Access authorization system, access control server, and business process execution system
An access control and business process technology, applied in transmission systems, digital transmission systems, instruments, etc., can solve the problems of longer user waiting time, higher processing load, longer time, etc., and achieve the effect of reducing waiting time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0100] First, a first embodiment of the present invention will be described.
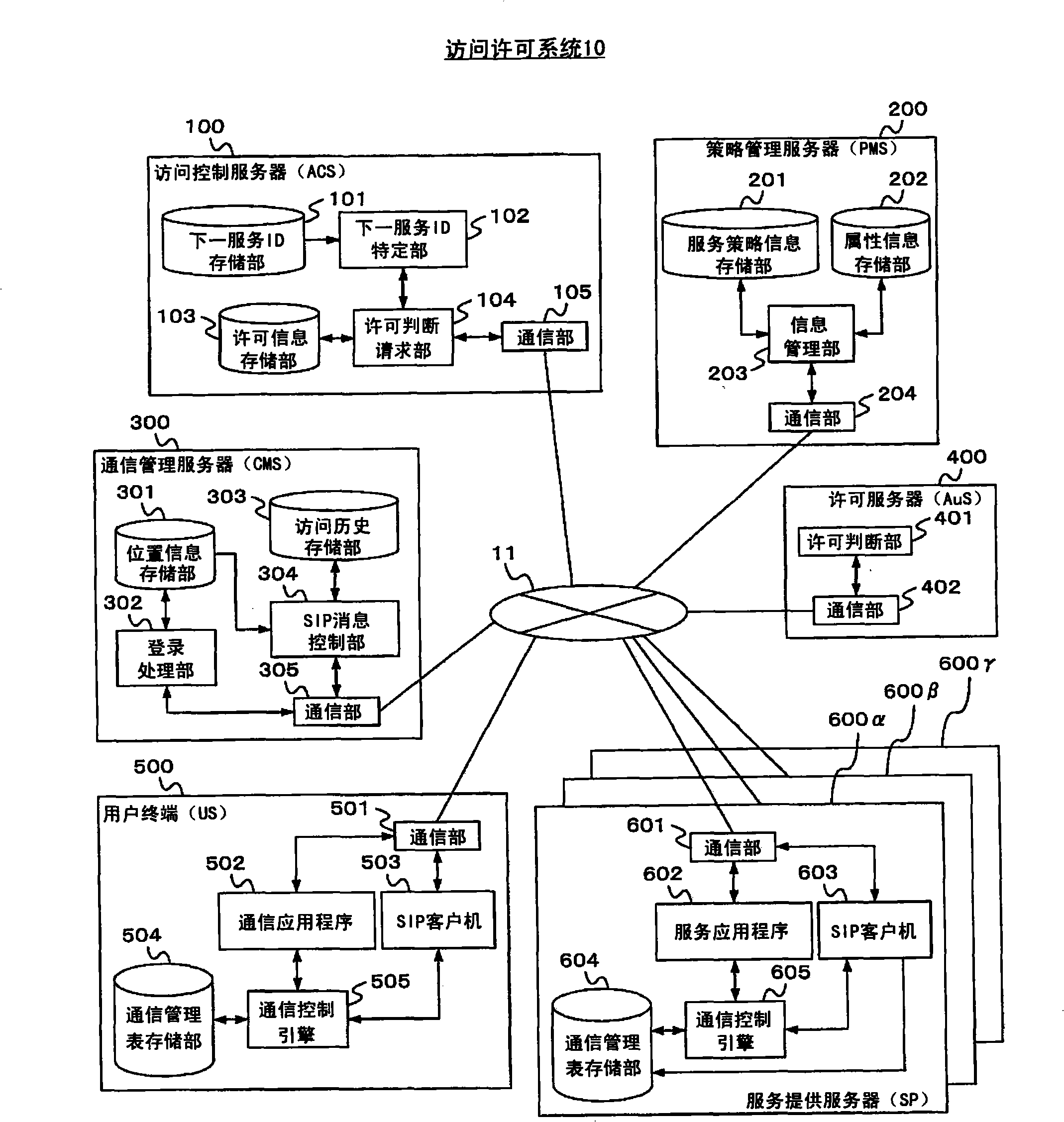
[0101] figure 1 is a system configuration diagram illustrating the configuration of the access permission system 10 in the first embodiment. The access permission system 10 includes an access control server (ACS) 100, a policy management server (PMS) 200, a communication management server (CMS) 300, an authorization server (AuS) 400, a user terminal (US) 500, and a plurality of service providing servers (SP )600. ACS100 , PMS200 , CMS300 , AuS400 , US500 , and SP600 communicate with each other via network 11 .
[0102] figure 1 In the access permission system 10 shown, when a user uses a service via US500, ACS100, which is a third party organization, cooperates with PMS200 and AuS400 to judge whether the user is permitted to use the service, and based on the result, CMS300 performs access control.
[0103] Next, functions possessed by each constituent element of the access permission system 10 i...
Embodiment 2
[0196] Next, a second embodiment of the present invention will be described.
[0197] Figure 15 It is a system configuration diagram illustrating the configuration of the access permission system 10 in the second embodiment. The access permission system 10 includes an access control server (ACS) 100, a policy management server (PMS) 200, a communication management server (CMS) 300, an authorization server (AuS) 400, a user terminal (US) 500, and a plurality of service providing servers (SP )600. In addition to the aspects described below, the Figure 15 neutralize figure 1 Structures appended with the same reference numbers are the same as figure 1 have the same structure or have the same function, so the description is omitted.
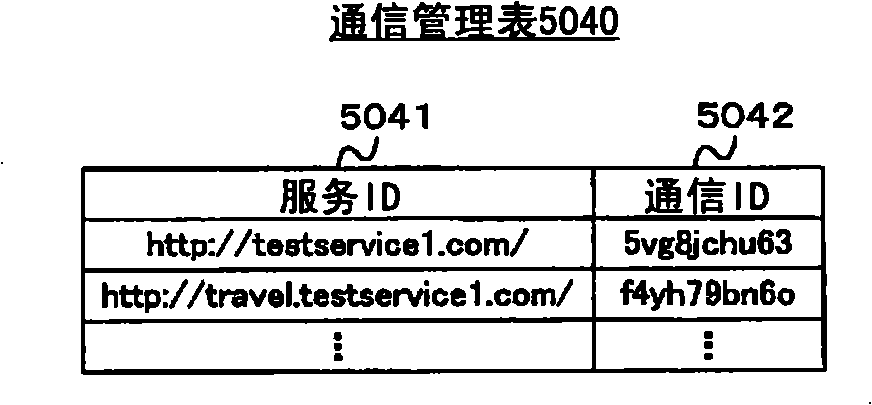
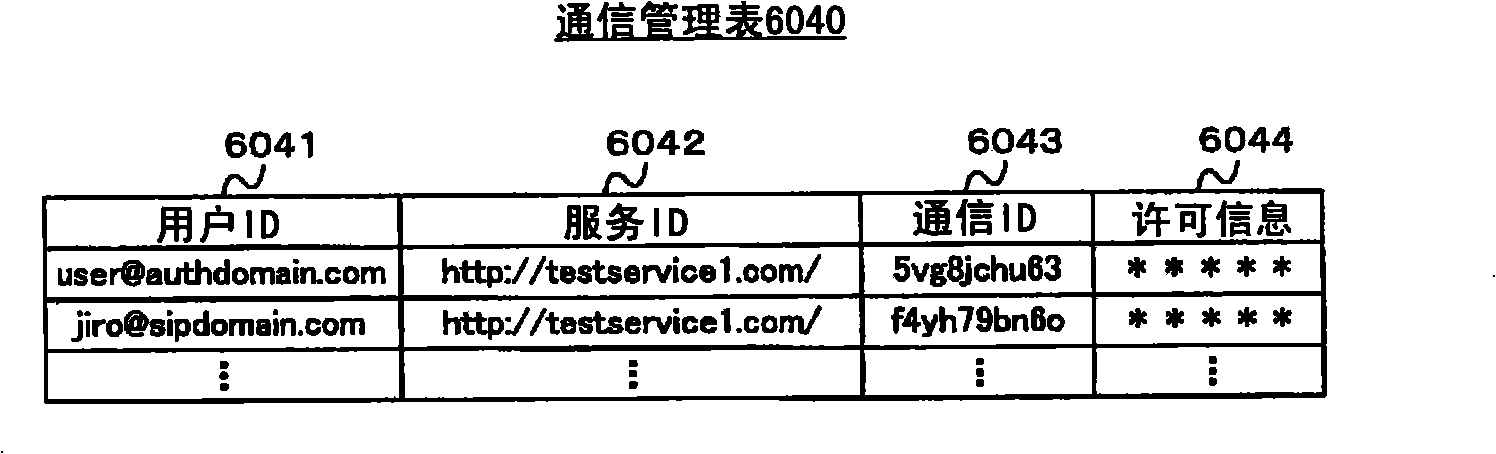
[0198] When the SIP client 603 of the SP600 receives a permission information transmission notification including the user ID, service ID and permission information from the ACS100, it registers the received information in the communication man...
Embodiment 3
[0237] Next, a third embodiment of the present invention will be described. The business process execution system 40 of this embodiment realizes one service by linking a plurality of Web services that implement access control through SAML according to a service script.
[0238] Figure 21 It is a system configuration diagram illustrating the configuration of the business process execution system 40 in the third embodiment. The business process execution system 40 includes a policy management server (PMS) 200, an authorization server (AuS) 400, a user terminal (US) 500, a plurality of service providing servers (SP) 600, a service execution server (SES) 700, and an attribute management server ( AS) 800.
[0239] Figure 21 The illustrated business process execution system 40, when a user uses a service script provided by SES 700 via US 500, makes a permission judgment in which SES 700 cooperates with AuS 400 to determine whether the user is permitted to provide each Web servi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com