Sensitive data switching control module and method for computer and movable memory device
A mobile storage device and sensitive data technology, applied in computer security devices, computing, digital data protection, etc., can solve the problems of poor security, lack of flexibility and practicability, and achieve the effect of strong practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
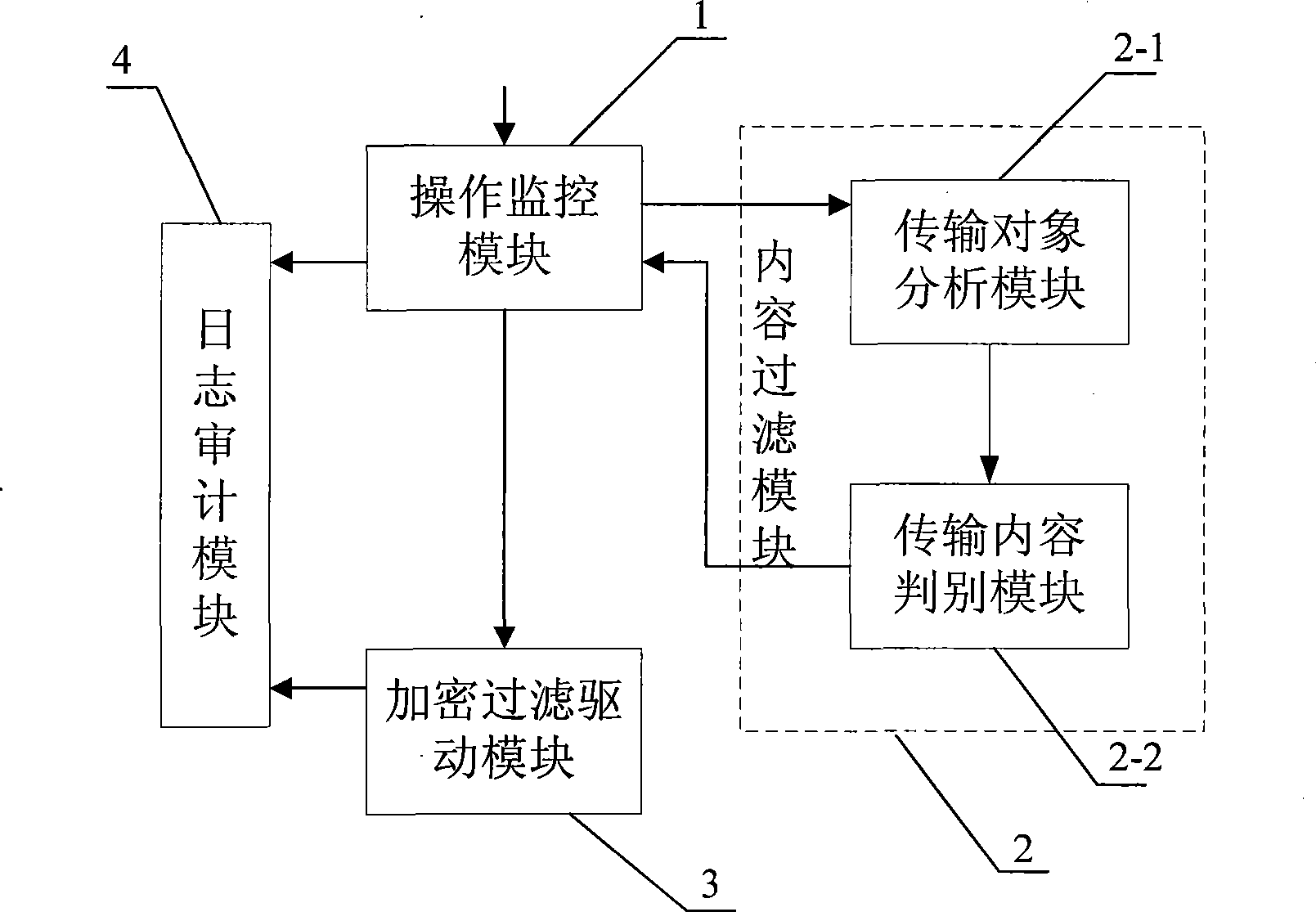
[0017] Specific implementation mode one: see figure 1 and figure 2 , the control module of this embodiment is made up of the following units:
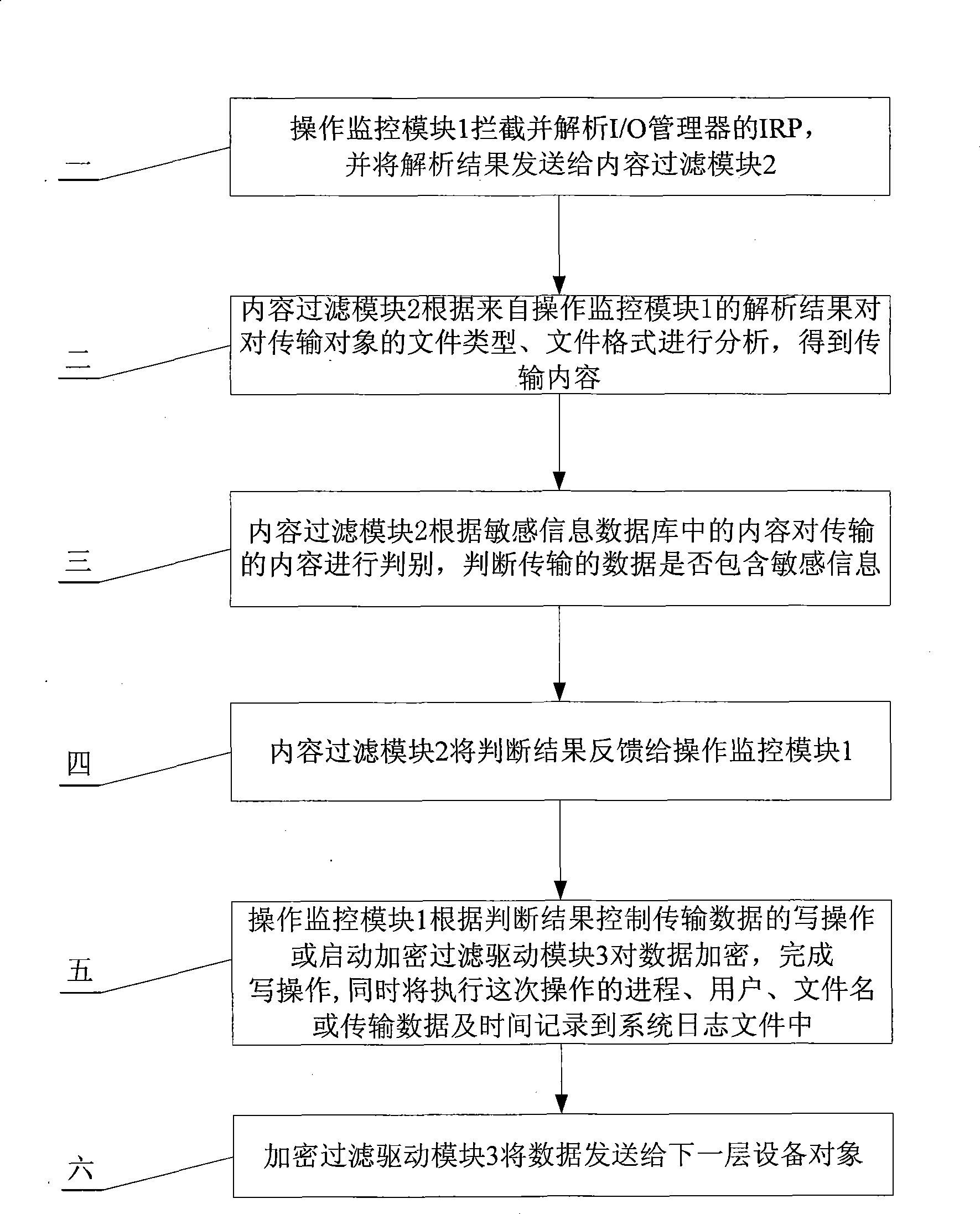
[0018] The operation monitoring module 1 is used to monitor the data transmission operation between the computer and the mobile storage device, and sends the transmission object (the transmission object may be a file or a part of the file) to the content filtering module 2, and judges according to the feedback of the content filtering module 2 The result is the control of the write operation on the transfer object;
[0019] The content filtering module 2 is used to analyze various attributes of the transmission object from the operation monitoring module 1: file type, file format, content, etc., judge whether the content of the transmission object contains sensitive information according to the sensitive data information database, and send the judgment result to the operation Monitoring module 1.
[0020] This embodiment is a data ...
specific Embodiment approach 2
[0022] Specific implementation mode two: see figure 1 , this embodiment further defines that the content filtering module 2 includes the following units on the basis of the first specific embodiment:
[0023] The transmission object analysis module 2-1 is used to analyze the transmission object provided by the operation monitoring module 1, obtain its file type, file format, and transmission content, and send the extracted content to the transmission content discrimination module 2-2;
[0024] The transmission content judging module 2-2 is used to judge whether the transmission content is sensitive content, and send the judging result to the operation monitoring module 1. There are two main types of content that can be processed, namely text file content and multimedia content such as images.
[0025] The transmission content discrimination module 2-2 judges the transmission content according to the sensitive information database, and the data in the sensitive information dat...
specific Embodiment approach 3
[0028] Specific implementation mode three: see figure 1 , this embodiment adds the following units on the basis of the specific embodiment one:
[0029] The encryption filter driver module 3 is used for performing real-time encryption or decryption on the transmission object based on the filter driver according to the judgment result of the content filter module 2 .
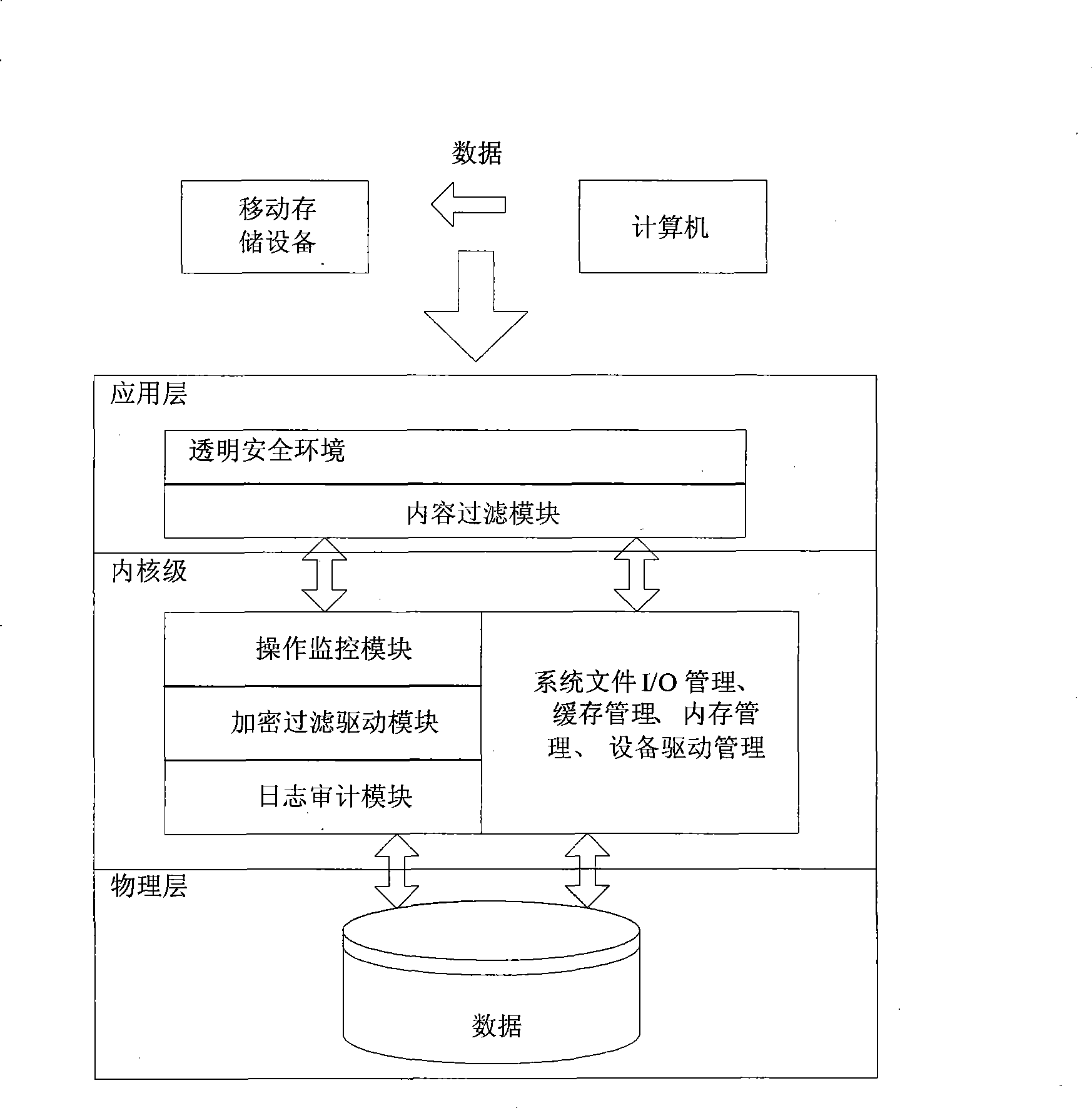
[0030] Encrypted filter driver is a data encryption technology in the operating system kernel and above the file system. It is a technology that uses the development of filter drivers to realize the function extension of the file system. It belongs to the kernel program of the operating system and is closely integrated with the file system to provide users with encryption / decryption services. Using the filter driver to implement file encryption and decryption is safe, because the filter driver belongs to the kernel program of the operating system, and the kernel mechanism provides a strong security guarantee and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com