Method for activating a third party application safely, a third party server, terminal and system
A server and terminal technology, applied to terminals that securely activate third-party applications, systems that securely activate third-party applications, activate third-party applications, securely activate third-party applications, third-party servers, and securely activate third-party applications. It can solve the problems of privatization, the inefficiency of preset multiple card writing, and the inability of the server to complete the security domain key, so as to achieve the effect of easy management.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
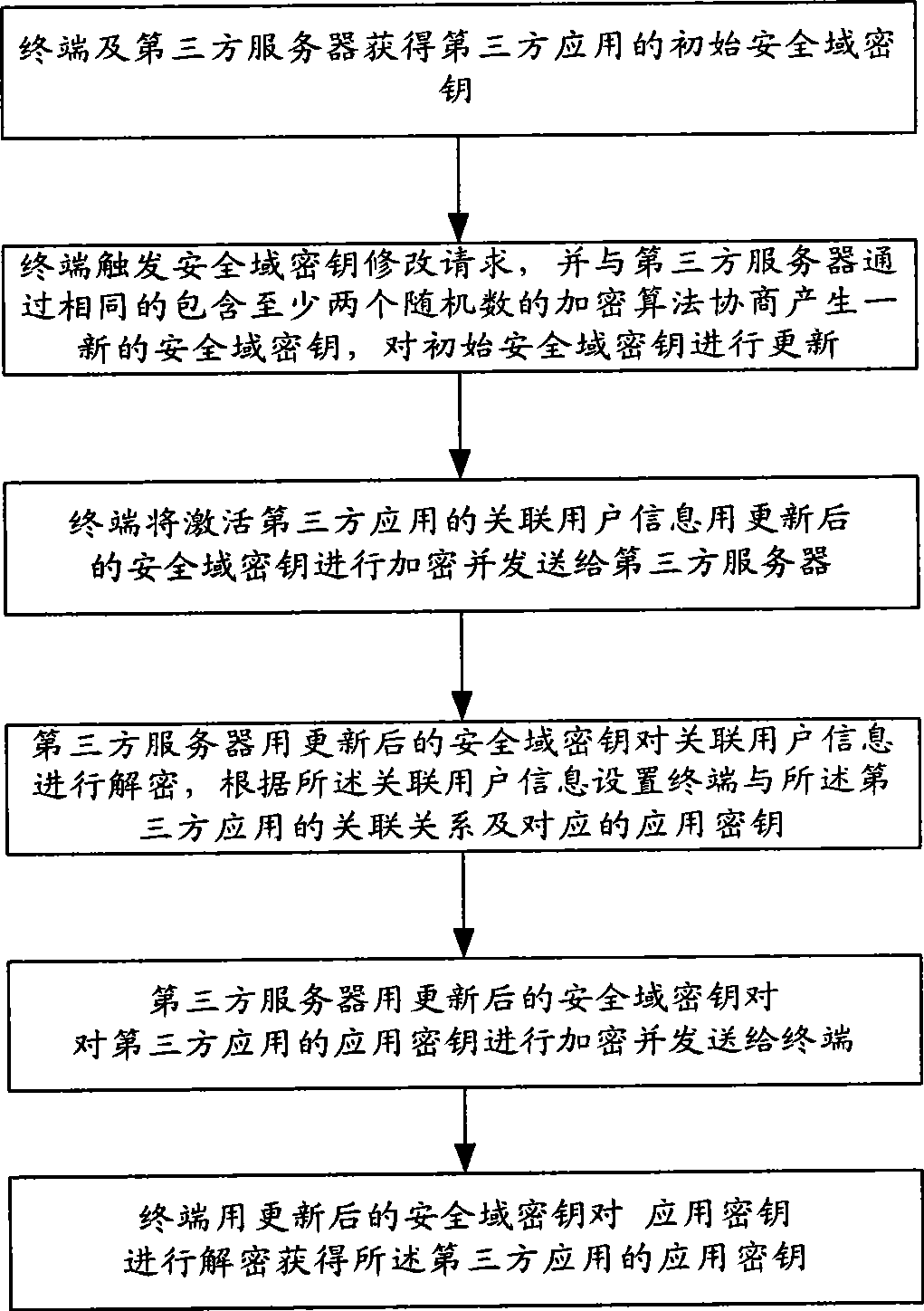
[0058] see figure 2 , is a flow chart of Embodiment 1 of a method for securely activating a third-party application in the present invention. Such as figure 2 As shown, this embodiment includes:
[0059] Step 1: the terminal and the third-party server obtain the initial security domain key of the third-party application;
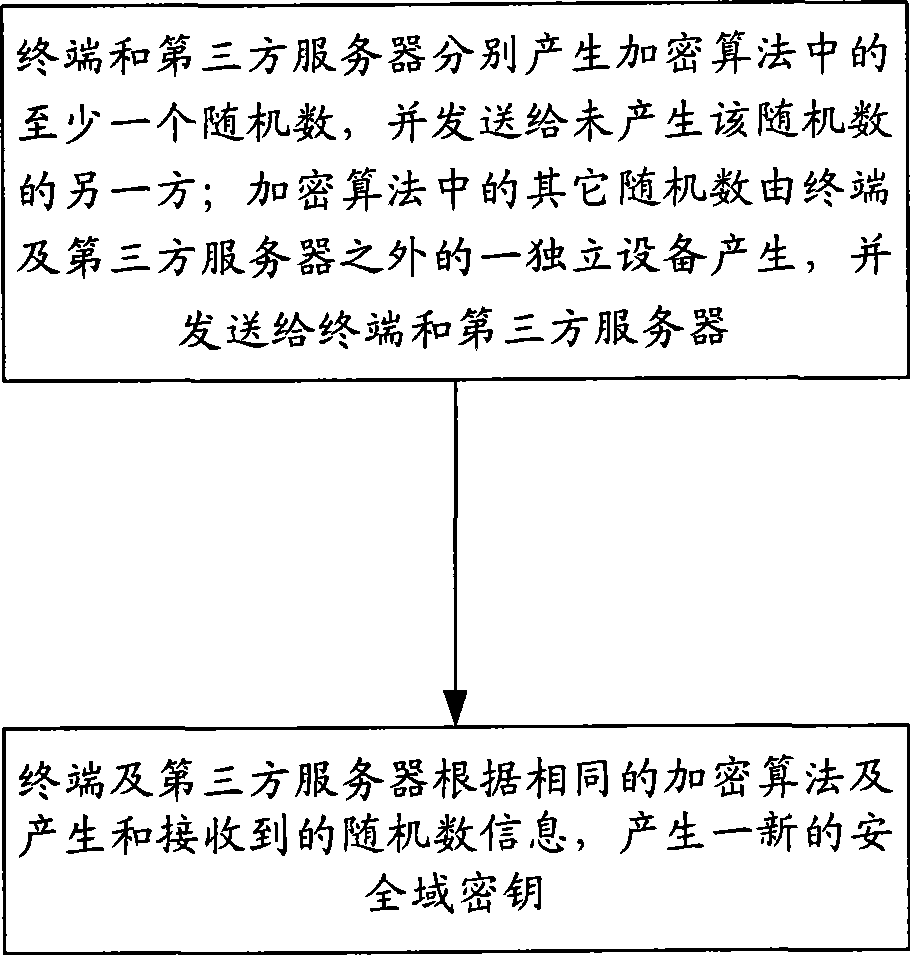
[0060] Step 2: The terminal triggers a security domain key modification request, and negotiates with the third-party server to generate a new security domain key through the same encryption algorithm containing at least two random numbers, and updates the initial security domain key;
[0061] Step 3: The terminal encrypts the associated user information for activating the third-party application with the updated security domain key and sends it to the third-party server;
[0062] Step 4: the third-party server decrypts the associated user information with the updated security domain key, and sets the association relationship between the terminal and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com