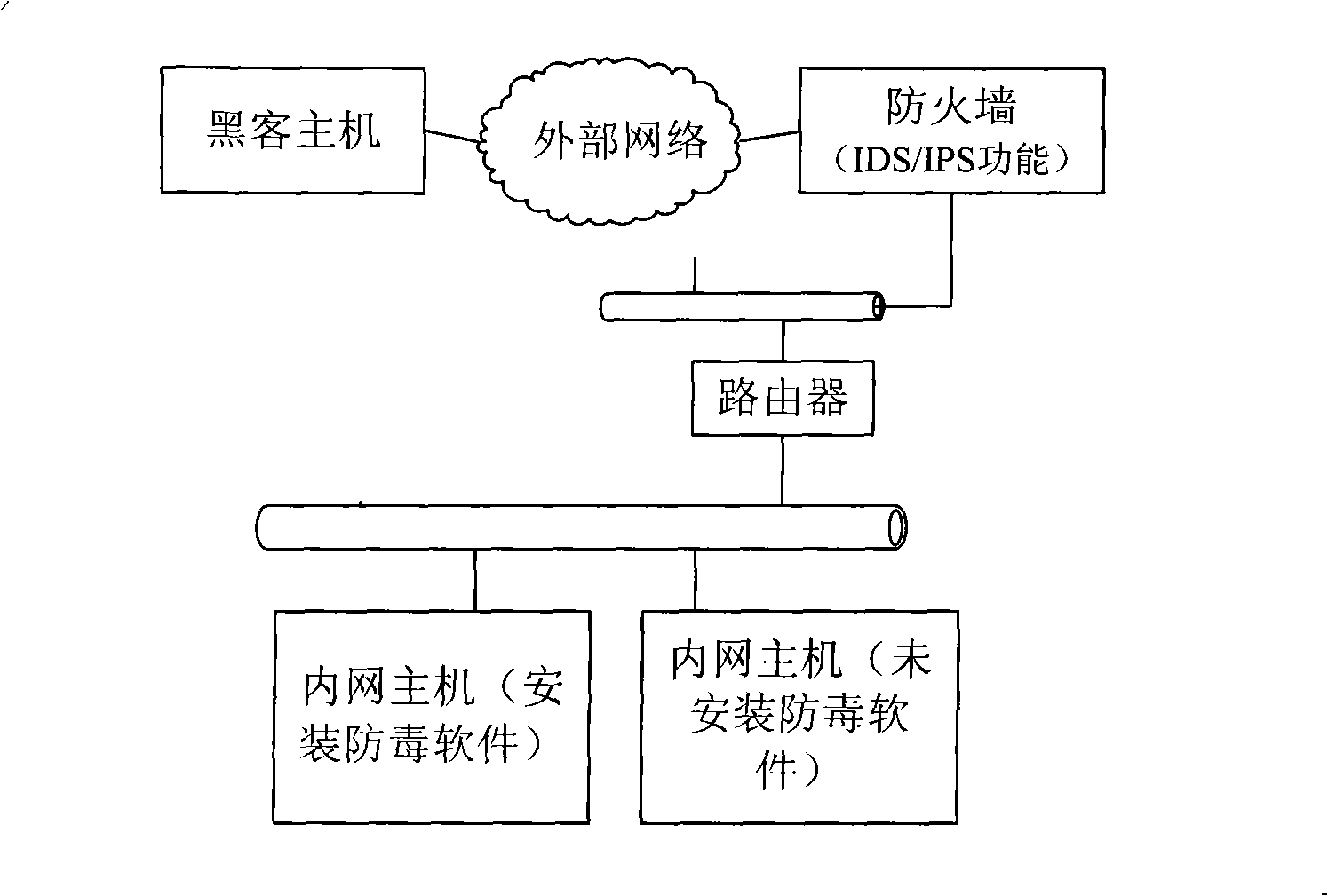
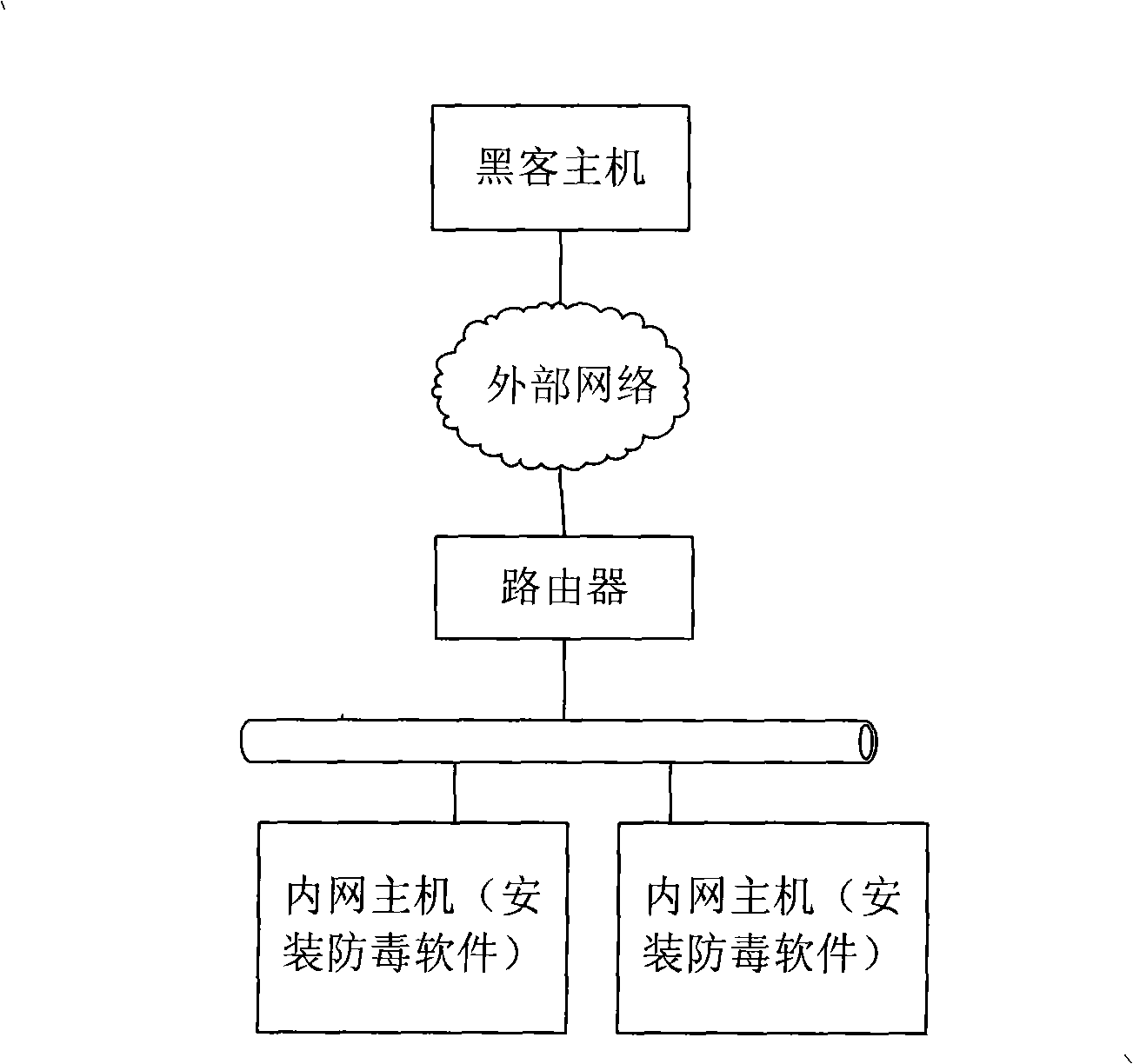
[0033]The present invention installs a server security processing module on the router, also known as: supplicant server (supplicant server, hereinafter referred to as: SUS), and installs a client security processing module on each intranet host, also known as: supplicant client Supplicant client (hereinafter referred to as: SUC), through the combination of SUC and SUS, performs Trojan horse protection on intranet hosts.
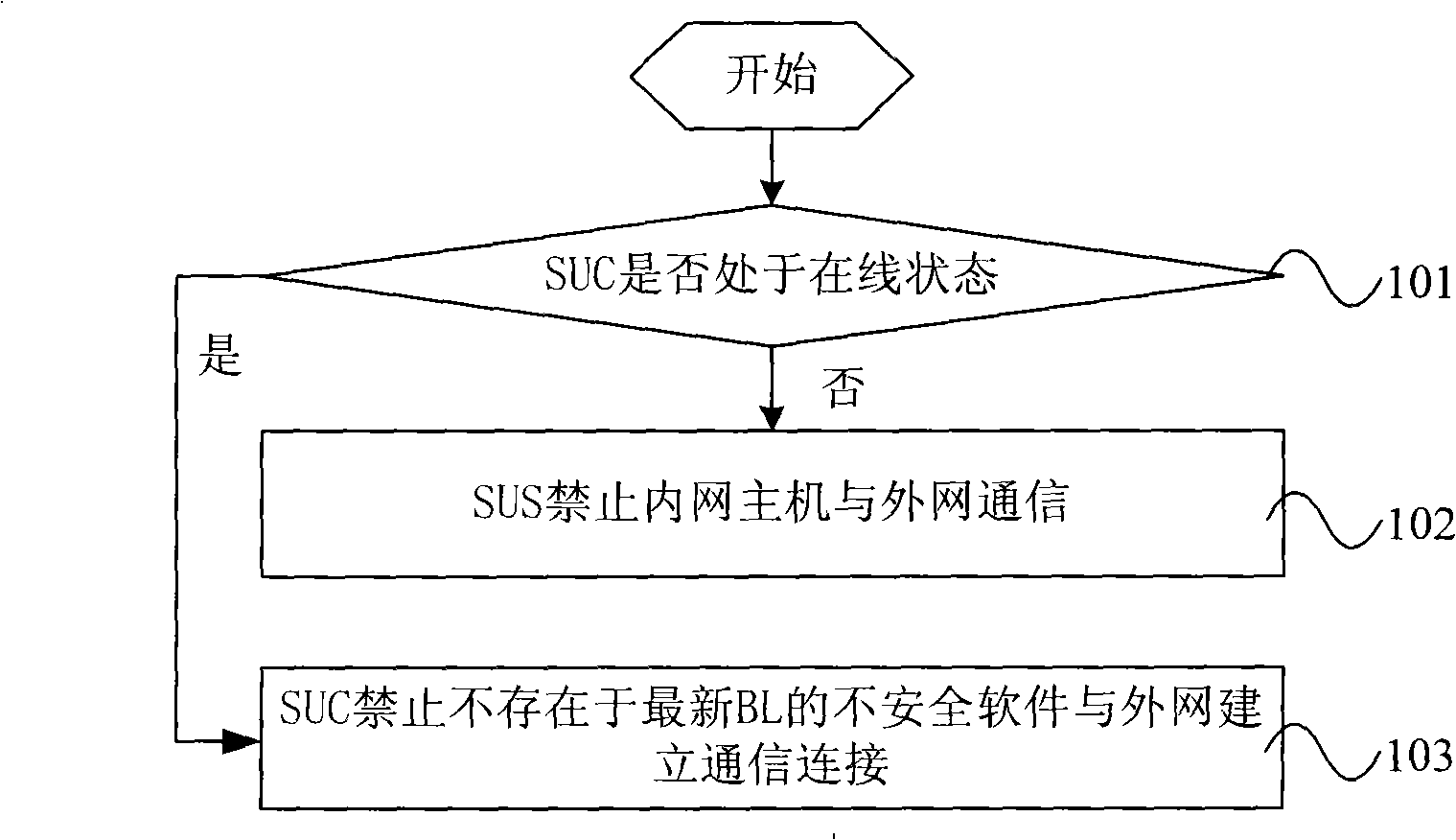
[0034] An information security processing method provided by an embodiment of the present invention includes:
[0035] The SUS judges whether the SUC used for security management of the intranet host is online; if the SUC is offline, the SUS prohibits the intranet host from communicating with the external network; The list library (backdoor library, hereinafter referred to as: BL), prohibits the insecure software that does not exist in the latest BL from establishing a communication connection with the external network, and the BL includes a list of files th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com