Method for cryptographic authentication
A technology of cryptographic authentication and cryptographic algorithm, applied in the fields of digital data authentication, instruments, electrical digital data processing, etc., can solve problems such as inability to obtain solutions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
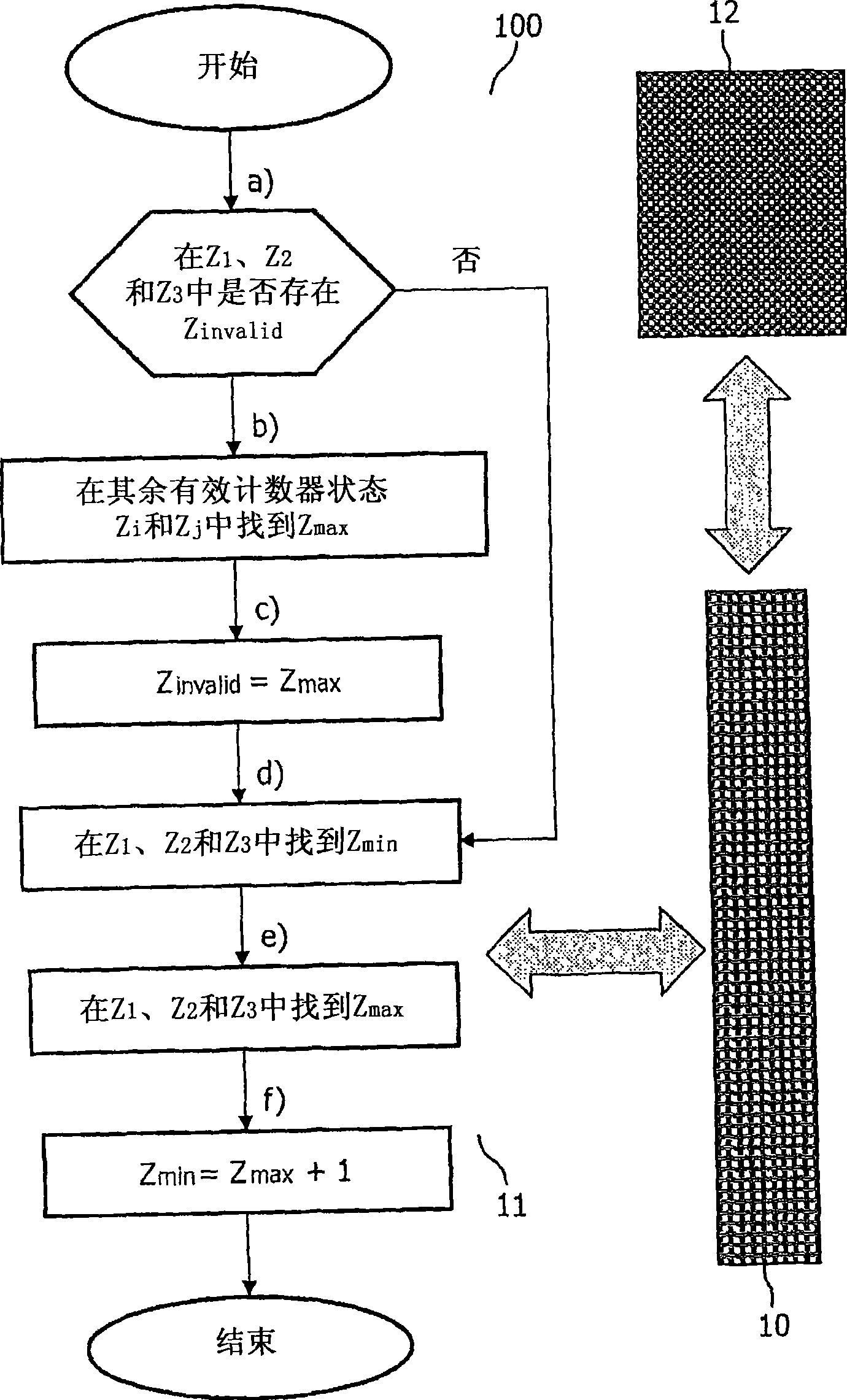
[0024] figure 1 shows a method 100 according to the present invention, wherein three EEPROM segments Z 1 ,Z 2 and Z 3 Used for safe storage of consecutive counts. The method 100 according to the invention represents the sequence of operations for securely counting and storing in the EEPROM 10 in the increment process 11 in which the increment process 11 is to be successfully implemented in the application, thereby subsequently entering the allowed access (Read, Write) Status of the EEPROM 10, ie access (ie read and write) is granted only if the INCREMENT command is executed successfully. In the first step a), one of the three EEPROM segments is searched for an invalid count Z valid , that is, make a query to determine if counting Z 1 ,Z 2 and Z 3 There is an invalid count Z in invalid . If such an invalid count Z does exist invalid , then in the next step b), if there are indeed invalid counts, then from the remaining valid counts Z i and Z j (i, j = 1, 2, 3) form ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com