Method and system for implementing start-up protection
A technology for protecting programs and computers. It is applied in the field of information security and can solve problems such as security risks, password leakage, and no guarantee of the binding of physical and digital identities.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
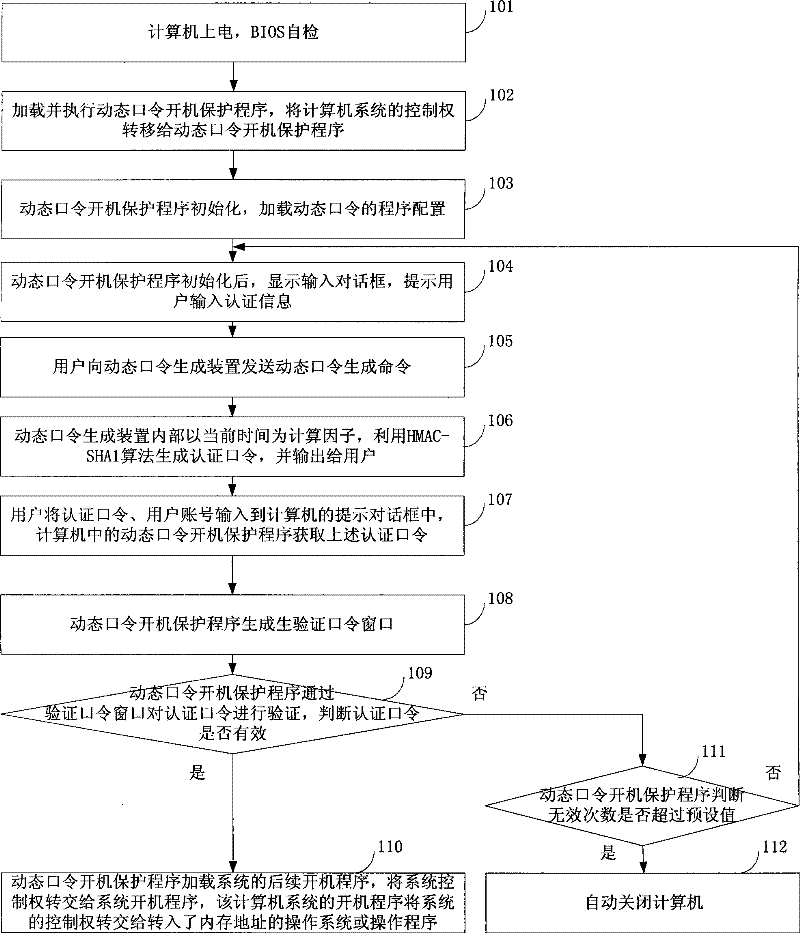
[0086] In this embodiment, the dynamic password power-on protection program can be placed in the BIOS program, as a part of the BIOS program, and can also be located in the master boot record of the computer boot hard disk. in,
[0087] If the dynamic password protection program is located in the BIOS, the dynamic password protection program is written into the preset position of the BIOS by the motherboard development tool of the computer;
[0088] If the dynamic password protection program is located in the master boot record, then write the dynamic password protection program into the position of the master boot record of the computer boot hard disk through the development tool of the computer, and keep the partition table information, for example, the 0 cylinder surface 0 magnetic head of the boot hard disk 1 sector and its subsequent sectors, etc.
[0089] Step 102, load and execute the dynamic password boot protection program after the BIOS self-check is successful, and...
Embodiment 2
[0139] The preprocessing module is used for powering on the computer, loading and executing the dynamic password protection program;
[0140] The receiving module is used to use the dynamic password protection program to receive the authentication password input by the user after the preprocessing module processes it;
[0141] Judging module, used for when the receiving module receives the authentication password, the dynamic password protection program judges whether the authentication password is valid;
[0142] The loading module is used to load the startup program of the computer into the dynamic password protection program after the judgment result of the judging module is that the authentication password is valid;
[0143] The processing module is used for when the judgment result of the judging module is that the authentication password is invalid, the dynamic password protection program does not load the boot program of the computer through the processing module;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com